Identosphere 115 • Funding for Threshold ECDSA KeySig • The Year of RSS • Most Relevant Interop Initiatives • SSI Meets WalletConnect
The new year came much quicker than expected. We never quite took that week off :D Did you? Welcome back for another year of decentralized ID, verifiable credential highlights!
Very Happy New Year from Identosphere - We Gather, You Read.
Contribute to our efforts by PayPal, or Patreon & we’ll keep aggregating industry infos, for the coming decade.
This should especially be the year of RSS for all of our readers and the organizations who subscribe to this newsletter! If you publish on decentralized ID, please be sure you have an RSS feed, and share it with us if not already included in the identosphere.net blogcatcher. This will be especially important in the future, as you will come to see. :D
Upcoming
Proposals for #Identiverse 2023 due 1/8
2023 OpenWallet Foundation Launch Event 1/17 @ Davos
Identity, Authentication and the Road Ahead: A Cybersecurity Policy Forum 1/25
GS1 Global Forum 2/13-16
APAC Digital Identity unConference 3/1-3 Bangkok, Thailand
Thoughtful Biometrics Workshop virtual unConference 3/13-17 [Registration]
Internet Identity Workshop 4/20, Mountain View, CA
User Experience
Better Onboarding with Verifiable Credentials Phil Windleys Technometria
Summary: Making onboarding easier would result in better customer experience, more customers, and reduced support costs. Last week a friend referred me to a question on Guru.com about devices for connected cars. Since I used to do Fuse, he figured I might be able to help. I was happy to. Unfortunately, Guru wasn't so happy to let me. You can't answer a question at Guru.com without registering
Why Social Media Needs Self Sovereign Identity Forbes
There is an inherent problem with how identity works in the digital age. In the current model, our “identity” is linked to a wide array of metadata that is controlled by a variety of tech companies. The user has little say or control over their own identity, as it is repeatedly treated as a commodity to be bought and sold.
Interop
[tweet] What was the most relevant Interoperability initiative of the year 2022 ? @psykoreactor
The #Plugfest for Learning and Employment Records (#LERs) by @jfftweets and @w3c_ccg VC EDU !
https://www.linkedin.com/pulse/plugfest-simone-ravaioli/
Self-Sovereign Identity meets WalletConnect. walt.id Submission for ETHLissbon 2022 walt.id (video)

The Inter-blockchain Communication protocol (IBC) is one of the world’s largest and most important interoperability protocols. As of today, IBC has connected more than 40 chains and, in the last 30 days, processed more than 12M unique transactions. This makes IBC by far the largest interoperability protocol by almost any measure.
With funding from Interchain Foundation, Datachain has contributed to the Cosmos/IBC community with the goal of increasing the number of blockchains communicating with IBC. The focus of Datachain has been mainly on implementing IBC modules for various chains such as Hyperledger Fabric, Hyperledger Besu (Enterprise Ethereum) and Corda.
IBC Use Cases in the Enterprise Space are Coming Interchain 4/19/22
time travel they wrote previous post the next day!! But ferreal for BSN too!?!!
as discussed in our previous post. The Inter-Blockchain Communication (IBC) protocol is not only for chains built on the Interchain Stack, but for all blockchains, regardless of app building framework, including enterprise (permissioned) blockchains and probabilistic finality chains.
This post is the second part of the IBC and enterprise series and will dive into enterprise use cases in production using the IBC protocol, specifically:
Delivery Versus Payment (DVP) Settlements between digital assets and digital currency (NTT DATA)
USDF, a USD-pegged Stable Coin (USDF Consortium)
Enterprise Blockchain Platform BSN (Bianjie) backed by the Chinese Government
Atomic Swap Between Digital Currencies (Soramitsu)
Development
Azure AD Multi tenant Azure App registration consent Damien Bod
This article looks at Azure Active directory and consent with multi-tenant Azure App registrations. Consent works different depending on the user type, the tenant policies and the required permissions. It is sometimes hard to understand why a user cannot login or where the consent has to be given
[code] Verifiable Credentials Resonate Coop 02/2021
This is Resonate's reference implementation of the Verifiable Credentials Data Model ("VC"). It is intended to explain the theory of our implementation (our "VC Architecture") and provide a working example.
DID MEME Orie Steele
*we got this to work but only dragging the image from the page, not downloaded
DID Meme Updates: Using a Joke Project to Experiment with Decentralized Identifiers Inside of Images As open source community leaders, Transmute is committed to fostering an environment where cutting edge problem sets and ideas are vetted and improved by expert peers. In that spirit, Transmute routinely publishes articles directly from our staff, who are experts across technology and industr
Funding
Chain-Key Signatures — Threshold ECDSA DFinity (ICP) source
Threshold ECDSA (tECDSA) allows canisters to issue W3C Verifiable Credentials that can be verified using standard libraries by relying parties even outside the Internet Computer, i.e. by standard web services or even mobile apps. We just released a Grant RFP that mentions this use case. Furthermore, it should be possible to define a DID method or just a verification method that supports canister signatures. This would allow issuing Verifiable Credentials even without using tECDSA.
