Identosphere 257: DEC 1-7: New DIF ED •Digitizing Vital Records • Trust Engineering Digital Death • The Computational Pressure on Personhood • Ethereum on Decentralized Identity
This is the weekly Identosphere Newsletter sharing highlights from around the web covering Decentralized and Self-Sovereign Identity curated by Kaliya Young, Identity Woman.
Welcoming Grace Rachmany as DIF’s New Executive Director
Grace has been deeply involved in building communities around decentralized technology that prioritize individual rights and human agency. She brings a rare combination of governance expertise, practical execution, and a deep understanding of how people collaborate in decentralized environments. I’m especially excited about her commitment to global outreach.
Ethereum Publishes: Decentralized Identity
Digital Credentials
(SpruceID) Highlights from NAPHSIS: Building the Next Layer of Digital Verification for Vital Records
His presentation, Identity, Privacy, and Trust: Building the Next Layer of Digital Verification, outlined why verifiable digital credentials (VDCs) are rapidly becoming essential public infrastructure, and how states can implement them in a secure, privacy-preserving, and interoperable manner.
(SpruceID) How Does Multi-Format Issuance Future-Proof Digital Credentials?
As states modernize digital identity programs, one architectural decision stands above the rest: what credential format to issue. But here’s the reality, there’s no single format that works everywhere. Airport security, online age verification, healthcare check-ins, and cross-border transactions each rely on different ecosystems. Issuing in only one format means leaving residents stranded when they step outside that ecosystem.
Testing is at the heart of EUDI Wallets Launchpad 2025
The EUDI Wallet Launchpad Testing track aims to bring together different actors involved in the development, testing, and roll-out of the European Digital Identity Wallet ecosystem. Participation is open to all Member States and associated stakeholders contributing to the EUDI framework implementation process, regardless of their current level of technical maturity.
Trust
Trust Engineering
The second- and third-order consequences of AI are still a weak signal in most security and privacy conversations. System-1 thinking remains dominant: defense, fear, compliance checklists, guardrails, and higher walls. A faster-developing System-2 signal is now emerging: the privatization of trust and the discipline of Trust Engineering.
(Sankarshan) The Political Economy of Trust Registries
Digital trust stacks are often described as a set of modular components: identifiers, verifiable credentials, wallets, protocols, assurance frameworks. In that diagram, trust registries are usually drawn as a small box somewhere in the background, labelled “directory of issuers” or “list of authorities.” The visual rhetoric is deliberate, and it is misleading: it suggests that registries are supporting utilities rather than centres of power.
(Sankarshan) The Computational Pressure on Personhood
The danger of being known without being understood lies not in the volume of data collected but in the assumptions embedded in its interpretation. Digital systems misread complexity as inconsistency, nuance as noise, and context as risk. They see too much and understand too little. This imbalance produces structural inequity because the system’s misunderstandings are expressed as rules, flags, or scores that determine real-world outcomes.
Digital Trust Is Not Engineered — It Is Negotiated: Trust Lives in the Space Between Security, Privacy, and Safety
Trust is created not by choosing privacy, safety, or security alone, but by balancing them in everyday decisions — whether it’s journalists protecting sources while relying on oversight, parents setting boundaries without invading a child’s privacy, or banks preventing fraud without collecting excessive data. Trust emerges when no single value overwhelms the others.
AI and Identity
Dick Hardt on MCP Security
This is the first installment of my conversation with Dick Hardt, covering his thoughts on agentic security and his work on Agent Auth (AAuth). We’ve edited the interview for readability and clarity.
(David Birch) Digital Public Infrastructure and Agents
We need to extend digital public infrastructure to AIs.
I have to say I agree with him wholeheartedly about this, and also see his view that agents will soon conduct “most” economic transactions as far from hyperbolic. And I’m not the only one. Craig DeWitt, from Skyfire (who are building agent-agent infrastructure) makes a similar point:
“AI has payment and identity requirements that are different from anything we’ve seen before”.
