Identosphere 235 July 13-20: SSI Platform Analysis • What are we really doing? • Identity is local. Interop is global. • mDL • Digital Nations •
SSI Platforms in 2025: Strategic Paradigms for the Post-Regulatory Era
The Self-Sovereign Identity (SSI) landscape has fractured into three irreconcilable paradigms, each with existential tradeoffs:
* Regulated Pragmatism (Condatis, Microsoft Entra) for compliance-critical sectors,
* Web3-Native Sovereignty (Dock, Veramo) for decentralized purists,
* Hybrid Interoperability (Walt.id) for organizations bridging both worlds.
Our analysis of 8 leading platforms reveals that 78% of failed SSI implementations stem from underestimating regulatory choreography and hidden TCO — not technical capabilities. Choose wisely: your paradigm alignment will dictate survival in 2026’s regulatory tsunami.
What are we really doing?
(Christopher Allen) Musings of a Trust Architect: When Technical Standards Meet Geopolitical Reality:
Digital Identity, Sovereignty, and the Erosion of Foundational Principles. It’s hard to boil the problems at GDC25 down to a single issue, because they were so encompassing. For example, there was a pattern of scheduling issues that undercut the community co-organizing goal of the conference and seemed to particularly impact decentralized talks. One session ended up in a small, hot room on the top floor that was hard to find. (It was packed anyway!) Generally, the decentralized-centric talks were in bad locations, they were short, they had restricted topics, or they were shared with other panelists.
(Kyle Den Hartog) From Printing Press to Digital Identity: A Pattern of Moral Crisis
To tie this back to recent history we can look at SIOP (and the attempt to revive it with SIOPv2) and the lack of adoption that came with it. If I remember the historical lore correctly too, that’s what kicked off OIDC in the first place. So it seems history is rhyming once again, but somehow we keep inverting things….
I know none of us want these systems to be abused for the purposes of identifying and harming human rights globally. That was the whole point of making them decentralized in the first place was to prevent the efficiency of abuse when the failure cases inevitably occur.
(Kyle Den Hartog) How SSI Becomes a Centralized Tool For Gatekeeping
To start, we first have to acknowledge that in a claims based model like with verifiable credentials or any other digital credential data model the technology itself is ambivalent to how it’s used.
So now that we understand how the issuance side has centralized let’s take a look at what this will mean in practice on the Web and in real life. Rather than re-iterate the points we made about the digital credentials API at Brave, I’ll just point back to our formal objection of it because they’re exactly the same as what I’d say here.
(Kyle Den Hartog) Decentralizing Age Verification with SSI: Separating Content Moderation from Guardianship
Then the operating system would be configured to recognize and trust the teacher’s or parent’s DID, which could issue a digital credential authorizing permission to access the content. In this way, the browser (or other applications) and operating system work in tandem to act as the verifier, not the centralized site server.
DID Methods Explored
[Podcast] (Joe Andrieu) Didja JWK? We did! (did:jwk, Part 1), &. Didja JWK? We did! (did:jwk, Part 2)
did:jwk embeds a JSON Web Key (JWK) in a DID to enable the use of JWKs in DID-enabled systems. Simple and straightforward, it promises to give did:key and did:pkh a run for their money. We talk with two of the co-authors of did:jwk, Jeremie Miller, known for creating Jabber and XMPP, and Orie Steele, CTO and Co-Founder of Transmute.
Digital Trust and Cyber Resilience
(OpenID) The OpenID Foundation's perspective on secure digital infrastructure
The blog post released today by the Cybersecurity and Infrastructure Security Agency (CISA) Securing Core Cloud Identity Infrastructure: Addressing Advanced Threats through Public-Private Collaboration outlines vulnerabilities in cloud identity infrastructure and the urgent need to address these challenges.
(ToIP) Digital Trust Ecosystems. Why they don’t make sense. TOIP EGWG 2025-07-10: Kyle Robinson
Learn why Kyle’s practical experience with the Canadian Province of British Columbia’s digital trust initiative has led him to focus on specific, high-impact digital credentials over broad “ecosystems.” Documenting these well fosters trust and enables organic growth and unpredictable efficiencies, naturally building interoperable digital trust networks.
