Identosphere 243 Aug 31-Sept 7: Agentic Internet Workshop Oct 24 • DIF-Trusted Agent WG • DCC reports re: EDU sector • Research DIDComm in Telco?
This is the weekly Identosphere Newsletter sharing highlights from around the web covering Decentralized and Self-Sovereign Identity curated by Kaliya Young, Identity Woman.
UpComing
Identity Week America, September 10-11, Washington DC [Link for Free Ticket] (Kaliya will be moderating a decentralized identity panel there)
Agentic AI Massive Open Online Course hosted by UC Berkeley begins September 15th
International Conference on Digital Identity, Digital Wallets and AI, October 21, Edinburgh, Scotland
Internet Identity Workshop #41 October 21-23 Mountain View California
Agentic Internet Workshop* October 24th Mountain View California (*Inspired IIW by and hosted by the IIW Foundation )
Agents and Identity
DIF Launches New Trusted AI Agents Working Group
DIF is launching the Trusted AI Agents Working Group, chaired by Nicola Gallo, Andor Kesselman, and Dmitri Zagidulin, to define an interoperable stack for trustworthy, privacy-preserving, and secure AI agents.
The initial focus of the group will be exploratory and experimental, starting from use cases and a taxonomy of delegation mechanisms and patterns. The first formal work item will be a report evaluating use cases for agents (that make explicit dynamics of authorization), primarily focusing on the object capability school of distributed authorization.
(Heather Flanagan) Roads, Robots, and Responsibility: Why Agentic AI Needs Identity Infrastructure
* Identity isn’t just a login box
* The right questions lead to better systems
* Protocols are evolving but identity hasn’t caught up
* Why this can’t be proprietary
* What to do now—before the collapse
(dock labs) 5 Identity Gaps That Put AI Agents at Risk
1. Agent Identity
2. Delegation
3. Reputation
4. Human Identity Without Real-Time Presence
5. Legal Consent
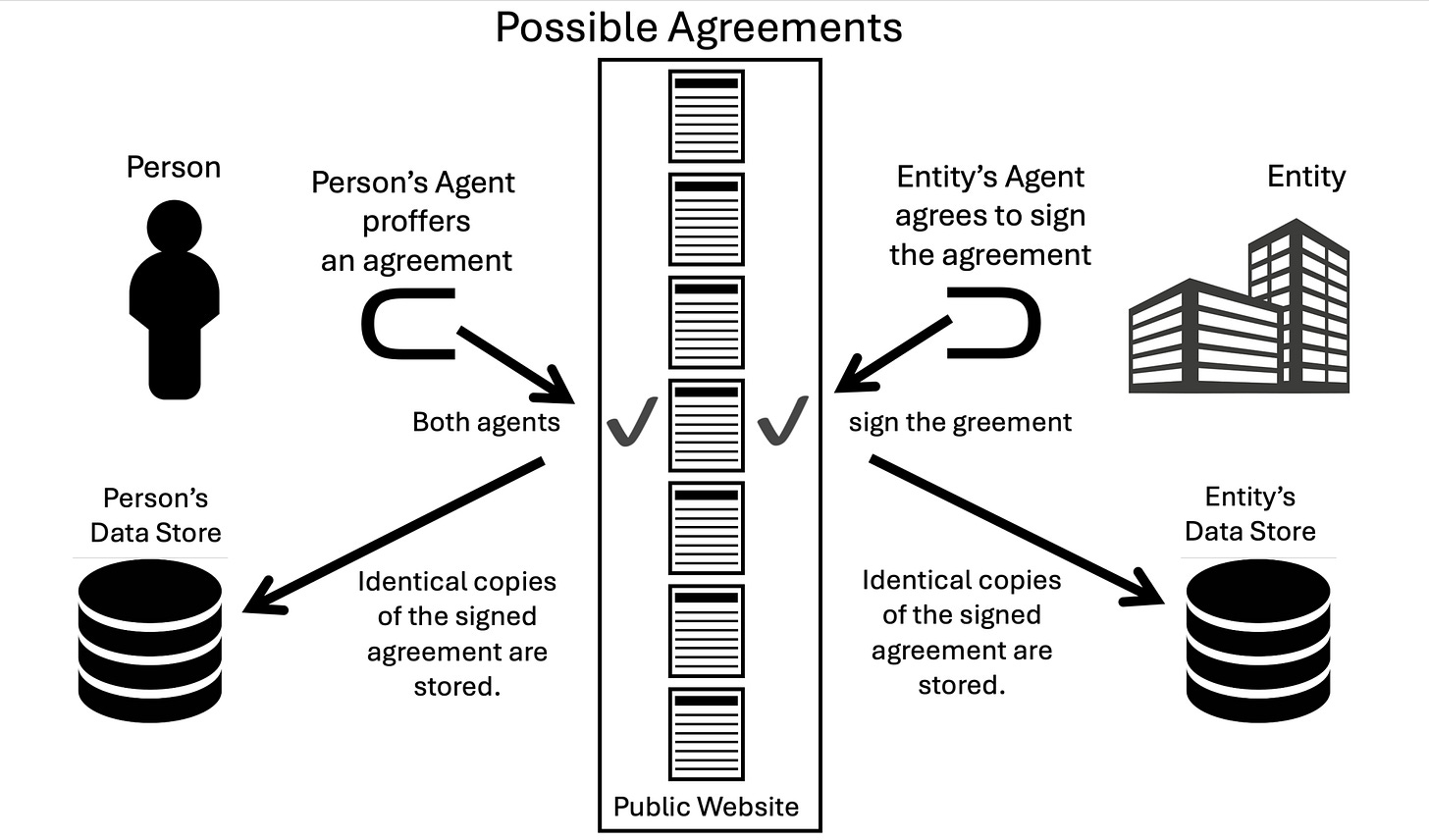
(Doc Searls) Protocols for MyTerms
MyTerms (IEEE P7012 Draft Standard for Machine Readable Personal Privacy Terms, unpacked here) has a simple conceptual structure that is open to many different protocols and roles for them. Note the arrows in this graphic:
C2PA - Privacy Analysis
[Report] Privacy, Identity and Trust in C2PA A Technical Review and Analysis of the C2PA Digital Media Provenance Framework
