Identosphere 261 Jan 2-Jan 9: NIST • Trust • New VC Charter @W3C • Biometric Data Discussion Group • Identity & AI
This is the weekly Identosphere Newsletter sharing highlights from around the web covering Decentralized and Self-Sovereign Identity curated by Kaliya Young, Identity Woman.
Upcoming New
Workshop: CREDEBL For Decentralized Identity and Verifiable Credentials, Wednesday, February 18 at 8 AM Pacific Zoom
Upcoming
These were all listed in previous newsletters
Call for Papers Open Now Open Identity Summit Deadline: January 31st, 2026
The summit takes place May 21–22, 2026 at University of Applied Sciences Dresden (HTW Dresden) in Dresden, Germany
Protocols for Publishers PfP✨ London on Feb 4-5, 2026 to discuss how we can preserve an open, equitable web, where no one company holds the keys.
MOSIP Connect, Rabat Moroco, Feb 11-13. Feb 13th is an unconference day facilitated by Kaliya. Reach out to me for an invite.
Join us at the 1EdTech Digital Credentials Summit in Philadelphia, February 18-20, 2026.
DIF Unconference Africa (an IIW Regional Event) Feb 24-26, 2026 Cape Town
Internet Identity Workshop #42, April 28-30, 2026, Mountain View California
Agentic Internet Workshop #2, May 1, 2026, Mountain View California
dice: Digital Identity unConfernece Europe (an IIW Regional Event) June 22-24, Copenhagen, Denmark
Standards
(NIST) Digital Identities: Getting to Know the Verifiable Digital Credential Ecosystem Post 2: Understanding mDL credential formats
(NIST) Digital Identities: Getting to Know the Verifiable Digital Credential Ecosystem Post 1 Overview.
[DRAFT] Verifiable Credentials Working Group Charter: Start Date 2026 April 1, 2026
The Working Group will deliver the following W3C normative specifications:
Verifiable Credential Render Method v1.0
Verifiable Credential Confidence Method v1.0
Verifiable Credential API for Lifecycle Management v1.0
Verifiable Credential Barcodes v1.0
Verifiable Issuers and Verifiers v1.0
Data Integrity BBS Cryptosuites v1.0
Verifiable Credentials JSON Schema Specification v1.0
Enhaced social protection through interoperability: ID systems standards released
Version 1.0.0 of the ID systems and SP-Systems Interoperability Standards is now available on Gitbook. The standards, endorsed by the USP2030 Partnership, adopt OpenID Connect (OpenID foundation) and Verifiable Credentials (W3C) as the technical foundation for interoperability. These open standards provide a secure and trusted framework that allows social protection systems to authenticate individuals and request reliable identity data—such as demographic attributes and authentication tokens—from ID systems in a privacy-preserving manner. This approach ensures that identity data can be exchanged safely while maintaining trust, security, and scalability.
(Kantara) Coming Soon – Biometric Data Discussion Group
The Biometric Data Discussion Group (Biometrics) will address the management, security, and privacy of biometric data, from collection to destruction, with a focus on practical application and GDPR compliance. While standards do exist, they are often inaccessible to non-experts, and there is a need to decode and translate existing standards into a straightforward, practical guide for real-world application. Biometrics will develop a set of recommendations and best practices for biometric data management to fill this need for use alongside existing standards.
Opt Out for Data Brokers
CA Gets the DROP on Data Brokers
Beginning in 2026, California residents can access the Delete Request and Opt-out Platform (DROP) and request data brokers delete their personal information – information collected from third parties or from consumers in a non-“first party” capacity (i.e., through an interaction where the consumer did not intend or expect to interact with the data broker).
In the Real World
[Podcast] How IATA is Building Trust for Nearly 400 Airlines (with Gabriel Marquie)
How does an airline instantly trust a travel agency on the other side of the world? And what does it take to enable a future where passengers move through airports with a seamless, contactless identity experience?
The SSI pitch that worked 2 years ago doesn’t work anymore.
Getting them to work in production when you’re processing millions of verifications? That’s where most implementations fall apart. Interoperability that goes beyond marketing slides. Your credentials need to work with ISO mdoc systems, OIDC4VC flows, and yes, even the SAML dinosaurs that half the enterprise world still runs on.
(SpruceID) How to Build a Digital ID People Actually Want to Use: 5 Lessons From the Field
Lesson 1: Anchor on Everyday Use Cases and Make Them Visible
Lesson 2: Get Big Names on Board Early
Lesson 3: Reduce Friction for Everyone
Lesson 4: Use Policy to Unlock Adoption
Lesson 5: Earn the Trust Dividend
(SpruceID) Digital Identity In America: Series Overview
An executive guide to SpruceID’s multi-part series on the future of digital identity in the U.S.
1. Foundations of Digital Identity
2. Policy Momentum: Why Governments Care Now
3. The Technology Powering Digital Identity
4. Privacy and User Control
5. Practical Digital Identity in America
6. