Identosphere #24 • eIDAS & SSI • State of Web ID • Indicio Launches Mainnet
Upcoming events, job opportunities, company announcements, SSI narratives, Literature, and other updates from blog feeds to the twitter lists.
Thank you for reading Identosphere’s Weekly
Identosphere Quarterly
We’re just passing through the Spring equinox. To celebrate, last week, we announced that we would begin publishing a Quarterly issue, a collection the top news items since beginning of Identosphere’s weekly.
We know you all can’t ready every issue, this quarterly release will help you to catch up on anything we don’t want you to miss.
Originally we said that would be made available to Patrons contributing at least $10 a month. After some consideration, instead we decided to share it with Patrons contributing at any level.
Coming up
Aries Mobile Agent & Demonstration by GlobaliD Demo • March 24
GlobaliD developer Alexis Falquier and Dev Bharel will show a brief video demonstration of the wallet connecting, receiving credentials and verifying the credential with an agent on Trinsic studio - showing interoperability.
GS1 US Innovation Summit • March 30
opportunity for innovators, entrepreneurs, and supply chain thought leaders to jumpstart strategies and actions that drive the future of trusted data sharing.
Lifelong Learner Project, Powered by Teachers • March 31
One of the winners of the ACE Blockchain Innovation Challenge, The Lifelong Learner Project is excited to share its vision and demonstrate our success with providing teacher professional credentials in a digital wallet with the larger education community.
PoCATHON by Affiniti • Mar 26 – May 9, 2021
We invite developers across the world to come and build applications that generate secure, portable and privacy-preserving credentials enabling trust across entities using Affinidi’s APIs
Affinidi PoCathon 2021 is a 6 week long virtual hackathon where developers will have the chance to design applications using Affinidi's resources and build a Proof of Concept (PoC).
Covid-19 Technology Innovations • April 14
“explore the technology innovations being pioneered in response to the Covid-19 pandemic, and what potential for Scottish ventures this presents.”
A talk by Peter Ferry, Gary McKay and Julian Ranger
Siccar, APPII and digi.me
Internet Identity Workshop XXXII (#32) • April 20-22
OpenID Foundation Virtual Workshop • April 29, 2021
Identiverse 2021 June 21-23 • Denver, co
Hiring
Gimly Blockchain Projects
We are hiring: a product development manager and a full-stack developer!
Build the next evolution of internet as part of @NGI4eu
Become an expert in Self-sovereign identity #SSI and #blockchain
Notabene Hiring
We are looking for a Full stack developer who will help us take our product to the next level. Our customers, global top crypto exchanges, rely on us to provide seamless and automated tools that enable them to manage crypto transaction risk.
SSI News
Gimly in eSSIf-lab: self-sovereign identity and NFC smartcards
Gimly is participating in the European SSI infrastructure programme (eSSIf-lab), building a bridge for the implementation of NFC smartcards with secure elements as physical SSI identifiers. Our aim is to enable self-sovereign identity for both online and offline identification, authorization and access management, with a decreased dependency on the use of personal smartphones.
