Identosphere 234 July 5- July 12 | GDC • More SPICEyness • New Consult Hyperion Report • Vitalik has More Identity Ideas
No Phone Home Continues…
[MATTR] Thoughts on solving modern identity challenges (comments on the No Phone Home movement)
Recently, the "nophonehome" movement sparked an important conversation about digital identity systems, privacy, and control. These conversations are timely and essential.
When Verification Calls Home: Three Views on Privacy, Risk, and Digital Credentials
“There’s been renewed attention lately on mobile driver’s licenses (mDLs) and the ISO/IEC specification that defines them. One of the more surprising aspects of the specification, even to long-time standards contributors, is that it allows the entity verifying a credential to contact the issuer directly in real time, a capability known as ‘phone home.'”
Considering Global Issues and Activity
The New Scramble for Africa: Digital Empires, Tech Sovereignty, and the Role of India, Estonia, GovStack, Brazil, and Other Digital Powers
In 1884, colonial powers gathered at the Berlin Conference to divide the African continent without African consent. Today, we are witnessing a new kind of scramble: one not for physical territory but for digital dominance. Africa’s vast population, untapped data resources, and growing digital infrastructure make it the focal point of a 21st-century geopolitical struggle among emerging and established digital powers: India, China, the United States, the European Union, Estonia, Brazil, and new initiatives like GovStack.
Global Digital Collaboration happened.
UN OPen Source DPI Day
DPI is a process, not an outcome. We know that tech isn’t neutral - and it needs to be actively shaped if it’s going to benefit people.
Decentralized identity goes mainstream: the Global Digital Collaboration 2025 Conference
Interoperability
How to slay with Verifiable Credentials
From the “How do we think about all this stuff” dept:
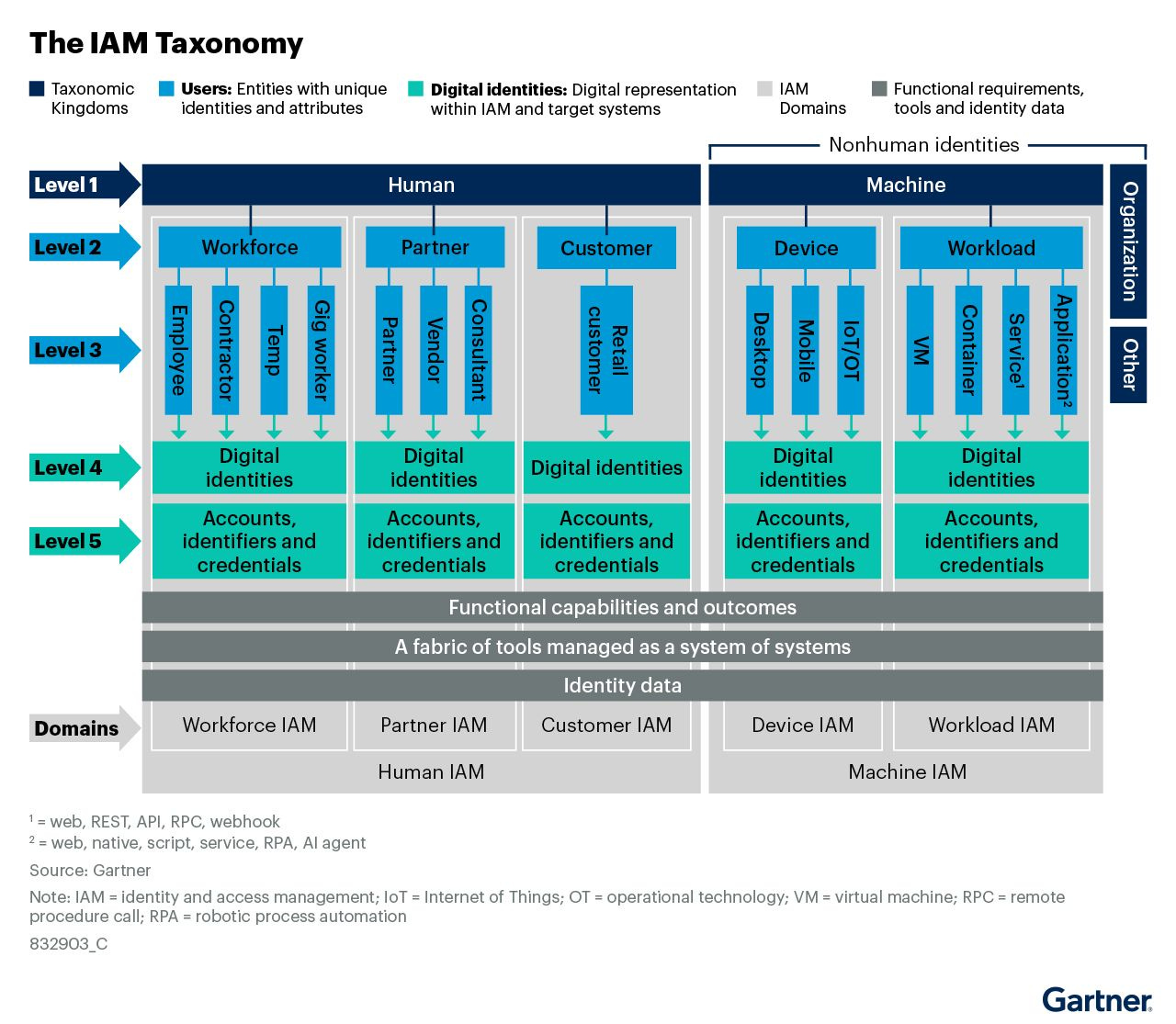
IAM - Taxonomy, Domains and Tools
Challenge Led Innovation
Vitalik has Identity Ideas
Ethereum Co-Founder Buterin Proposes Decentralized Digital Identity Model
