Identosphere 201: DIDComm Formal Analysis • DNP Network Launch - Decentralised Identity Platform • Customer Loyalty • ID Challenges for AI APPs
Everything related to decentralized identity and verifiable credentials: DWeb, Fediverse, Public Sector, Enterprise, policy, research literature, standards and development.
Identosphere’s Weekly Highlights
We Gather, You Read!
We’re still aggregating industry info.
Thanks for supporting our efforts by a PayPal, or Patreon
Upcoming
New Listings
[online] India’s Digital Trust Ecosystem: An Overview 9/05
DIF Hackathon 10/1-11/4
[New Orleans] Hybrid Identity Protection Conference (HIP Conf) 11/13-14 - the world's foremost hybrid identity leaders deliver key insights and trends in today’s evolving threat landscape.
Previously Listed
Agenda for ETSI / CEN Workshop on EU Digital Identity Framework Standards 9/10-12
FediForum - unconference for the Fediverse 9/12-24 [Kaliya is facilitating]
Check out the session notes and demo videos from our March 2024, September 2023 and March 2023 events to see what FediForum is all about.[Berlin, Global Trust Foundation] EU Digital Identity Wallets Forum 10/09
[California] Internet Identity Workshop #39 10/29-31 Early Bird Registration end August 29.
Shared Signals Interop Event at Gartner's IAM Summit 12/9-11
Business
[youtube] Verifiable Credentials: How to Adopt a Zero Trust Strategy 2024-08-27 Indicio
Join Indicio as we welcome Dr. Chase Cunningham “Dr Zero Trust”, Cyber Security Expert and Author, to dive into the intersection between Zero Trust and Verifiable Credentials with co-speaker, Will Groah, a member of the Indicio Board of Directors.
Unlocking Customer Loyalty: How Verifiable Credentials Lead the Way 2024-08-27 CIOL Bureau
we introduce innovative approaches that leverage verifiable credentials as a game-changing solution to address the shortcomings of traditional loyalty programs. Discover how revamping your loyalty program can not only overcome these challenges but also significantly boost customer satisfaction and sharpen your competitive edge in the market.
Break Free from Conventional Loyalty Programs: The Game-Changing Power of Verifiable Credentials 2024-08-27 www.dqindia.com
Meet Sarah, a frequent traveller who is a member of several loyalty programs across airlines, hotels, and retail stores, each offering various rewards and benefits. Despite her loyalty, Sarah finds it challenging to track her points across different programs and often forgets to redeem her rewards before they expire.
White Paper: Replacing Password-Only Authentication with Passkeys in the Enterprise - FIDO Alliance 2024-08-29 fidoalliance.org
This white paper outlines the benefits of passkeys, the user experience, and adoption considerations for enterprises.
Standards Development
[literature] What Did Come Out of It? Analysis and Improvements of DIDComm Messaging 2024-08-29 Christian Badertscher,Fabio Banfi, Jesus Diaz; eprint.iacr.org
We present the first formal analysis of DIDComm’s cryptography, and formalize its goal of (sender-) anonymity and authenticity. We follow a composable approach to capture its security over a generic network, formulating the goal of DIDComm as a strong ideal communication resource
DIF Newsletter #43 2024-08-30 Decentralized Identity Foundation
DID Method Standardization: DIF received strong support for this cross-organizational initiative, aiming for open collaboration in standardizing Decentralized Identifiers (DIDs).
