Identosphere #209: DIDComm gets formal • SSI Is Dead - Long Live SSI • G7 Mapping Exercise
Everything related to decentralized identity and verifiable credentials including standards and development: updates, walkthroughs, from the enterprise to web3, real world use, policy and research.
We Gather, You Read!
We’re still aggregating industry info.
Thanks for supporting our efforts by a PayPal, or Patreon
Upcoming Events
We had so many we created a separate issue this week. Please see it here.
Submission Deadlines
TDI 2025: 3rd International Workshop on Trends in Digital Identity Submissions:12-09 Workshop: 2025-02-03
[Spain] International Conference on Online Identity Management Technologies Submissions: 10/31 Conference: 02/10-11
From the Blogosphere
Identity as Root 2024-10-15 ; Doc Searls
This is from an email thread on the topic of digital identity, which is the twice-yearly subject of the Internet Identity Workshop, the most leveraged conference I know.
SSI Is Dead - Long Live SSI
Why Verifiable Credentials Aren’t Widely Adopted & Why Trinsic Pivoted 2024-10-16 Riley Hughes
At the Internet Identity Workshop 38, I announced my talk with a description something like this:
Five years ago at this conference, Trinsic’s first product (our self-sovereign identity wallet app) was launched. Today, I’m hosting a session called “SSI didn’t work. Trinsic is pivoting.”
The Greatly Exaggerated Demise of SSI: A Rebuttal to Premature Eulogies 2024-10-15 Decentral Gabe
The post I'm responding to makes a point about people resisting its conclusions because their livelihoods depend on it. But let’s be real—Trinsic depends on this too, just as much as mine does.
Organizations
‘The Community Moved On’: Sovrin Announces MainNet’s ‘Likely Shutdown’ 2024-10-21 IDTechWire
Decline in MainNet Usage: No new Transaction Endorsers joined in 2024; efforts to revitalize interest failed.
Regulatory Uncertainty: Ambiguities around decentralized identity discouraged investments, hindering Sovrin's growth.
Technical Challenges: Resources invested in Steward node upgrades diverted to TestNet issues, straining resources.
Governance and Community Involvement: Limited involvement from the Steward community in governance burdened Trustees with heavy debt from previous Board.
Accredify Joins the Asia Pacific Digital Identity Consortium to Shape the Future of Digital Trust and Identities in the APJ Region 2024-10-18 Accredify
Consortium Objectives:
Establish policy frameworks for digital identity governance across borders
Create real-world use cases enhancing daily life with digital identities and verifiable credentials
Foster innovation and inclusivity in building a trusted digital economy
DINZ Executive Council Elections & Annual Meeting 2024 2024-10-15 ; Digital Identity New Zealand
The Council is the governing group for the association, providing guidance and direction as we navigate the evolving world of digital identity in Aotearoa.
Deadline for nominations: 4 November
Scheduled for 10:00am on Thursday, 5 December 2024
Online voting will take place in advance of the meeting, with results announced at the Annual Meeting
DIF Hackathon
Event Timeline DIF Hackathon 2024
DIF Hackathon 2024 www.youtube.com
Building Decentralized Identifier (DID) Applications with ArcBlock Pt 2
Components for Secure Identity and Information Verification with Extrimian
Harnessing Decentralized Identity for Verifiable AI with cheqd
Report
[Report] G7 Mapping Exercise of Digital Identity Approaches 2024-10-15 www.oecd.org
This report presents a mapping exercise to identify commonalities in digital identity approaches among G7 members that can support future interoperability efforts. These commonalities include shared concepts and definitions, the use of international technical standards and approaches to levels of assurance.
[linkedin] Dr. Carsten Stöcker G7 MAPPING EXERCISE OF DIGITAL IDENTITY APPROACHES 2024-10-21 Carsten Stöcker
The #Path #Forward 🚀 Adoption of digital wallets, decentralized identity frameworks, and verifiable DPPs is accelerating, merging citizen, enterprise, and machine identities into seamless global systems.
[Report] G7 Mapping Exercise of Digital Identity Approaches 2024-10-15 www.oecd.org
This report presents a mapping exercise to identify commonalities in digital identity approaches among G7 members that can support future interoperability efforts. These commonalities include shared concepts and definitions, the use of international technical standards and approaches to levels of assurance.
Standardization
DIDComm gets formal 2024-10-15 iohk.io
In our work, we formally look into whether DIDComm’s combination of encryption and key derivation schemes achieves the claimed security properties. However, we exclude digital signatures from our analysis. [...] Thus, formally capturing DIDComm’s security goals is a big part of our work. To do this, we studied its specification and related standards and also comprehensively reviewed the main implementations in Python and Java, and even coded our own improvements, as described next.
