Identosphere 259 Dec 14-19: 2025: Kim Duffy signs out of DIF • The Seven Sins of European Digital Identity • Two APIs Walk Into a Browser • AI Agent Registry Research
This is the weekly Identosphere Newsletter sharing highlights from around the web covering Decentralized and Self-Sovereign Identity curated by Kaliya Young, Identity Woman.
Upcoming
Call for Papers Open Now Open Identity Summit Deadline: January 31st, 2026
The summit takes place May 21–22, 2026 at University of Applied Sciences Dresden (HTW Dresden) in Dresden, Germany
Protocols for Publishers PfP✨ London on Feb 4-5, 2026 to discuss how we can preserve an open, equitable web, where no one company holds the keys.
MOSIP Connect, Rabat Moroco, Feb 11-13. Feb 13th is an unconference day facilitated by Kaliya. Reach out to me for an invite.
Join us at the 1EdTech Digital Credentials Summit in Philadelphia, February 18-20, 2026.
DIF Unconference Africa (an IIW Regional Event) Feb 24-26, 2026 Cape Town
Internet Identity Workshop #42, April 28-30, 2026, Mountain View California
Agentic Internet Workshop #2, May 1, 2026, Mountain View California
dice: Digital Identity unConfernece Europe, June 22-24, Copenhagen, Denmark
Goodbye from Kim Duffy: From the [DIF] Executive Director
SpruceID at the SEC Roundtable: Advancing Privacy-First Digital Identity
This week, SpruceID Founder and CEO Wayne Chang participated in the U.S. Securities and Exchange Commission’s Roundtable on Financial Surveillance and Privacy, sharing perspectives on the role of digital identity in modern financial systems.
Europe
(Dyne) The Seven Sins of European Digital Identity (EUDI)
I want Europe to be excellent to all its citizens. We should develop our technological solutions following a human-centric approach grounded on principles of privacy, fairness, and inclusion. The motivation behind EUDI is that of achieving strategic autonomy for our public and social services, but its realization goes in the opposite direction, effectively putting in the hands of mobile OS manufacturers core interaction channels with the institutions governing our society. As it is today, EUDI has lost my trust, and it does not deserve yours either.
Allez! The French 🇫🇷 📲 EUDI Wallet Sandbox is open for testing:
Get started here:
Documentation: https://lnkd.in/dCA_anzB
Access Form: https://lnkd.in/dPg5eu5i
New Version of EU Architecture and Reference Framework 2.7.3
The 📒”Yellow Pages” of the 🇪🇺 📲 EUDI Wallet ecosystem are live. eIDAS Dashboard
(Webinar) Advanced features of European Digital Credentials for Learning (EDC)
Statement on Canada-EU Digital Credentials and Trust Services MOU: International Alignment Benefits From Domestic Coordination
DIACC welcomes Canada and the European Union’s commitment to collaborate on digital credentials and trust services, formalized through the December 8 memorandum of understanding. International alignment matters deeply—for Canadian economic competitiveness, for secure cross-border transactions, and for ensuring our citizens can participate fully in the global digital economy.
EUDI in Practice: Inside Germany’s Digital Identity Strategy [Video and Takeaways]
In a recent webinar, we spoke with Mirko Mollik, Identity Architect at SPRIND (Germany’s Federal Agency for Breakthrough Innovation), to unpack how Germany is approaching the rollout of the EUDI ecosystem. The conversation went beyond high-level regulation and focused on the realities of implementation: how wallets will be certified, how issuers and verifiers will onboard, how privacy is enforced in practice, and which standards are truly mandatory.
Business Wallets and Organizational Identity: What the EWC Pilots Revealed
Unlike personal wallets, business wallets introduce a different set of requirements, structures, and challenges. The EWC pilots provided early insight into how these could function in real operational environments.
Digital Onboarding and Identity in Europe: The Next Frontier for Financial Services
Current LLM-based AI agents cannot establish differentiated trust when initiating cross-organizational dialogues, so this article presents a prototype using W3C DIDs and Verifiable Credentials to enable agent authentication and trust establishment, though LLM-controlled security procedures show limitations.