Identifiers and Discovery WG launched the DID Traits work item
Claims & Credentials WG released an initial draft of the Basic Person abstract data model
Applied Crypto WG is advancing the BBS Signature Scheme
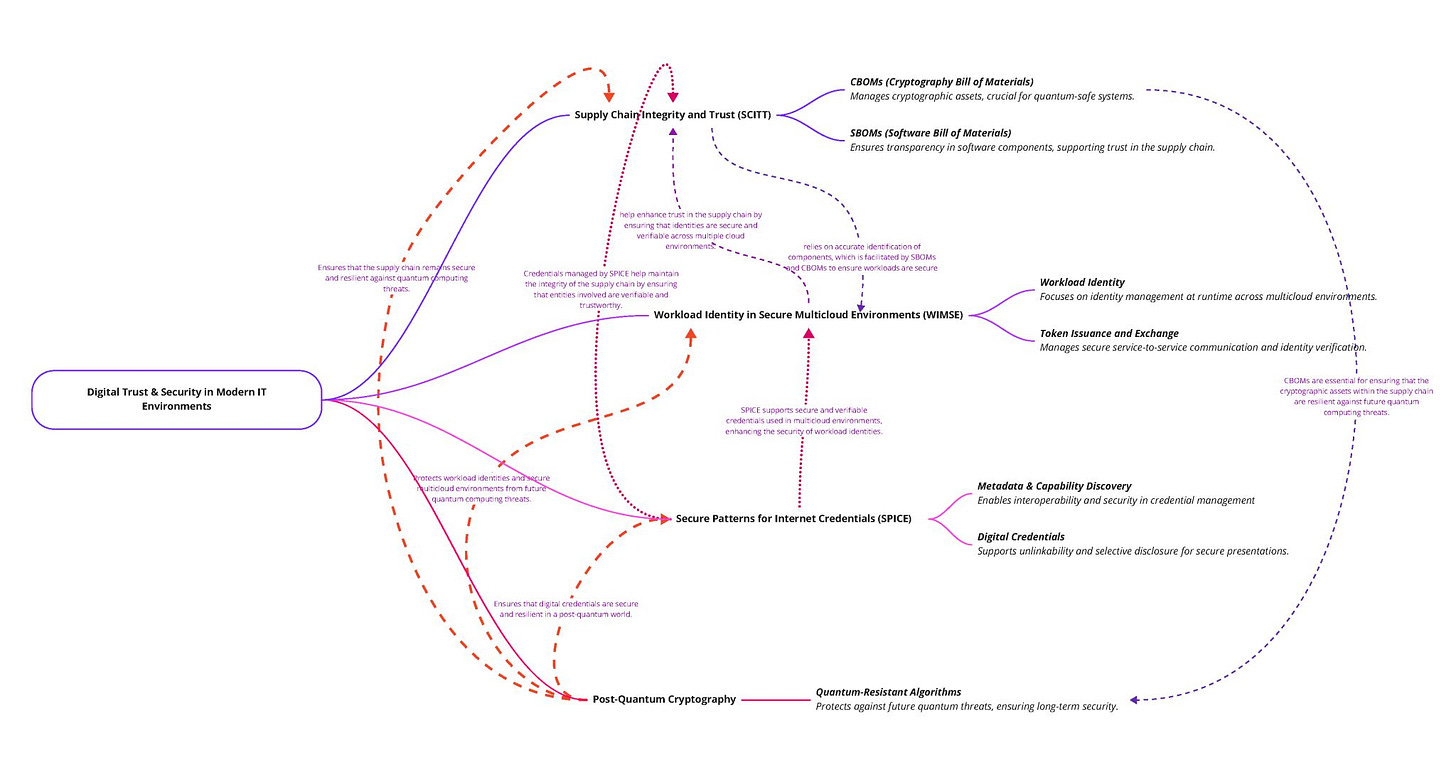
[LinkedIn] after writing two blog posts about standards, reviewing documentation on MFA requirements for the public safety sector, and studying NIST SP 1800-38B: Migration to Post-Quantum Cryptography 2024-09-01 Heather Flanagan
I ended up loopy enough to try mindmapping how several pieces of work I'm focused on relate to each other.
[linkedin] Exploring the DIDComm Protocol for Secure Communication in Decentralized Systems 2024-08-25 Gourav Patidar
DIDComm is a powerful protocol that brings secure, interoperable communication to decentralized systems. By understanding and implementing DIDComm, developers can build applications that not only respect user privacy but also enhance the security and trustworthiness of digital interactions.
Thoughtful
Digital Identity and Access Control 2024-08-28 Phil Windley
The more we rely on federated identity systems, with their tendency to centralization, the more we risk ceding control over our digital lives, reducing our autonomy and increasing our dependence on entities whose goals may not align with our own.
An Introduction to Systems Thinking: Part II 2024-08-30 blog.weareopen.coop
Feedback loops are essential for understanding how systems behave, adapt, and evolve over time. By mastering the dynamics of feedback loops, you can identify how small changes can ripple through a system, leading to significant outcomes, whether intended or unintended.