(Project VRM) The Cluetrain Will Run from Customers to Companies
MyTerms not a technical spec, so implementations are open to whatever. Development on any of those can start now. So can work in any of the six areas listed above.
(Heather Flanagan) Local Flavors, Global Reach: Why Digital Identity Needs Cultural Context
This isn’t just about user attitudes. Cultural values shape system design too. Western identity architectures often assume:
* Ownership and individualism – the user holds and controls their identity;
* Transparency and audit – data trails should be visible and attributable;
* Consent as the primary safeguard – once informed, the user is responsible
Identity is local. Interop is global.
We’re building the infrastructure of digital personhood. That’s no small task. But if we want that infrastructure to support real people, not just tidy models, we have to let it speak in more than one voice.
(Indicio) How to use Proven Auth with your existing identity provider
Proven Auth is a version of Indicio Proven designed to enable single sign-on (SSO) using Verifiable Credentials. Proven Auth is more than just a way to enable passwordless authentication, it is a system for orchestrating access to applications and resources and managing the lifecycle of a user so that they have access to what they need — and only what they need — when they need it.
mDL from Multiple Perspectives
[Webinar] From Wallets to ID Wallets: How Digital ID Will Transform Payments
To answer that question, we hosted a live panel with Leonard Botezatu, Director of Product & Service Design for Identity at Mastercard, and David Kelts, Co-Chair of the mDL Jumpstart Committee at the Secure Technology Alliance.
Inside Samsung’s Strategy for Mobile IDs in the U.S.
We recently sat down with Rob White, Head of Identity Services at Samsung Wallet, to talk about the rollout of mobile driver’s licenses (mDLs) in the U.S.
(INATBA) Mobile Driver’s Licence (mDL) & Self-Sovereign Identity (SSI) Comparison – Updated
This is very much aligned to the core constructs of SSI which includes the concept of Issuers, Holders, and Verifiers; however, the differences are in the details. Here are some examples:
Digital Nations Explored
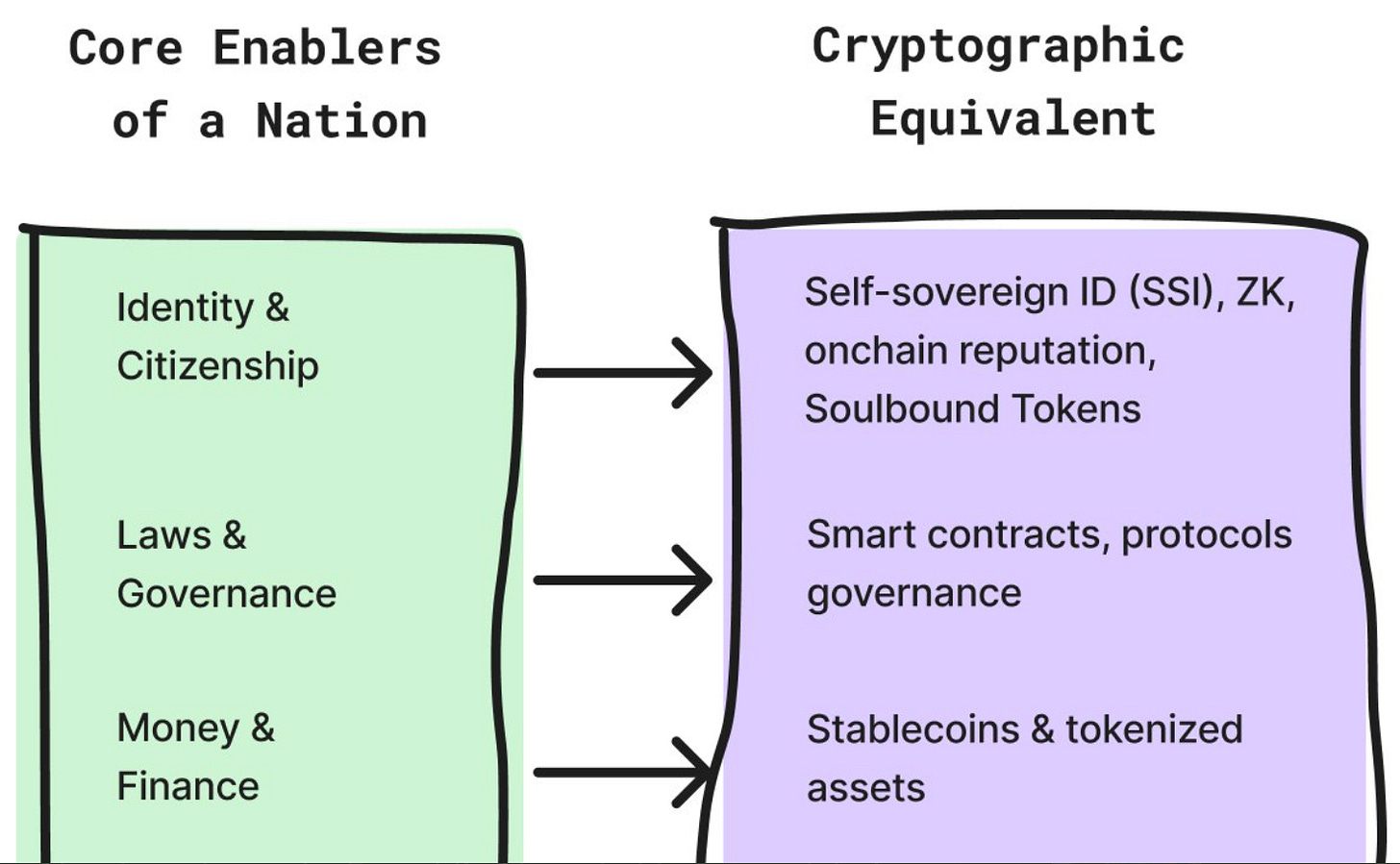
Why Now Is the Best Time to Build Sovereign Digital Nations