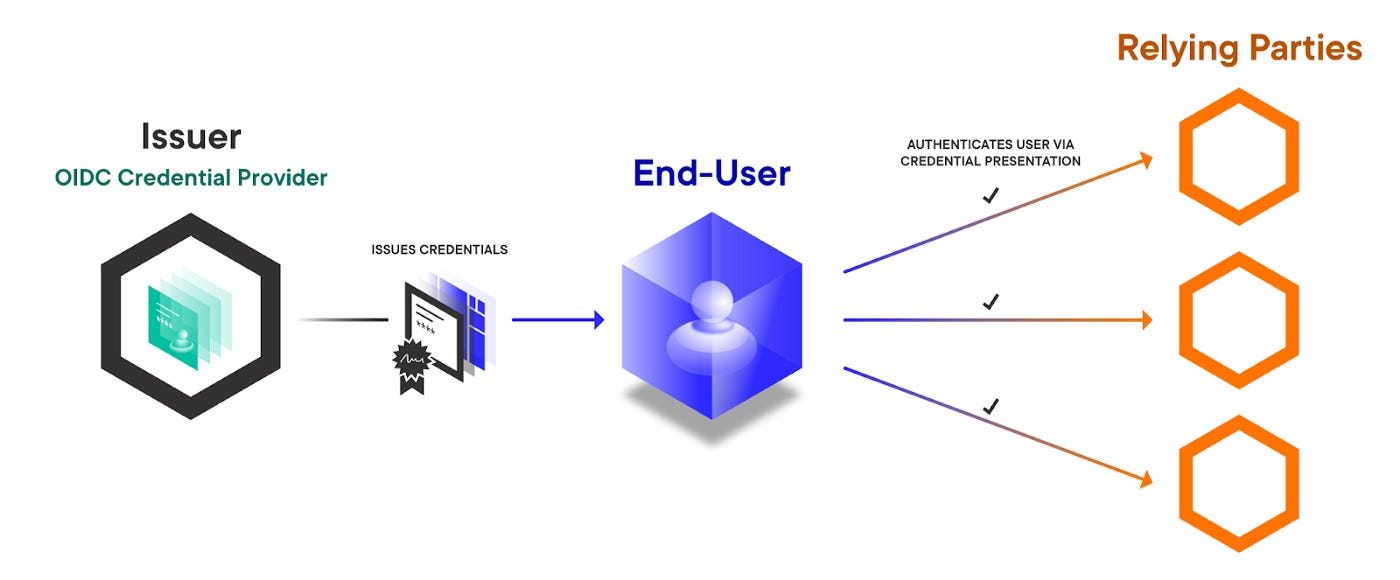
The State of Identity on the Web Mattr
This article discusses how the success of Open ID Connect shaped the state of identity on the web, how new web standards enable a new model, and describes a bridge between those worlds: OIDC Credential provider.
This cycle perpetuates the dominance of a few major IdPs and likewise forces users to keep choosing from the same set of options or risk losing access to all of their online accounts. In addition, many of these IdPs have leveraged their role as central intermediaries to increase surveillance and user behavior tracking, not just across their proprietary services, but across a user’s entire web experience.
[...]
OIDC Credential Provider allows you to extend OIDC to allow IdPs to issue reusable VCs about the end-user instead of simple identity tokens with limited functionality. It allows end-users to request credentials from an OpenID Provider and manage their own credentials in a digital wallet under their control.
DIACC White Paper: Consumer Digital Identity Leveraging Blockchain
SecureKey Technologies entered into a multiphase program with DIACC and the U.S. Department of Homeland Security (DHS) Science and Technology Directorate (S&T) to evaluate, develop, and deliver a solution for enabling distributed privacy enhanced identity ecosystems. This paper summarizes the work done as part of Phase 3 of the program, concentrating on the “Commercialization of the Verified.Me project”
Phase 1 White Paper: Architectural and Privacy Principles
Phase 2 White Paper: The Implementation
eIDAS and Self-Sovereign Identity (Video) Dingle Group
Why then is eIDAS v1 not seen as a success? There are many reasons; from parts of the regulation that focused or constrained its use into the public sphere only, to the lack of total coverage across all of the EU. Likely the key missing piece was that the cultural climate was not yet ripe and the state of digital identity was really not ready. Too many technical problems were yet to be solved. Without these elements the realized state of eIDAS should not be unexpected. All this said, eIDAS v1 laid very important groundwork and created an environment to gather important learnings to allow eIDAS v2 to realize the hoped for levels of success and adoption.