Privacy-Enhancing Technologies: Protecting Human and Non-Human Identities 2024-08-29 sphericalcowconsulting.com
The rise of privacy-enhancing technologies (PETs) like zero-knowledge proofs and advanced biometrics is reshaping how we think about and manage digital identity. But what’s driving this change, and why should it matter to you, whether you’re managing user access or overseeing countless processes and APIs in the cloud?
[linkedin] I’m pleased to announce that my first book, Relationality is launching today! Ben Werdmuller
if we start rewarding people who build relationship for the value that we create, then we can invite in a radically more resilient, innovative, joyful and democratic world.
Human Needs
Digital transformation and the future of humanitarian response 2024-08-22 Global Policy Journal
The idea of DPI reflects a shift from building specific digital systems and services to building underlying infrastructure, much like roads, railways, and plumbing. For example, in 2020 Brazil’s central bank launched Pix, an instant payment system, followed by an open finance regime that enables users to share their banking data with a range of credit, insurance, and savings providers. Today, 84% of adults in Brazil have a financial account, up from 56% in 2011.
Data Strategy
[healthcare] Effective Data Solidarity requires symmetry in human digital agency and a social license 2024-09-02 MyData.org
This blog is focusing on a third component of a human-driven fair data economy: health data sharing. In a world where increased pandemic risks require data-driven evidence to regularly adapt public health guidelines, and where there is major innovation potential expected from data-trained AI solutions, effective data sharing is critical to increase the amount of available data.
fairsfair: Data governance and privacy pop up in mobility 2024-08-29 Mydata.org
With a fragmented landscape of apps, ticketing platforms, and identification means, he found out that the main thing all these digital solutions have in common is that they support digitised interactions. Interactions that either allow for transport services or payment services to take place.
Government
Verifiable Credentials Set to Transform Digital Immigration Documents in the US - EBSI 2024-08-26 European Commission
The US joins a growing list of countries keen on reinventing personal documents to stay up to date with technological advancements and meet citizens' demands for easy, trustworthy, and seamless public services. This growing global interest in decentralised, verifiable and secure documents – which is shared with EU Member States – indicates a rising international focus on adopting VC standards.
What you need to know about Mobile Driver’s Licenses 2024-08-28 Tim Spring Indicio
an mDL is not the same as a verifiable credential because the mDL data can technically be stored in a siloed database. However, a verifiable credential, which allows a person to hold their data, could absolutely fit this standard and be used to easily issue mDLs, as they meet all the other requirements laid out above.
Development
Implement ASP.NET Core OpenID Connect OAuth PAR client with Keycloak using .NET Aspire 2024-09-02 damienbod.com
This post shows how to implement an ASP.NET Core application which uses OpenID Connect and OAuth PAR for authentication. The client application uses Keycloak as the identity provider. The Keycloak application is hosted in a docker container. The applications are run locally using .NET Aspire. This makes it really easy to develop using containers. [Code]
Company Stories
Growing the Buz Economy: Announcing the Social Intelligence Paranet Launch 2024-08-30 LunarCrush, OriginTrail
The Social Intelligence Paranet will operate on the OriginTrail DKG, a permissionless peer-to-peer network that ensures all social content published to the Paranet is discoverable, verifiable, and attributed to its owners. This setup allows AI services leveraging this knowledge base to avoid challenges like hallucinations, managed bias, and intellectual property violations. For an in-depth understanding of the technical design of paranets, DKG, and decentralized Retrieval-Augmented Generation (dRAG), we recommend reviewing the OriginTrail Whitepaper.
IDAC Sponsor Spotlight - Semperis 2024-08-28 Identity at the Center
They delve into Semperis' tools like Purple Knight and Forest Druid, focusing on their capabilities in detecting and mitigating Active Directory and Entra ID vulnerabilities. The conversation covers the critical role of prevention and response in ITDR, the impact of ransomware on Enterprise ID infrastructures, and the importance of ensuring a trusted state in Active Directory. They also touch on the upcoming Hybrid Identity Protection Conference and its significance for industry professionals
[dhiway] Samagra and Dhiway come together to build a developer community for CORD 2024-08-28 Dhiway
India is making remarkable strides in building DPGs and DPI. As we set new benchmarks, it becomes crucial to ensure the adoption, maintenance, and sustainability of DPGs and open-source technology for the public good.