Traditional digital identity systems often depend on centralized authorities, which can be susceptible to hacking and data breaches. Buterin's model seeks to decentralize this process, empowering users with more control over their personal information and mitigating the risk of data misuse.
Standards
ISTTP:// A protocol for digital trade
In February this year, a group of trade and technology veterans announced the formal launch of the Verifiable.Trade Foundation, a Basel-headquartered non-profit organisation with a unique plan for digitalising trade. John Basquill speaks to three of the foundation’s founding members – chairman Stephan Wolf and board members Hans Huber and Daniel Cotti – about the vision behind the project and the progress made so far.
Moving on with Overlays Capture Architecture 2.0: A New Era of Semantic Interoperability
Finally we release RC1 of Overlays Capture Architecture Specification v2.0.0 which is signal for readiness of mentioned features and functions. The process of implementation already started in our reference implementation which can be followed at oca-rs.
(Mike Jones) More SPICEyness
In April, I wrote about several useful developments in the IETF Secure Patterns for Internet CrEdentials (SPICE) working group. I’ve recently contributed to progressing several specifications in preparation for the SPICE working group meeting at IETF 123 in Madrid. Here’s a tour…
Programmable Governance for Group-Controlled Decentralized Identifiers
Self-Sovereign Identity (SSI) is a paradigm for digital identity management that offers unique privacy advantages. A key technology in SSI is Decentralized Identifiers (DIDs) and their associated metadata, DID Documents (DDOs). DDOs contain crucial verification material such as the public keys of the entity identified by the DID (i.e., the DID subject) and are often anchored on a distributed ledger to ensure security and availability.
Thoughtful
Globally, People Want Control of Their Data
Majorities around the globe are concerned about the amount of personal information that social media companies and internet businesses know about them, according to a seven-nation survey by the Project Liberty Institute. At the same time, relatively few feel solidly in control of what happens to their data.