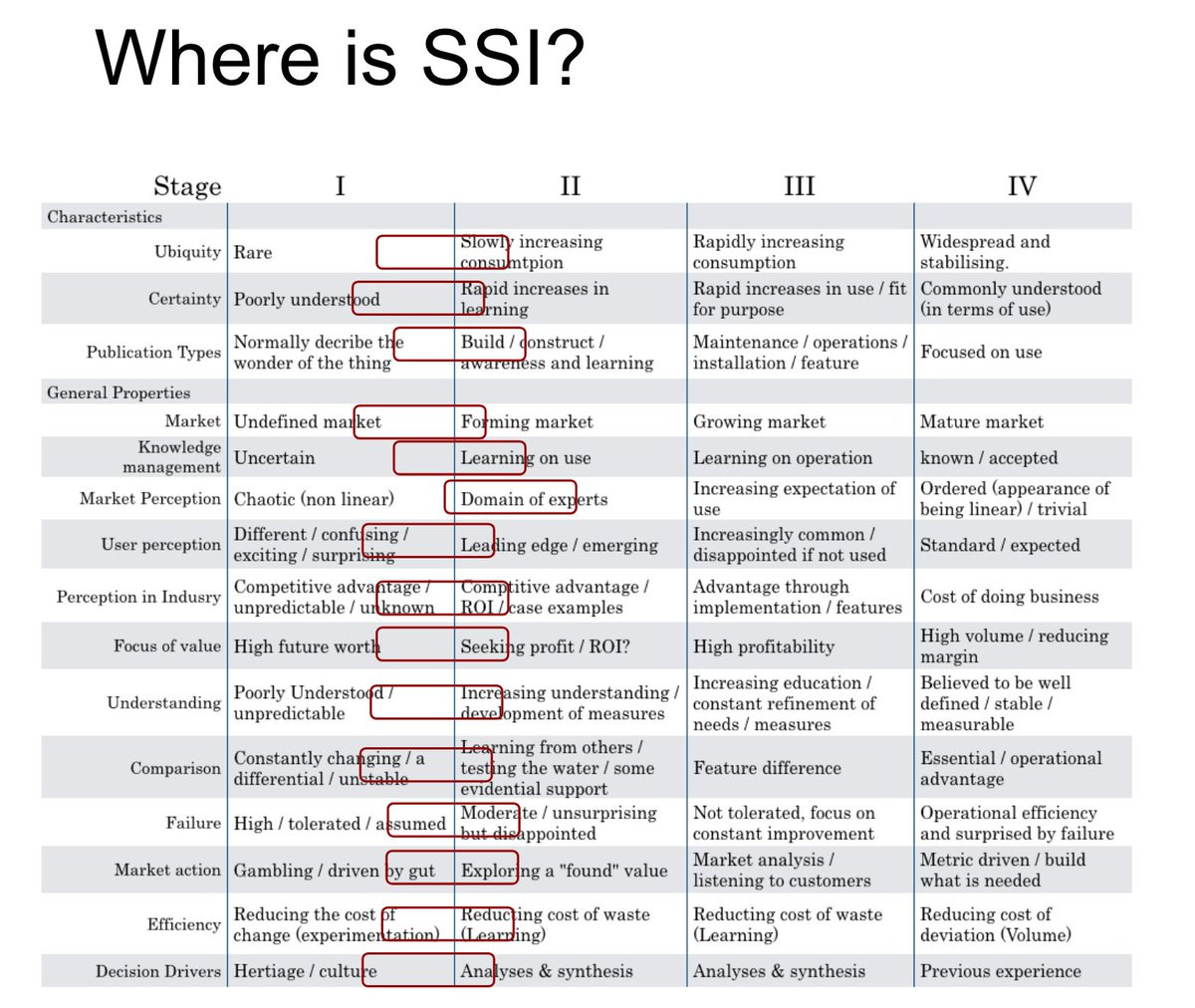
Darrell O'Donnell tweets
Some early thinking about where #SSI is under @swardley model of Genesis -> Custom -> Product -> Utility. We've come a long way, but we are still in the earliest of stages.
Indicio launches blockchain-enabled network for identity
“Our clients asked for a stable, fully-staffed network based on Hyperledger Indy— one that could provide the Service Level Agreements their customers need for mission-critical workloads,” said Heather Dahl, CEO of Indicio. “Today, we are excited to announce that this MainNet is open for business.”