Adoption
LACChain Case Study Hyperledger Foundation
More than 101 entities on the network since its launch
As of August, 2022, 191 nodes deployed
More than 60 projects on LACChain Network
Over 40 projects with impact on inclusion
15 countries co-building ecosystems
VU adds digital identity expert to evolve cybersecurity PRNewswire
BUENOS AIRES, Dec. 16, 2022 VU inc, a global cybersecurity company that protects more than 350 million users around the world, has added digital identity and authentication expert Stephen Maloney, an experienced industry veteran with a history of building successful technology companies, as Senior Strategic Advisor.
Looking Forward
[tweet] 3-word aliases for ION DIDs should arrive by May csuwildcat
which means you can have IDs like: did:ion:big-red-car, did:ion:daniel-12345, etc., that securely map to multiple keys and routing endpoints you can roll. Can't do that with just keys, folks
This is the year of the RSS reader. (Really!) Ben Werdmüller
“I predict that these people won’t stand for a universe where their email becomes ever more crowded just because of Elon Musk mucking up Twitter. The only way to survive in a world where multiple DC-insider publications are launching multiple newsletters and Twitter is no longer socially acceptable is to use an RSS reader that satisfies the intelligentsia and political elite.”
How Developers Will Work In 2023 auth0
Queryable encryption, WASM goes mainstream, and a tighter job market
Crypto Thesis for 2023, Ryan Selkis bankless
I have written this year-end piece for the sixth year in a row because I see light at the end of the tunnel. I hope this report provides a clean mental model for you to refer back to throughout the year ahead. We cover all of the top investment themes, people to watch, policy developments, and technical breakthroughs that we expect will shape crypto in 2023. Onward.
Everything Will be Tokenized: The Future of Identity Identiverse: Katrina Dow, Meeco
this tokenized world to emerge, we first need the infrastructure for people and their digital twins to participate. This will include a trusted digital identity and the means to be verified, present credentials, transact and pay.
IOT
When Things Know What They Are: IoT in the Age of Self-Sovereign Identity ITN Trust
Note that wherever the SSDT is located in the cloud, only one entity controls it through the ownership certificate it was given by the previous owner and the registration of the owner’s keys in the DID document of the camera as the camera’s controller. All the information presented by the SSDT based on the digital certificates it holds is considered verifiable, immutable, and cannot be repudiated — i.e., trustworthy.
In our next blog, we will look at the significance of this example in the context of DIDs, or unique global identifiers.
> Read “The Digital Business Trilemma, Zero Trust, and the ITN.”
KYC
Improving KYC Processes using Self-Sovereign Identity hira.siddiqui
Overall, the integration of self-sovereign identity and KYC can help to create a more secure, transparent, and efficient financial system. By using blockchain to facilitate the verification of identity and risk assessment, businesses can streamline their processes and improve the accuracy of their risk assessment efforts
KYC-Chain’s New Features and Upgrades KYC Chain
As we head towards the end of the year, at KYC-Chain we've been accelerating our new feature releases and upgrades, bringing a powerful new suite of tools to our onboarding platform. Let's take a look at what they are. The post Preparing for the Compliance Challenges of 2023: KYC-Chain’s New Features and Upgrades appeared first on KYC-Chain.
Education & Employment
A shout-out to the thousands of builders and innovators engaged in building the Internet of Careers. Velocity Network
A shout-out to the thousands of builders and innovators engaged in building the Internet of Careers®. Happy Holidays and a prosperous New Year to you, with sincere thoughts and best wishes from Velocity Network Foundation®. The post A shout-out to the thousands of builders and innovators engaged in building the Internet of Careers®. appeared first on Velocity.
The Future of Employment Verification Indicio
Employees would connect to the Issuer, receive the credentials, and store the credentials in an Aries-compatible agent application such as Holdr+. Various departments and systems within the company or from its partners would request credentials from the employees, who would review the requests and consent (or decline) to share the data from their agent application.
How Learning and Employment Records Shape Access to Quality Education and Jobs Annelies Goger, Allyson Parco, Rohan Carter-Rau, Jessa Henderson, Kazumi Homma, Ani Meliksetyan, and Natalie Milman
In this report, we share key findings from our research on digital credentials and LERs and present three detailed case studies of initiatives to govern and implement digital and microcredentials with the goal of achieving the fourth United Nations Sustainable Development Goal7 (SDG 4): equitable access to quality education and lifelong learning.