You can think of a sovereign digital nation (SDN) as an internet-native society that gives its citizens access to real rights and services using programmable infrastructure. Physical nations are built with concrete, and digital nations are built with code. SDNs are not DAOs or a digital community. They are a system of governance where identity, finance, and legal frameworks are all coordinated digitally, and enable real access to real services. Basically, what you can do in a physical nation, you should be able to do in a digital nation.
Identity and AI Agents
AI Agents & Digital Identity: How MCP and OIDC4VP Empower Agents to Use the EUDI Wallet
As AI agents become more capable of acting autonomously, they are being used in increasingly sensitive domains: finance, healthcare, education, legal compliance, and public services. In these contexts, identity matters.
This is where Self-Sovereign Identity (SSI) and digital wallets - particularly the upcoming EUDI Wallet in Europe - can play a transformative role. And two technologies make it all work: MCP and OIDC4VP.
Reports by Chequed:
Human-Centred Relationship Guide: For AI Agents and Their Creators
Entangled Relationship Guide: For AI Agents and Their Creators
Travel & AI Agents
(PhocusWire) Industry leaders on the future of digital identity and AI agents
Nick Price, founder of Netsys Technology and co-chair of the Decentralized Identity Foundation (DIF) Hospitality & Travel Special Interest Group, said DIF is working on standards and use cases for self-sovereign identity in the travel industry and trying to address a major gap: traveler profile and preferences.
Travel
Discover How Digi Yatra Is Shaping The Future Of Airport Journeys In India With Facial Authentication
Introduced in December 2022, Digi Yatra has so far enabled more than 60 million contactless movements at 24 large airports in the country. This ground-breaking platform, developed as a self-sovereign identity (SSI) system, is changing how passengers move through the airport with its smooth, touchless travel from check-in to boarding.
Personhood Creds
[Video] PEPR '25 - Verifying Humanness: Personhood Credentials for the Digital Identity Crisis
This talk examines personhood credentials (PHCs), which allow individuals to prove they are unique humans without revealing additional personal information, as a response to AI-powered deception and the need for better identity verification systems. The discussion focuses on how users understand and reason about PHCs' privacy guarantees compared to existing methods, and explores critical design considerations including trusted issuers, data attributes for credential issuance, and the trade-offs between centralized versus decentralized systems.