He goes on to talk about the paradigm shift here, meaning that we are looking at an entirely new approach to how agents will access and pay for services.
Death
(Interview w/ Dean Saxe) Life, death, and online identity: What happens to your online accounts after death?
This emerging area of asset management remains in its early stages, facing a complex technological landscape, fragmented (or nonexistent) legal frameworks, and significant systemic gaps.
To address these challenges, the OpenID Foundation (OIDF) has been developing a new whitepaper and a digital estate planning guide that examine this issue on a global scale.
Kenya just sold 25 years of citizen health data for $20 per person.
Kenya signed a 25-year agreement giving the US unprecedented access to:
👉 Personal medical records
👉 Genetic information
👉 Lab samples
👉 Insurance details
👉 Digital health platforms
The price? $1.6 billion over 5 years.
EU’s data policy overhaul: what’s missing, what’s next, and four big ideas that matter
November 19 was a big day for EU data policy. It saw the release of the European Data Union Strategy (now reframed to pursue data for AI), the Digital Simplification Omnibus (proposing simplifications and reforms across multiple acts and directives), and a Digital Fitness Check call for evidence (to review how the entire body of regulation on digital “affects and supports the competitiveness objective of the EU”).
(LFDT/Indicio) [Case Study] Open source flywheel: Indicio turns leadership in the LF Decentralized Trust community into credibility, growth, and global reach
The founding team chose to focus on community leadership rather than traditional marketing. Indicio built its flagship offering, Indicio Proven, directly on technologies openly developed by LF Decentralized Trust and, in some cases, now OpenWallet Foundation communities, including Aries Framework, ACA-Py, Credo, Hyperledger AnonCreds, Hyperledger Indy, and Trust Over IP.
(DIACC) From Trust to Growth: The Business Case for Digital Client Verification in Open Banking and Lending
The Digital ID and Authentication Council of Canada (DIACC) convened an industry workshop in Montreal focused on exploring the business case for digital trust in open banking and lending. The session brought together stakeholders from government, financial services, technology providers, and legal sectors to examine how digital client identity verification (IDV) can drive measurable value while mitigating fraud and enabling growth.
(OIDF) Public Review Period for Proposed OpenID Federation 1.0 Final Specification
A Final Specification provides intellectual property protections to implementers of the specification and is not subject to further revision. This note starts the 60-day public review period for the specification draft in accordance with the OpenID Foundation IPR policies and procedures.
FIDO Alliance Launches New Digital Credentials Initiative to Accelerate and Secure an Interoperable Digital Identity Ecosystem
The FIDO Alliance announced today the launch of a new digital credentials initiative, marking an expansion of its mission to accelerate the adoption of verifiable digital credentials and identity wallets. This initiative is poised to help the world simplify and secure online and in-person interactions by establishing a trusted, and interoperable identity wallet ecosystem.
(Indicio) Verifiable Credentials strengthen AML compliance, KYC for digital assets and finance
To:U.S. Department of the Treasury.
Subject: Request for comment, Innovative Methods To Detect Illicit Activity Involving Digital Assets
Thoughtful
Robots, Humans, and the Edges of the Open Web
A week later, at the W3C TPAC meetings in Kobe, Japan, I ended up in an almost identical conversation, hosted again by Mark and David, fortunately a somewhat larger room. That discussion brought in new faces, new community norms, and a different governance culture, but in both discussions, we almost immediately fell to the question:
Digital Identity, Tokenization, and the Burning Platform
Digital Identity in the context of Asset Tokenization provides the necessary trust fabric and helps in regulatory compliance for asset tokenization to unlock dormant capital. Tokenization is the process of issuing digital representations of assets on a programmable ledger. A game changer because of the below:
Updates
VeriMe Cooperative
VeriMe is a membership cooperative dedicated to researcher identity verification. Worldwide.
We provide researchers digital identity verification services that enable verified access to research systems, facilities, and workflows without exposing personal data.