[dhiway] Integra and Dhiway Partner Up to Expand Verifiable Credentialing 2024-08-28 Dhiway
Additionally, we intend to extend our Wallet software to support CBDC, NFTs, and Crypto, utilizing Dhiway’s robust blockchain technology.
Dhiway makes the Finternet possible 2024-08-28 Dhiway
The BIS Working Papers No. 1178 […] outlines a way to unlock the potential within the financial sector by enabling an architecture that draws on on the Internet, decentralization, and unbundling.
DNP Group Launch
[LinkedIn] DNP Network Launch - Decentralised Identity Platform 📣 2024-09-03 Katryna Dow
I geeked out in the "Wallet Security" track where Paul Bastian started explaining how to achieve digital, cryptographic key binding with Wallet Trust Evidence and Wallet Instance Attestation, both providing evidence that keys are managed correctly and wallet instance is not revoked by the user. Warning 🚒 , more standards are being defined. ❓
DNP Launches Platform for Building Decentralized ID-based Digital Credential Issue and Verification System 2024-08-28 DNP Group
DNP will be in a position to provide companies and organizations promoting VC-related businesses with the necessary functions to match planned uses and environments. Such functions include VC issuance and verification systems, and digital identity wallets, as a mechanism allowing consumers to verify their identity via smartphones where consumers used to manage VC.
Identity and AI
Identity Challenges for AI-Powered Applications 2024-08-28 auth0.com
While many threats to AI-based systems and applications are common to traditional applications, there are others that are specific to AI. OWASP, the most known independent security-focused organization, launched a specific initiative about AI security called AI Exchange.
Verida Technical Litepaper: Self-Sovereign Confidential Compute Network to Secure Private AI 2024-09-02 Verida
It is essential to protect user privacy within the ecosystem and prevent user data leaking to non-confidential compute services outside the network. Each service deployed to the network will be running verifiable code, running on verifiable confidential compute infrastructure.
DWeb
[rss] I like the way you like it like that 2024-09-03 werd.io
"It's a simple thing, but it's kind of a big deal. With this milestone, Ghost is for the first time exceeding the functionality of a basic RSS reader. This is 2-way interaction. You publish, and your readers can respond."
[ethereum] Hyperledger Web3j in 2024: Updates for Blockchain Developers 2024-08-29 Hyperledger.org
One of the significant updates this year is the adaptation of Hyperledger Web3j to support EIP-4844, introducing a new type of transaction known as "blob transactions." […] "proto-danksharding," represents a major shift in how the Ethereum network handles large amounts of data.
How TBD is leveraging open standards 2024-08-28 developer.tbd.website
OpenID Foundation: We’re also working with the OpenID Foundation to integrate their standards with VCs and DIDs. This work is focused on extending OpenID’s capabilities beyond web-based applications, making them applicable in backend services and mobile environments. [...]\
We’re also making significant strides with our Rust Core approach, which will form the basis for many of our SDKs. This effort will allow us to support multiple languages more efficiently and ensure greater consistency across our implementations. [video]
Comparisons
[youtube] Protocol Wars - The Fediverse Explained! 2024-08-28 WVFRM Podcast
In this episode, we dive deep into the origins of two of the leading social networks and the protocols they run on - Threads/ActivityPub and Bluesky/AT protocol. If you've been wondering what the heck the Fediverse is, this episode is for you!
[Web5 vs BlueSky] How Web5 and Bluesky are Building the Next Layer of the Web - A Comparative Analysis 2024-08-27 TBDevs
AT Proto focuses on decentralized social media, while Web5 enables developers to build any type of application, from financial tools to social media to health management. For example … [video]
Bluesky
Introducing Bluesky Starter Packs 2024-06-26 Bluesky
Custom feeds. On Bluesky, you can set any algorithm or topic as your home timeline.[...] Add your favorite accounts and encourage new users to follow them.
New Anti-Toxicity Features on Bluesky Bluesky
we’re taking a look at specifically toxicity (harassment, dunking, etc.) and some steps we’re taking to mitigate it from the product perspective.