(European Data Protection Supervisor) [Tech Dispatch] The path towards a data protection by design and by default approach
The purpose of this TechDispatch is to introduce the concept of a DIW, understand the privacy risks that exist when using a DIW, and discuss relevant data protection by design and by default requirements and their implementation, including relevant technologies. Eventually, we assess how the European Digital Identity Wallet (EUDIW), mandated by the eIDAS 2 Regulation, fits within the framework outlined.
Germany’s eID cards issued without adequate identity verification
Gap in biometric IDV, doc verification enables fraudsters opening fake bank accounts
Thoughtful
(Bo Harald) How will AI change standardisation work?
- Semantic layers become the anchor
- Envelopes (JWT, SD-JWT, mdoc, COSE) become interchangeable wrappers
Exactly the direction you’ve been arguing for in EUDI / EBW / WeBuild:
VCDM + controlled vocabularies first, envelopes second.Trust standards become non-negotiable
AI cannot function safely without: verifiable identity, authority, provenance, evocation.
This makes trust infrastructure standards foundational: wallets, verifiable credentials, registries, governance rulebooks.
AI forces standardisation to confront lawfulness, accountability, and responsibility head-on.
(John Philips) Apple Citizens?
“Apple don’t just want you as their customer, they want you as their citizen” - that was the conclusion that I reached (and voiced) at the IBM TechXChange workshop session yesterday in Melbourne.
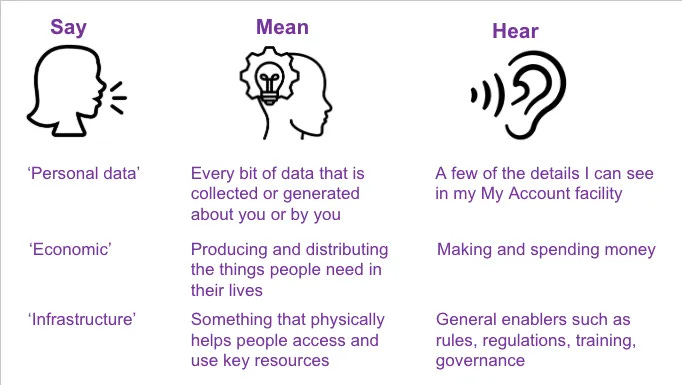
(Alan Mitchell) Why the words we use matter
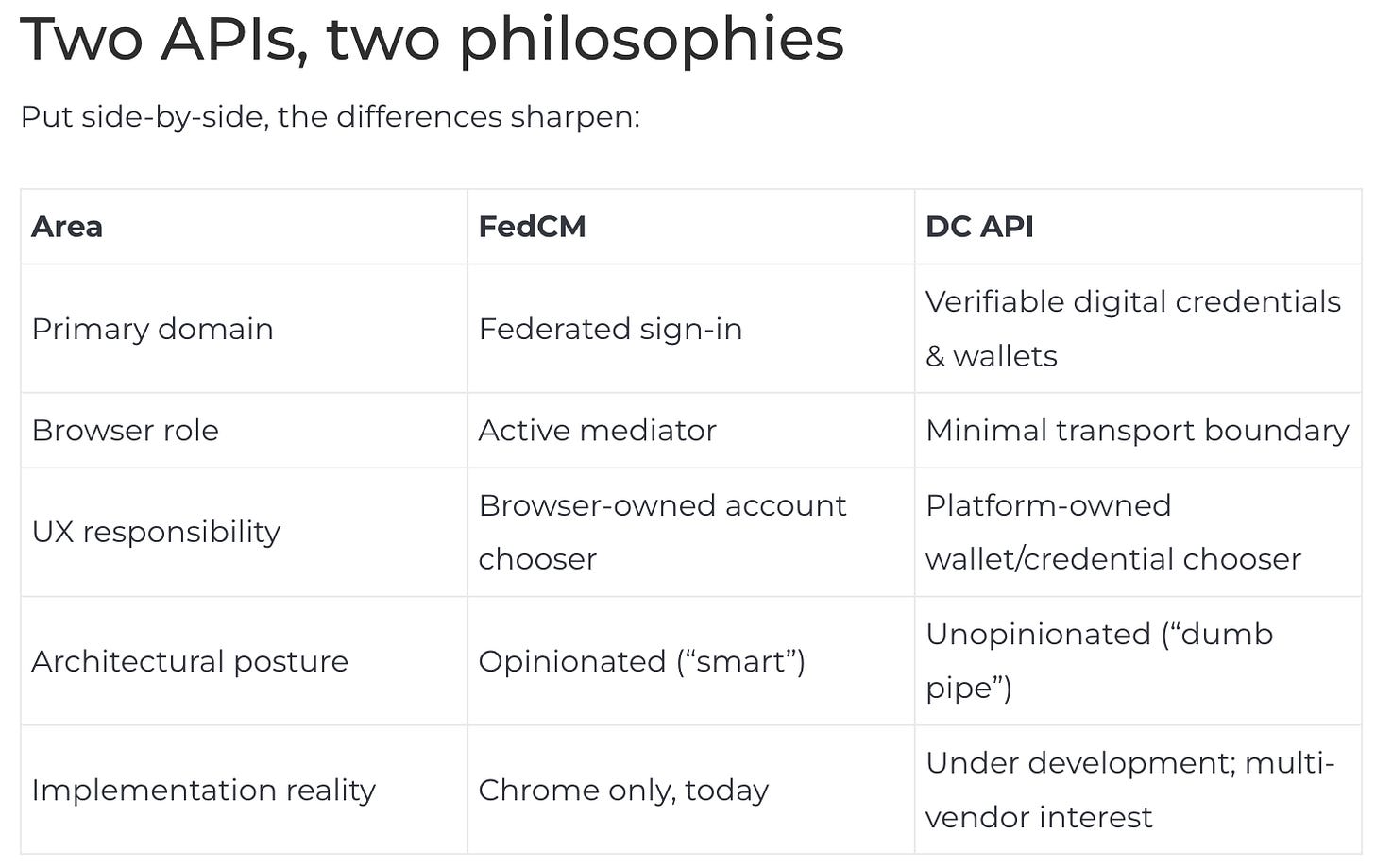
Two APIs Walk Into a Browser: FedCM vs. the DC API
AI and Identity
Human-in-the-Loop AI and Identity: Putting People at the Center of Machine-Driven Decisions
For identity and access management (IAM), HITL helps answer a growing question: How do we use AI to make smarter decisions without giving up control? The answer lies in balancing automation with human judgment, and identity is the anchor that makes that possible.
