Identosphere 126: How Do Humans Trust? • Tokenization: Security + Exceptional UX • municipalities may need their own • Updates to Trinsic v1 and Sovrin StagingNet
A weekly digest on self sovereign identity: upcoming events, company news, policy, organizational updates, standards development and more... For Over 2 Years!!! Thanks for supporting us on Patreon!!!
Identosphere’s Weekly Highlights:
We Gather, You Read!
Contribute to Identosphere by PayPal, or Patreon! We’ll keep aggregating industry info.
Upcoming PreIIW
Announcing Interaction Patterns Task Force ToIP - 2nd & 3rd Thursdays [Calendar]
London Event: MEF CONNECTS Personal Data & Identity May 25 Identity Praxis, Inc.
New unConference for the Fediverse and future of social media: FediForum Johannes Ernst, Kaliya, Jennifer Holmes 3/29-30 (fediforum.org)
[Pre-IIW] OpenID Foundation Workshop at Microsoft 4/17
Internet Identity Workshop 4/18-20, Mountain View, CA
MeetUp Holland FinTech: The Future of Banking Innopay 4/13 Rabobank, Utrecht, The Netherlands
eIDAS 2.0 l New Opportunities in Digital Identity INNOPAY 4/27
Heroes of Data Privacy – the practise-oriented data privacy conference in Vienna LionsGate 5/24 Vienna, Austria
Digital Identity unConference Europe 6/7-9 Zurich ← Registration open
Company Stories
Key Takeaways from a Conversation with Phil Windley on “Learning Digital Identity” Indicio
While his new book, “Learning Digital Identity,” is mostly geared toward a business and technical audience, it is replete with important insights for how we all should think about digital identity
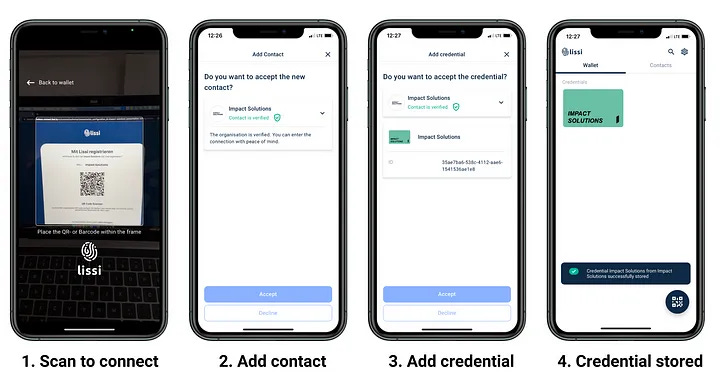
IMPACT SOLUTIONS platform integrates login with the Lissi Wallet Lissi
IMPACT SOLUTIONS is an innovative marketplace through which, companies from all sectors can find tested solutions for their sustainable transformation
200+ participants, 66 prototypes submitted, and 6 winners Affinidi
Affinidi India team members have emerged as 2 of the 6 winning teams of the Skill-A-Thon 1.0, a hackathon aimed at promoting skills discovery and education opportunities in India
Tech
[Recap] Kiva Protocol
To accomplish this, our team became significant contributors in the open-source communities developing the code bases and open standards on which Protocol was built, including Hyperledger Indy, Aries, and Ursa; the Trust Over IP Foundation; the W3C, and more. During the lifespan of Kiva Protocol, the open-source community we participated in grew from about 40 contributors to 1000s. The tech from that community is being used for government digital identity work in Canada, Germany, Finland and elsewhere.
Do you have Cryptographic Agility? Entrust
What attributes would hinder an organization’s cryptographic agility?
Important Updates to Trinsic v1 and Sovrin StagingNet Trinsic
For non-production testing, development, or prototyping work, we recommend Indicio TestNet.
For production credentials and verification, we recommend continuing to use Sovrin MainNet.