This report is a technical review and analysis of the C2PA technical framework that connects digital media content such as images, video, audio and documents to data about the origins of and changes made to that content. C2PA is designed to undergird media infrastructures with detailed, automated, encoded and shareable data and trust signals about media and its creators. In its analysis of C2PA, this report considers and discusses C2PA use cases and interactions with data privacy, identity and trust in digital information ecosystems. C2PA is an abbreviation for the Coalition for Content Provenance and Authenticity, which developed the framework.
Thoughtful
(Lockstep) Comparing Three Party and Four Party data verification models
The fourth party onboards data receivers (just like acquiring banks onboard merchants into the card systems), executes a standard form of contract with them, and supports them with metadata (credential descriptors, accreditation information, public keys etc.).
The fourth party is the missing link in scalable systems of verifiable credentials.
Verifiable credentials cannot verify themselves. That is, the verification step requires essential metadata which need to be distributed to relying parties.
Organizations
Join DIF Leadership: Executive Director & Steering Committee
This is your opportunity to shape the future of DIF! We have an upcoming Steering Committee election (6 seats open) AND we're accepting applications for the next Executive Director term! Current ED Kim [Hamliton-Duffy] falls sway to the siren call of building, we have an exciting opportunity to set the direction of DIF! We are accepting applications now. See application details here,
(Velocity Network) Enabling the Golden Age of Workforce Data
The success of modern workforce strategies depends on the development of a unified data layer that allows education, employment, licensure, and skills information to move seamlessly across stakeholders.
(MyData) Why a decentralised web index puts people first?
Timpi is building a people‑first discovery layer: a decentralised web index run by the community, private by design, and accessible to developers who want to create new services that respect users. It’s a practical way to turn human‑centric principles into everyday tools.