Retrospective
A Season of Pinging Ping Identity
Ping Identity employees collaborated their services over the holiday season, with five offices worldwide taking part in our “Season of Pinging,” a global initiative to give back to our local communities during a challenging time of the year.
Where Self Sovereign Identity (SSI) is now Milan Bzovyi
As before, standardization and implementation methods are still being studied by different organizations, research is being conducted, and only a few of them are in full use. However, the importance of SSI is gradually growing in Europe, where the consistency between SSI and eIDAS is being evaluated and discussed, and in Japan, where the issue is being discussed by the Digital Market Competition Council, which is one of the policy councils.
E18 - 2022 Year in Review Quiz This week in identity
Favourite conference of 2022
Favourite identity buzz word
IAM acronym / topic that will die in 2023
Biggest IAM surprise in 2022
Most interesting IAM startup / category
IAM acronym / topic that will come alive in 2023
The CAI’s 2022 Year in Review Content Authenticity Initiative, Coleen Jose
The urgency to address mis- and disinformation, facilitate transparency and creator attribution online has become even more critical with the speed of developments in generative artificial intelligence.
2022 in Review and What's Next for Fission Fission
2022 was an exciting year at Fission. We continued to build out our signature edge app developer toolkit, Webnative SDK, and laid the foundation for our database and virtual machine. We celebrated several research breakthroughs and grew our company's presence and team.
After LastPass breach Cyberforge, Anil John
Why 1Password or Bitwarden as alternatives … a good number of people questioned why I recommend ditching LastPass and expressed concern with me recommending people jump ship simply because they suffered a breach. Even more are questioning why I recommend Bitwarden and 1Password, what advantages they hold over LastPass
Web 3
22 Top Crypto Pieces From 2022 a16z
…top resources
…top podcasts
…top code releases
…top op-eds
…top code releases
…plus top research pieces
…and top videos
IOTA recommended in "German blockchain report" for innovative technology on identity management Crypto News Flash
The report notes: “The robust ecosystem in the German capital, which creates important synergies between decision-makers, investors, startups, and SMEs, provides the ideal framework for the blockchain community to flourish. Among them are important players like the Ethereum Foundation, the IOTA foundation, and Ocean Protocol.”
Decentralized identity described on Ethereum.org
In the context of decentralized identity, attestations (also known as Verifiable Credentials) are tamper-proof, cryptographically verifiable claims made by the issuer. Every attestation or Verifiable Credential an entity (e.g., an organization) issues is associated with their DID.
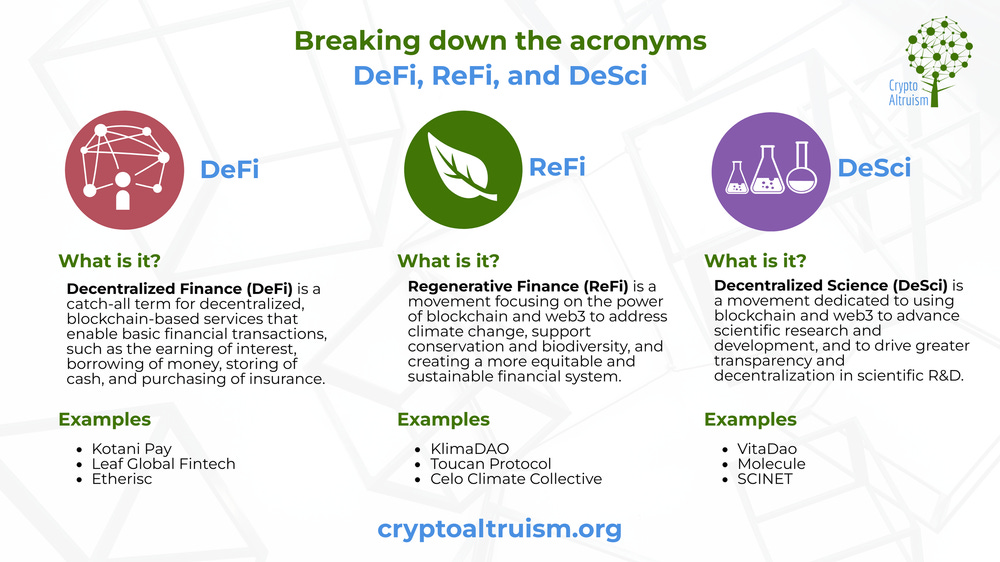
INFOGRAPHIC: DeFi, ReFi, and DeSci - Breaking down the acronyms Crypto Altruism
Thanks for Reading - Happy New Year!
Read more \ Subscribe: newsletter.identosphere.net
Contact \ Submission: newsletter [at] identosphere [dot] net