“This is the network we need to accelerate adoption of passwordless zero trust ecosystems for enterprise customers” said Mike Vesey, President of IdRamp, a leader in decentralized identity and a Genesis Node Operator on the Network.
Swiss doing SSI
Underpinned by our country’s values, DIDAS is the Swiss ecosystem with the goal to enable an inclusive, privacy-first & frictionless future for our society’s Digital & Data needs. We are advocating for global standards with local governance for digital identities and data sovereignty.
Delegatable Credentials Now Available
An issuer may grant delegation authority to another issuer simply by issuing them a vcdm credential. Let's say did:ex:a wants to grant delegation authority to did:ex:b. did:ex:a simply issues the credential saying that did:ex:b may make any claim.
{"@context": [ "https://www.w3.org/2018/credentials/v1" ],"id": "urn:uuid:9b472d4e-492b-49f7-821c-d8c91e7fe767","type": [ "VerifiableCredential" ],"issuer": "did:dock:a","credentialSubject": {"id": "did:dock:b","https://rdf.dock.io/alpha/2021#mayClaim": "https://rdf.dock.io/alpha/2021#ANYCLAIM"},"issuanceDate": "2021-03-18T19:23:24Z","proof": { ... }}
Commerc.io srl has concluded the project with Essif on anti-money laundering eKYC
[ComKYC] is a protocol on the Commercio Network blockchain that allows you to issue a KYC verifiable credential after performing a simple set of payments through a bank or any regulated money institution. We piggy back on banks kyc requirements [...] We have created the first portable derivative key kyc credential protocol that will eliminate the endless passport upload for users, reduce customer dropouts for companies, and reduce time and cost for onboarding new customers
Blockchain Brad Interviews Ingo Rübe: Essential Credentials for Web 3.0 KILT (Part 2)
Part 1 of Brad Laurie’s wide-ranging conversation with Ingo Rübe covers the below topics (PDF).
Credentials • Identity • Use Cases for Verifiable Credentials • Sovereignty • Trust & Truth • Anonymity • Social KYC • Open Source • A Universal Protocol • Decentralized Identity Foundation • Ingo’s Background • KILT Use Cases • Why Polkadot? • XCMP and Polkadot Relay Chain • Ecosystem Collaboration
From the CCG Mailing List
Re: How to verify the did:key document is authorized by the private key holder ... JWS?
Manu responds:
On 3/18/21 8:24 PM, Stefan More wrote:
> Thus, there is no need to sign the DID doc by design. Or am I missing something?Correct. did:key DID Documents are purely generative things... if you know the did:key value, you have everything you need to:
1) Generate the DID Document, and
2) Verify that any signature created by that did:key was generated by the controller of that key.In other words, this is a cryptographic public key:
did:key:z6MkpTHR8VNsBxYAAWHut2Geadd9jSwuBV8xRoAnwWsdvktH
and that's all you need to verify a signature.
W3C DID Core 1.0 enters Candidate Recommendation stage
Manu Writes:
The W3C DID WG has also communicated that the specification is stable enough to collect implementation experience from the global implementer community. Once the WG collects enough implementation experience, it may then make final adjustments before publishing the v1.0 global standard, which is expected at the end of September 2021.
Literature
Major new Privacy Paper
Privacy Harms • Daniel Solove
Courts struggle with privacy harms because they often involve future uses of personal data that vary widely. When privacy violations do result in negative consequences, the effects are often small – frustration, aggravation, and inconvenience – and dispersed among a large number of people. When these minor harms are done at a vast scale by a large number of actors, they aggregate into more significant harms to people and society. But these harms do not fit well with existing judicial understandings of harm.
This article makes two central contributions. The first is the construction of a road map for courts to understand harm so that privacy violations can be tackled and remedied in a meaningful way.