What Did Come Out of It? Analysis and Improvements of DIDComm Messaging 2024-08-29 Christian Badertscher, Fabio Banfi, Jesus Diaz; iacr.org
Present first formal analysis of DIDComm's cryptography
Captured security over generic network, forming strong ideal communication resource
Prove proposed encryption modes provide expected privacy and authenticity but leak information beyond underlying network - tweet thread
Methods for Decentralized Identities: Evaluation and Insights 2021-08-25 Walid Fdhila, Nicholas Stifter, Kristian Kostal, Cihan Saglam, and Markus Sabadello
This paper provides an evaluation of a selection of distributed identity methods, and analyzes their properties based on the categorization specified in the W3C recommendation rubric.
Grant Negotiation and Authorization Protocol (GNAP) 2024-10-14 Simon Willison
The most interesting difference between GNAP and OAuth 2 is that GNAP no longer requires clients to be registered in advance. With OAuth the client_id and client_secret need to be configured for each application, which means applications need to register with their targets - creating a new application on GitHub or Twitter before implementing the authorization flow, for example.
Research
[Use-Case] Decoupling Online Ride-Hailing Services: A Privacy Protection Scheme Based on Decentralized Identity 2024-01-21 ; Sun, Liu, Zhang, Nigang Sun, Yuxuan Liu, Yuanyi Zhang, Yining Liu; mdpi.com
Issue with Existing Online Ride-Hailing Systems:
Direct association of digital identities with real identities within the platform
Leaves users vulnerable to privacy breaches
Government
The EUDI Wallet: A First Step on Germany’s Way Into a Flexible Digital Identity Future www.kuppingercole.com
Germany has officially launched the German part of the EUDI Wallet initiative, a significant advancement in digital identity management as part of the broader European eIDAS 2.0 regulation.
French Court Rules ISPs Must Block Porn Sites That Don’t Use Age Verification idtechwire.com
Enforcement of a July 2020 law requiring adult content sites to verify users’ ages before granting access
Child protection associations advocating for stricter implementation
Recent victory at the Court of Cassation reaffirmed their right to demand action from internet service providers
Company News
Digi Yatra launches d-KYC campaign; promises convenience with privacy 2024-10-17 Bizz Buzz
Hyderabad-based company launches campaign: 'Don’t Know Your Customer'
Utilizes face biometric technology for contactless passenger processing at airports
Adheres to highest global standards for data protection and privacy
6.4 million app users
Operations in 24 locations across India
Revolutionizing Verified Digital Identity Tom Sargent; Vidos
How to Implement Verifiable Credentials in Your Organization:
Unlock future of enterprise identity management
Reveal secrets for efficient, tamper-proof credentials
Streamline workflows
Boost security.
Matter has a new website: Trust in every transaction. Certainty in every connection.
So does Anonyome Labs: Stop fraud and protect user data with reusable credentials
[AuvoDigital] Q3 2024 Progress Report 2024-10-18 IOTA
AuvoDigital, a platform specializing in organizational identity and verifiable credentialing, uses IOTA Identity to simplify organizational identity management with its AutoID application, and IOTA EVM to power AuvoComply, its compliance application featuring secure, reusable KYC/AML solutions and scalable wallet verification.
MATTR VII Changelog: Terminology updates across MATTR platforms 2024-10-13
To make it easier to consume our capabilities, we have made some changes to our terminology to describe credentials supported by MATTR platforms by their underlying technology and standards.
mDocs: Previously referred to as Mobile credentials.
CBOR Web Tokens (CWT) credentials: Previously referred to as Compact credentials.
JSON credentials: Previously referred to as Web credentials.
HoVI.ID Identity infrastructure for the internet
New company making claims…
The only verifiable credential integration you’ll ever need
Build effortlessly with self-sovereign identity on global standards
Business
Why you need to add Verifiable Credentials to your biometric authentication systems 2024-10-15 Sam Curren; Indicio
The market for biometric digital identity in travel is expected to grow at a compound annual growth rate of 92%
Permissioning the City Product Journey
Transitioning from project to product — Day 1 2024-10-17 Dark Matter Labs
the series aims to share our ongoing progress, learnings, and reflections on building a digital permissioning system designed to unlock underutilised spaces in the city for civic use, through introducing participatory and distributed forms of spatial governance.
User journey and scenario building — Day 2 2024-10-17 Dark Matter Labs
Through the user journey exercise, we were able to clearly distinguish the differences between the three types of permission processes: pre-defined/automated, exception-based, and bespoke permissions.