Research
Endorsement-Driven Blockchain SSI Framework for Dynamic IoT Ecosystems
This paper proposes a blockchain-based Self-Sovereign Identity (SSI) framework for IoT that allows any individual with verifiable trust linkage to issue credentials, rather than limiting this capability to trusted entities like manufacturers. The framework uses a layered architecture with dynamic trust calculations and smart contracts to manage credential operations, with a proof-of-concept showing minimal overhead while enabling more flexible and decentralized identity management in IoT environments.
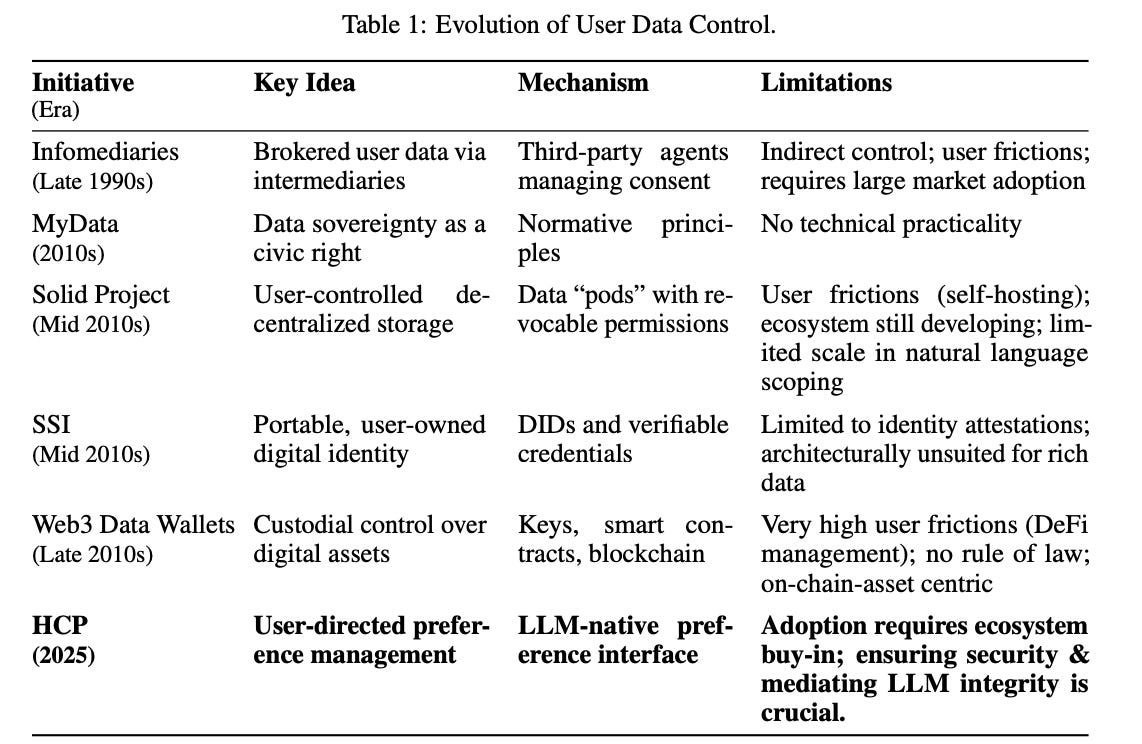
Robust AI Personalization Will Require a Human Context Protocol
This position paper proposes a Human Context Protocol (HCP) that would give users direct, granular control over their personal data and preferences across AI systems, replacing the current model where companies infer user preferences from behavior. The authors argue that HCP would create a more competitive AI ecosystem by enabling seamless data portability between services while ensuring AI systems are genuinely personalized and aligned with individual human values.
[Videos] (Jamie Smith) DIGITAL TRUST HUI TAUMATA : Hui Videos
Series of short videos
Education
How to implement identity verification at universities
Although many universities have digitalised certain academic procedures, enrolment remains tied to in-person, repetitive, and inefficient practices: you have to show up with physical documents, queue, repeat information already submitted, and go through an in-person identity verification that consists of looking at a civil servant in the eyes.