Self-Sovereign Identity for IoT Devices
Nataliia Kulabukhova, Andrei Ivashchenko, Iurii Tipikin, and Igor Minin
in our point of view, a lot of development groups are working in parallel on the similar topics, yet it is not clear what is going on inside. In this paper we will try to define the differences and discuss both pros and cons of using such commonly known technologies as Sovrin based upon the Hyperledger Indy technology, Civic, Jolocom, uPort and some others. Besides, we’ll tackle the idea of using the SSI for inanimate object and how it can be constructed in this way.
Covid News
Architecture for Covid-19 Vaccine Passports
As they explain here, their National Clinical Data Store (NCDS) is storing vaccinations data and being made accessible to healthcare staff, via their VMT app.
“Under the bonnet, the VMT sends copies of the records of immunisations to the NCDS. For those that may be interested, this is achieved using a “FHIR API” based on the UK FHIR Core Immunisation Profile. A FHIR API is essentially an industry standard way of sharing digital health data. The NCDS can then securely share citizens’ immunisation history records to other services, again using a FHIR API.”
As we’ll explore in the upcoming and future webinars, Scotland’s opportunity is to build upon this core innovation through a collaborating community, a Digital Healthcare Ecosystem, to flesh it out in multiple directions including ways to expand user uptake and to enable new scenarios for how users interact with and update data.
The EU Digital Green Certificate Program: Analysis & Comparison
The EU approach does not support selective disclosure, i.e. allowing a subset of attributes from a credential to be used without revealing all the data in the credential.
Getting Privacy Right with Verifiable Health Credentials
Verifiable health credentials have never been more important or more urgently needed. Yet, as an industry, we have a responsibility to ensure that the solutions we deploy today are held to the highest bar and set the right precedent for personal data privacy.
MyData
Why 2021 is shaping up to be an exciting year for Regtech and data exchange
Joanne stated the company’s aim is to extol the benefits of giving app developers rapid ability to create hyper-personalised services built on ethical data with ingrained consent controls and privacy-by-design principles. Crucially, a lot of ADX’s efforts are going into making it clear to fintechs and innovators that fundamental backend system services already exist, and are ready to be utilised to fast track new products and services into the market today, not in some mythical future.
Achieving Change At Scale
This is the third in a series of blogs providing edited extracts from Mydex CIC’s response to the UK Government consultation around a new National Data Strategy.
The first focused on how to unleash the full potential of personal data, the second on why every citizen should be provided with their own personal data store. This blog explains why this strategy can be quick and easy to implement.
To catch up on progress on our Macmillan My Data Store Pilot click here.
Identity Not SSI
Facial Biometrics – Voluntary vs. Involuntary
we find that most, if not all of the ethical debate centers on how the biometrics are used and, more specifically, whether the biometric is used Voluntarily or Involuntarily.
OAuth 2.0 JWT Secured Authorization Request (JAR) updates
After the OAuth 2.0 JWT Secured Authorization Request (JAR) specification was sent to the RFC Editor, the IESG requested an additional round of IETF feedback. We’ve published an updated draft addressing the remaining review comments, specifically, SecDir comments from Watson Ladd. The only normative change made since the 28 was to change the MIME Type from “oauth.authz.req+jwt” to “oauth-authz-req+jwt”, per advice from the designated experts.
Financial-grade API (FAPI) 1.0 Final Specifications Published
This is a true accomplishment for open banking initiatives worldwide. The Foundation couldn’t have reached this important milestone with the FAPI specification without the leadership of the FAPI Working Group led by Chairman Nat Sakimura, Anoop Saxena (Intuit), Dave Tonge (MoneyHub), and a diverse group of experts with the technical chops, persistence and patience for the painstaking work of open technical standards development.
Using WebAuthn to Secure Your Digital Life
WebAuthn is an exciting technology, maximizing security without sacrificing user experience
As of January 2021, all major browsers like Chrome, Edge, Firefox, and Safari now support the Web Authentication API meaning we now have the ability to use Public Key Cryptography to register and authenticate users instead of passwords!
Thanks for reading
We’ll see you next week! Be sure to sign up on Patreon to support the creation of this newsletter and receive our first edition of the Identosphere Quarterly.