Are we coding too soon? — Day 3 2024-10-17 Dark Matter Labs
Three Potential Strategies for Dark Matter Labs' Product Development
Maximize Experimentation:
Maximize Potential for Real Users:
Interoperable Permission Engine:
Explainer
Decentralized identity and what if I lose my phone? 2024-10-17 Trevor Butterworth; Indicio
Verifiable Credentials represent a massive net gain on how we currently manage identity online and off. video
What’s the Difference Between a Physical ID Card and a Verifiable Digital Credential? 2024-10-18 blog.spruceid.com
New York Times report reveals teenagers and twentysomethings find wallets "uncool"
Preference for storing all payment methods, documents, or credentials on smartphones (Apple Pay, etc.)
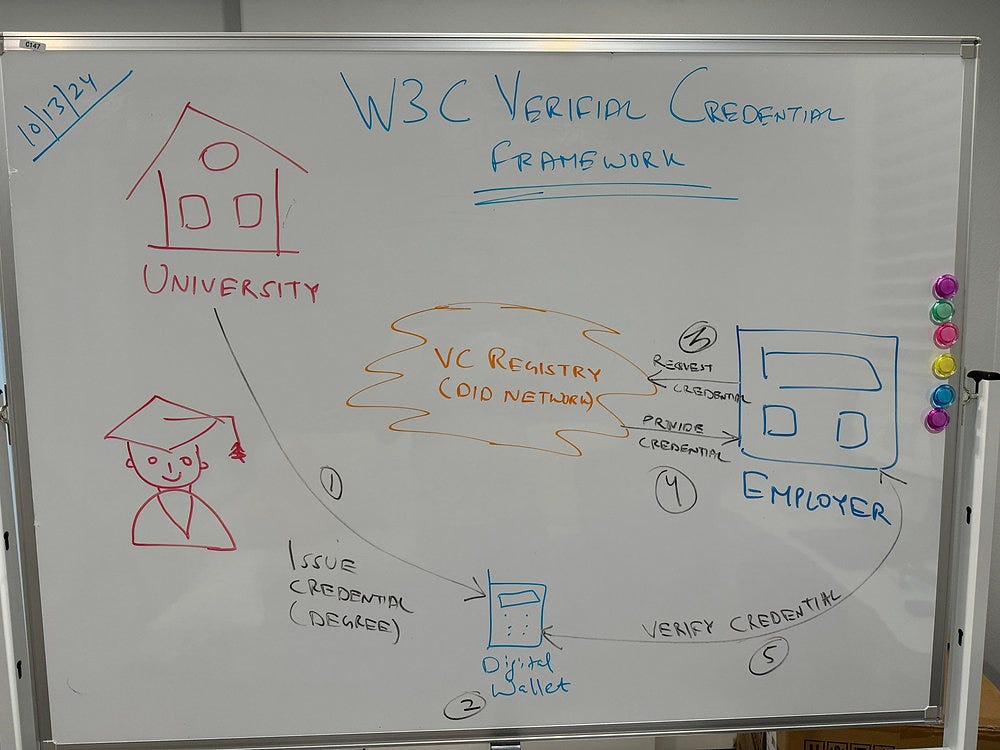
The Application of W3C Verifiable Credentials in Modern Digital Scenarios: A Comprehensive Guide 2024-10-14 www.demystifybiometrics.com
Embracing the world of mDLs and ISO/IEC 18013-5 has been an exciting journey for me. [...] However, the recent introduction to the W3C VCs standard by my friend Leo has been a game-changer.
[Digital Twins] Self-Sovereign Data and Identity 2024-06-28 MOBI
According to a report by IoT Analytics, there were 16.6 billion connected IoT devices by the end of 2023. This is projected to grow 13% to 18.8 billion by the end of 2024. As digitalization touches nearly every aspect of life — from payments to services — it’s crucial to adopt secure, interoperable, and user-friendly models for managing digital identities and data.
Tools
[GitHub] AKSW/jekyll-rdf: 📃 A Jekyll plugin to include RDF data in your static site or build a complete site for your RDF graph AKSW Research Group
📃 A Jekyll plugin to include RDF data in your static site or build a complete site for your RDF graph - AKSW/jekyll-rdf
WorldCoin Watch Continues
Rebranded Worldcoin Leans Into Biometric ID, Deepfake Detection
Beyond ID
Pluralistic: You should be using an RSS reader 2024-10-16 Cory Doctorow
This conduit is anti-lock-in, it works for nearly the whole internet. It is surveillance-resistant, far more accessible than the web or any mobile app interface. It is my secret super-power.