The Looming Authorization Crisis: Why Traditional IAM Fails Agentic AI
Where Current IAM Falls Short
Promising IAM Frameworks for Agentic AI
The stakes are high. Without a comprehensive plan for managing these agents—one that tracks who they are, what they can access, and when their permissions expire—organizations risk disaster through complexity and compromise. Identity remains the foundation of enterprise security, and its scope must expand quickly to shield the autonomous revolution.
Digital wallets & AI threats to reshape ID security
“The strategic takeaway for CISOs is clear: identity is no longer a directory entry; it is a dynamic security signal. Cyber resilience in 2026 hinges on building an ‘Identity-Runtime Mesh’ - uniting identity, zero trust, and real-time workload security to ensure accountability and control at speed.”
(Research) Evolution of AI Agent Registry Solutions: Centralized, Enterprise, and Distributed Approaches
Abstract—Autonomous AI agents now operate across cloud, enterprise, and decentralized domains, creating demand for registry infrastructures that enable trustworthy discovery, capability negotiation, and identity assurance. We analyze five prominent approaches: (1) MCP Registry (centralized publication of mcp.json descriptors), (2) A2A Agent Cards (decentralized self-describing JSON capability manifests), (3) AGNTCY Agent Directory Service (IPFS Kademlia DHT content routing extended for semantic taxonomy–based content discovery, OCI artifact storage, and Sigstore-backed integrity), (4) Microsoft Entra Agent ID (enterprise SaaS directory with policy and zero-trust integration), and (5) NANDA Index AgentFacts (cryptographically verifiable, privacy-preserving fact model with credentialed assertions). Using four evaluation dimensions—security, authentication, scalability, and maintainability—we surface architectural trade-offs between centralized control, enterprise governance, and distributed resilience. We conclude with design recommendations for an emerging Internet of AI Agents requiring verifiable identity, adaptive discovery flows, and interoperable capability semantics.