Tokenization: Enabling the Intersection of Data Security and Exceptional User Experiences Entrust
Tokenization doesn’t obfuscate data; it removes it from the interaction entirely. It replaces sensitive data with a token that represents the financial card data. If it’s stolen, it’s worthless to a hacker
The Road to Identity-First Security: Identity Data & Observability Radiant Logic
By using a combination of attribute and schema changes with time-series analysis, an observer can interpret the health of datasets and pipelines, identifying risk areas that undermine policy engine execution
Microsoft
[video] Introduction to Microsoft Entra Verified ID Core Concepts and Use Cases Tech Mind Factory
This video introduces Decentralized Identity and Verifiable Credentials concepts. It presents how Microsoft Entra Verified ID works and how it is built on top of industry standards for Verifiable Credentials.
Use Azure AD Access Packages to onboard users in an Azure DevOps project Damien Bod
This post looks at onboarding users into an Azure DevOps team or project using Azure AD access packages.
Literature
3 key insights from the Entrust Cybersecurity Institute’s “Future of Identity” Entrust [Report]
We surveyed 1,450 consumers globally to understand how they feel about emerging identity topics
How Do Humans Trust? ToIP
The Trust Over IP Design Principles identified the following human trust principles as headings in this essay. The principles create the fabric in which we make decisions to trust something or someone.
How is Self-Sovereign Data different from Blockchain technologies? Hub of All Things
what if, instead of decentralising data from the central data processing system we decentralise the data processing system itself?
The market for self-sovereign data - WRAP: Warwick Research Archive Portal
Decentralised Data Processing: Personal Data Stores and the GDPR
Use Case Explainers
The Business Benefits of Digital Onboarding KYC Chain
With automated KYC solutions integrated into their digital onboarding process, businesses can easily compare customer data against multiple reliable sources in order to obtain accurate results.
Virtual Onboarding with MS Entra Verified ID IDRamp
How can businesses improve protection against insider threats and simplify the verification onboarding process at the same time?
Micro-Credentials: Building Blocks for 21st Century Digital Education DigitalScot
As FutureLearn describes a Micro-credential is a “Certification of learning that can accumulate into a larger credential or degree, be part of a portfolio that demonstrates individuals’ proof of learning, or have a value in itself.”
Travel
[real world] Partnerships for Pangiam, SITA and Embross to ease travel processes Indicio, via Biometric Update
“What we’ve done is built a way to translate the trustworthiness of a passport into an equally trustworthy ICAO DTC type 1 digital credential – all without needing to store any personal data about the passenger outside the credential.”
How Self-Sovereign Identity Can Revolutionise the Travel Industry Zaisan
Travellers control their own personal information
Travel companies do not have to worry about storing sensitive personal data
The travel process is more streamlined
Identity can be verified more efficiently and securely
Policy \ Public Sector
[podcast] Digital ID in Local Municipalities w Henk Marsman, SonicBee ubisecure
why local municipalities may need their own digital identity schemes – including how these local schemes differ from national schemes and how they help people missed by national schemes, alongside some examples of live local identity schemes.
[UK Regulation] UK Data Protection – What Is Changing Kuppinger Kole
It provides greater clarity about what is personal data and the reasonable steps that a data control needs to take to decide whether data could identify a living individual.
Standards Work
[explainer] Verifiable Credentials – the Killer Feature of Decentralized Identity Dr Paul Ashley, Anonyome Labs
VCs are what will make decentralized identity ubiquitous on the internet in the next decade.
[explainer] Selective Disclosure Guide: Privacy Feature of Verifiable Credentials Dock
Review of Proposed Submission of Code List Representation (genericode) V1.0 to ISO/IEC JTC 1 Oasis Open - ends 4/16
Code List Representation (genericode) V1.0 was approved as an OASIS Standard on 31 January 2023
Data Protection
Is there any demand for personal data stores? MyDex
“But there is no demand for personal data stores!”. This is especially the case with policy makers and investors. We think they’re wrong and this blog explains why.