Decentralized Social Network
There's a graph in the middle of this article which is fairly sobering for those of us who are really hoping for Bluesky and Mastodon to succeed. In it, we see a gentle decline in X usage, a healthy increase in Threads usage, and a straight, slightly-declining line representing Bluesky usage that seems to stubbornly cling to the X axis.
(Doc Searls ) Education 3.0
Education 3.0 is what we get with Big AI, which will overthow Education 2.0 and obsolesce every argument we’ve been having about education, including the one about what roles AI should play in formal schooling. (Think of that last one as Education 2.9.)
(Rest of the World) Why Big Tech is threatened by a global push for data sovereignty
Developing countries from Nigeria to Vietnam are pushing back on Big Tech’s control of user data. These countries want tech giants to store their citizens’ data locally instead of overseas, to reclaim digital sovereignty.
Demand for local cloud services is growing due to the high cost of international providers and increasing awareness about data sovereignty.
Thoughtful AI
Gen AI and Gen PI
The phenomenon of deep fakes, where Generative AI creates realistic still and moving images mimicking real individuals, is deeply troubling for actors, authors and public figures. Some people have tried to assert intellectual property rights over their likenesses, but these approaches have proved problematic. Legal reform in this area would be complicated and time consuming.
Here I propose a simpler way to legally protect appearances, by applying established technology-neutral data privacy law to facial images and voice recordings.
Why Machine Identities Are the Next Big Compliance Challenge
Machine identities are digital credentials that enable non-human systems to authenticate and interact securely, but they often go unmanaged and create security vulnerabilities. Traditional identity governance tools designed for humans cannot handle the speed and scale of automated machine systems. New regulations require organizations to track machine actions and automate governance to meet the same accountability standards applied to human users.
Continuous identity is here: And it changes everything
At Identiverse 2025, the duo made the case for transforming traditional IAM frameworks into dynamic, event-driven architectures that use real-time signals, from endpoint health to behavioral anomalies, to continuously verify user trust and permissions.
AI Agent Identity
MCP vs A2A: A Guide to AI Agent Communication Protocols
As AI agents become more autonomous, developers need to understand how they communicate. We compare two key agent communication protocols: Model Context Protocol (MCP) and Agent-to-Agent (A2A), explaining how they work and when to use them.
Government ID Updates
One Month to Go: Preparing for the UK’s Mandatory Director and PSC Identity Verification
The United Kingdom is less than a month away from a major shift in how it handles director and beneficial owner identity verification. Under the Economic Crime and Corporate Transparency Act, new requirements will soon make it mandatory for company directors, Persons with Significant Control (PSCs), and anyone filing with Companies House to verify their identity. These changes aim to bring greater transparency to corporate structures and reduce the risk of fraud. They also introduce new pressures for compliance teams, legal advisers, and company secretaries—especially those still relying on outdated onboarding methods.
Cybersecurity by Design: Reimagining Digital ID for American Resilience
The recent rollback of Biden-era policies on cybersecurity and Digital Identity (Digital ID), including Presidential Executive Order 14144,1 presents the Trump administration with an opportunity to lay the foundation for modern, secure, and privacy-preserving Digital ID infrastructure here in the U.S. - By Tricia Gallagher, Treasury Solutions Info Tech LLC June 24,2025
Identity & the Digital Economy
(Consult Hyperion) Strategic readiness in Payments and Identity: building the digital economy’s bullet train
At this inflection point, identity, reputation, and tokenized value are no longer discrete elements—they are converging into a seamless, dynamic ecosystem. The future of payments is about more than speed or scale; it’s about embedding trust, context, and programmability into every transaction. This is a call to action for payment providers, technology architects, and financial institutions: it’s time to prepare not just for the next upgrade, but for a new paradigm.
Decentralized Web
Introducing the New Holochain Roadmap
It shows a summary of release history, status of in-progress work, and planning of upcoming work including releases actively being planned and those that are just incubating. These summaries are linked to our actual Github project management tooling to calculate our work velocity and expected completion of work in progress as well as planning estimation.