Year End Refelections + Year Ahead
The DIACC 2025 Annual Report
AI-generated fraud and misinformation threaten economic stability. DIACC’s work has never been more critical. Our new Canadian Digital Trust Adoption Dashboard provides unprecedented transparency into provincial programs. Our partnership with the SIROS Foundation positions Canada to leverage credentials for cross-border labour mobility.
2025 Reflections: Lessons from a Year of Acceleration
1. Fraud became more personal, adaptive, and believable
2. First-party fraud moved into the center of the P&L conversation
3. AI governance and data access control became operational necessities
4. KYC, AML, and financial crime teams made progress while facing higher stakes
5. Capital returned with clearer priorities and a higher bar
6: Age assurance moves from debate to implementation
Juniper Research names Indicio as a “Disruptor and Challenger” in 2025 Digital Identity Leaderboard
As digital identity threats evolve, independent market analysis shows Verifiable Credentials is the most powerful way to defend against AI deepfakes, synthetic IDs, and document fraud. Indicio’s inclusion in the report points to the strength of its market-leading decentralized identity solution, Indicio Proven®, and the pace of customer deployment.
2025 Community Awards: Recognizing Contributions from Across the LF Decentralized Trust Community
It’s that time of the year… Namirial predictions for 2026!
Research
[Research] Comparative Analysis of Traditional vs. Decentralized Identity Management: Security Implications for Enterprise Networks
This research compares centralized and decentralized identity management systems, finding that DIM frameworks using blockchain and DIDs offer superior security, privacy, and resilience against identity theft and unauthorized access, though they require careful enterprise integration.
[Research] Binding Agent ID: Unleashing the Power of AI Agents with accountability and credibility
BAID (Binding Agent ID) proposes a comprehensive identity infrastructure using biometric authentication, blockchain-based identity management, and zkVM-based code authentication to create verifiable, traceable accountability for autonomous AI agents by cryptographically linking operators to their agents’ code and execution.
[Research] AI Agents with Decentralized Identifiers and Verifiable Credentials
This article proposes equipping AI agents with self-sovereign digital identities using W3C Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs) to enable autonomous, cross-domain trust establishment at the start of agent-to-agent dialogues, though evaluation reveals limitations when LLMs solely control security procedures.
News
Digital Identity New Zealand Meri Kirihimete me te Tau Hou Hari
[LFDT] Building the foundations for a decentralized world: A decade of community, code, and market development at the Linux Foundation
Ten years ago today, the Linux Foundation launched its first blockchain-related project, the Hyperledger Project, a collaborative effort to “advance popular blockchain technology.” At the time, blockchain was largely viewed in the enterprise as an experimental technology. It was promising in theory, but unproven at scale, raising questions about security, performance, governance, and regulatory fit. It was often also conflated with cryptocurrency, which many institutions associated with volatility, regulatory uncertainty, and speculative use cases.
OpenID for Verifiable Credential self-certification to launch Feb 2026
The OpenID Foundation is pleased to announce implementers will be able to start self-certifying their implementations in February 26th 2026 for OpenID for Verifiable Presentations (OpenID4VP) 1.0, OpenID for Verifiable Credential Issuance (OpenID4VCI) 1.0 and High Assurance Interoperability Profile (HAIP) 1.0 implementations through the OpenID Foundation’s conformance testing platform.
IBM Verify Identity Access Digital Credentials <- company site
Connecting Learning and Work Worldwide: 2025 CTDL Recap
The opportunities provided by digital credentials make this work more essential than ever. In the United States alone, the Counting Credentials 2025 report identifies more than 1.85 million unique credentials, with an increasing share now digital. This reflects a global shift toward new forms of learning recognition. As digital credentials expand worldwide, the need for interoperable data becomes even more critical, reinforcing the benefits of CTDL.