[video] Bringing Data Back Under Control Kuppinger Cole
KuppingerCole Analysts and data security firm ShardSecure discuss data confidentiality in the context of modern infrastructures, quantum computing, and data protection regulations. They will also discuss data resilience
EID And SSI Technology: Privacy Risks And Discrimination Against Citizens? Tangle Labs
Very good In Depth artice
Critics present very valid arguments against the widespread introduction of this technology in society. At this point, I will address these points
Web3
Why Global Trade Needs the Blockchain Vinay Gupta
Computers worldwide cannot all agree on what is true due to the speed of light, which creates a significant delay that affects things like global finance
Lobbying Group Hunts For Proof That Feds Are Targeting Crypto Defiant
Blockchain Association Requests Information From US Banking Regulators
Aztec To Sunset Privacy Protocol Defiant
Over 100,000 Wallets Have Used Aztec Connect [...] Aztec also open-sourced the entire codebase for Connect and encouraged community members to fork, deploy, or develop a new version of the rollup. “We’d love to see an independently-operated Aztec Connect and are ready to fund it,” it said.
Pioneering the Metaverse in Scotland Digital Scotland
Showcasing the Scottish innovators pioneering the most significant evolution of technology in history.
Web3 ID
Verida One Preview: Usernames for your Decentralized Identities Verida
Filecoin Launches Ethereum-compatible Smart Contracts Defiant - “Update Enables DeFi, ‘Data DAOs’ and Perpetual Storage”
Worldcoin says SDK lets you prove you’re a human online. Coins not included Biometric Update - “The protocol and World ID do not prove who a person is”
Civic Now Offers Support for Ethereum & Polygon Civic - “Our integrated token-gating tool helps dApps gate access to their services by issuing a Civic Pass to their users, which may be used across chains and wallets.”
Unlocking the Power of NFTs with KILT’s Public Credentials -“KILT announced its first use case for public credentials with Public Pressure who will use KILT to verify NFTs on their Marketplace collections.”
Web3 Studios predicts digital identity, particularly self-sovereign identity (SSI), could generate $600bn+ by 2030 Sinegy
SSI allows users to control their data, enabling decentralization and data privacy in Web 3.0.
ID Not SSI
Leaked passwords exceeded 721M in 2022 SC Media “Threat actors have exposed 721.5 million credentials online last year, many of which had been exfiltrated from malware-infected third-party business apps, VentureBeat reports.”
NY DMV MDL and Other Acronyms: Identity News Digest FindBiometrics
Optimizing Cost and Performance of Auth0's Private Cloud auth0 “uses Performance Engineering to balance infrastructure cost and performance”
Build resilience in a world of weaponized trust SC Media - CISOs are building stronger relationships with their A-list vendors and have fewer solutions for their team to manage and learn
Welcome to the fraud factory: Home of the pig butchering scam IDnow - “Earning the victim’s trust can often take several months, depending on the commitment of the criminal“
New Social
[Steampipe+Mastodon] Mastodon timelines for teams Jon Udell
WordPress and ActivityPub Werd DWeb Aquisitions begin
I believe it will remain open source, but by acquiring the copyright to the code and hiring its developer to work on open web projects, Automattic is sending a signal about what it considers to be important.
Thoughtful
Anti-Racist Starter Pack h/t Ben Werdmüller - “A list of anti-racist books, articles, documentaries, podcasts, and interviews”
Everythign is Liquid The Real Lesson of Silicon Valley Bank for all of us Dana F. Blankenhorn ‘When everything is liquid “It makes everything precarious for everyone”’
Qualities Of Value Wilder Team - “[after] countless hours of research and reading over the past five years, four ‘qualities of value’ have emerged. These are provenance, persistence, flexibility, and portability”
Thanks for Reading
Read more \ Subscribe: newsletter.identosphere.net
Contact \ Submission: newsletter [at] identosphere [dot] net