AI Usage Issues
(MySudo) How to stop your personal data from being used to train AI
* 12 AI privacy threats—and counting
* Artificial intelligence (AI) is the ultimate data broker
* Auto opt-in to AI training is a big issue
* How to protect your personal information from AI
* How MySudo protects your personal information from AI
Company News
How to Create Government-Issued Digital Identities using Truvera [Demo]
Most interactions with local government still rely on paper forms, manual checks, and brittle PDFs. In this demo, Richard Esplin (Head of Product at Truvera) shows how a city can issue a digital residency credential and then use it to verify eligibility across departments—from getting a library card to scheduling trash pickup—using verifiable credentials.
Indicio to advance trusted digital identity with APTITUDE, Europe’s newest Large Scale Project for digital wallet travel and payments
APTITUDE, one of the newest Large Scale Pilots backed by the European Commission, has officially launched, marking a major milestone in the EU’s drive to equip 80% of residents with a digital identity wallet by 2026 and setting out to prove how digital wallets can transform travel and payments across Europe.
(EverCRED) How EveryCRED align with SSI and DID for SMEs
SSI and DID are no longer just for large enterprises. The same trust and security frameworks can now be used by SMEs without the heavy costs or complexity.
With EveryCRED, small and mid-sized businesses get the tools to manage identity, build compliance, and earn customer trust. All without needing deep technical expertise or massive IT budgets.
For SME founders, compliance managers, and IT leads, the message is clear: identity can be a growth driver, not a roadblock.
Reports from Credential Engine and Digital Credentials Consortium
[Blog Post] Issuer Identity Registry Research Report and Governance Framework for Issuer Identity Registries
[Report] Governance Framework for Issuer Identity Registries
This report documents a joint research effort by Credential Engine and the Digital Credentials Consortium to explore, design, and test issuer identity registries—digital, structured directories that confirm the legitimacy of organizations authorized to issue credentials. These registries do not issue credentials themselves. Instead, they provide a foundational layer of trust for verifying the identity of credential issuers in ecosystems that use verifiable credentials, such as Learning and Employment Records (LERs).
[Report] Issuer Identity Registry Research Report Designing Trust Infrastructure for W3C Verifiable Credentials Being Used for Learning and Employment Records
This report documents a joint research effort by Credential Engine and the Digital Credentials Consortium to explore, design, and test issuer identity registries—digital, structured directories that confirm the legitimacy of organizations authorized to issue credentials. These registries do not issue credentials themselves. Instead, they provide a foundational layer of trust for verifying the identity of credential issuers in ecosystems that use verifiable credentials, such as Learning and Employment Records (LERs).
Education
(extrimian) How to Protect Students Data: Digital Diplomas & Credentials
With Extrimian, the university issues tamper-proof digital credentials, offers one official page to verify them in seconds, and uses AI internally to spot risk and speed corrections. Students get control and privacy; employers get instant answers; staff spend less time on inbox ping-pong. It’s security and simplicity, together.
Research
Secure and Trustful Cross-domain Communication with Decentralized Identifiers in 5G and Beyond
This paper proposes the application of W3C-endorsed Decentralized Identifiers (DIDs) to establish secure and trustful communication channels among network functions in 5G and subsequent generations.
[Battery Tracing] A GAIA-X-Aligned, Blockchain-Anchored Privacy-Preserving, Zero-Knowledge Digital Passport for Smart Vehicles
[Event Report] OwnYourData @ Semantics 2025: Privacy-preserving Data Sharing for Renewable Energy Communities
On September 3, 2025, we took part in Semantics 2025 in Vienna – specifically at the 2nd NeXt-Generation Data Governance (NXDG) Workshop. Together with our partners, we presented results from a current research project:
Identity not SSI
(Auth0) Dealing With Non-Human Identities
* Non-Human Identities and the Rise of AI
* Top Security Challenges with NHIs
* Best Practices for Managing Non-Human Identities
* The Future is Non-Human