ASEAN ID Update
Brunei has softly launched BruneiID (with a cool website: https://lnkd.in/gaSYXZXQ) and Indonesia has made improvements to IKD. I’ve also added Malaysia’s MyGOV app, which includes a wallet, while myDigitalID is an authenticator.
Research
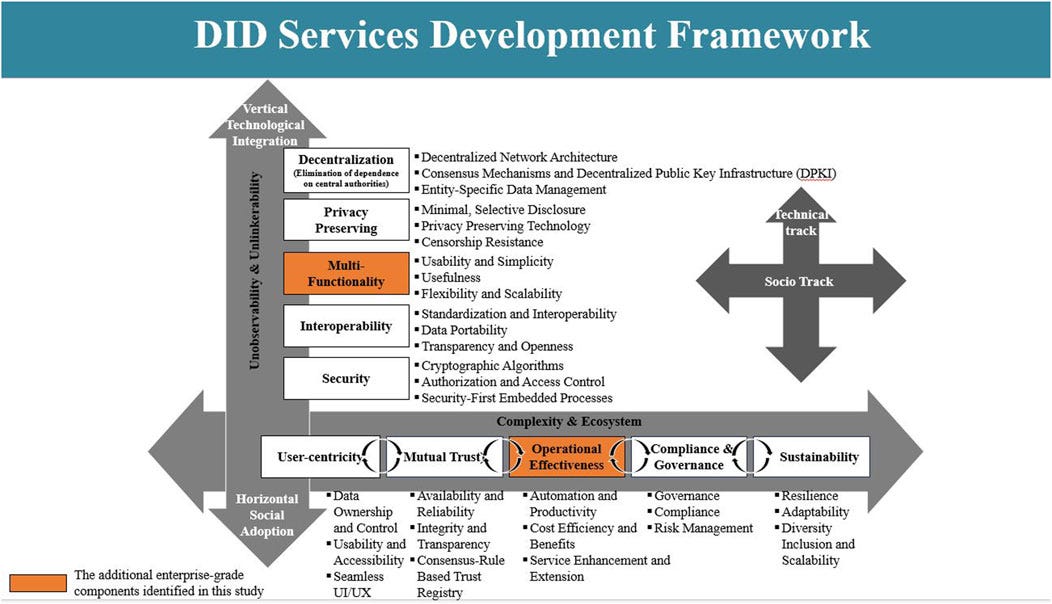
[Reserch] Towards a refined architecture for socio-technical decentralized identity services
While blockchain-based Decentralized Identity (DID) services are increasingly recognized as foundational for secure, user-controlled identity management, existing implementations remain predominantly technology-focused and overlook critical socio-technical factors such as governance, usability, and stakeholder trust. This study addresses this gap by proposing an STS-based (Socio-Technical Systems) framework that integrates social and technical components, validated through expert consultation, and introduces a Refined DID Service Architecture for enterprise deployment that balances technological robustness with social acceptance while addressing key adoption barriers like interoperability gaps and regulatory inconsistencies.
[Research] Designing and implementing the trust diamond for verifiable and privacy-preserving data sharing: engineering energy flexibility provision
This study addresses the tension between data verifiability and privacy in electricity grid operations—where grid operators need verifiable data from small-scale flexibility devices while owners seek data protection—by designing a Flexibility Provision Data Flow and digital Trust Diamond using wallet-based identity management. Through Action Design Research, the authors develop two design principles (Verifiability through Delegation and Mediated Sovereignty) and propose a Decentralized Flexibility Provision Architecture that demonstrates practical scalability in laboratory and field tests, enabling privacy-preserving yet verifiable data sharing for decentralized grid flexibility and Redispatch measures.
[Research] A Security and Usability Analysis of Local Attacks Against FIDO2
In this paper, we explore threats from local attacks on FIDO2 that have received less attention---a malicious browser extension or cross-site scripting (XSS), and attackers gaining physical access to an HSK. Our systematic analysis of current implementations of FIDO2 reveals four underlying flaws, and we demonstrate the feasibility of seven attacks that exploit those flaws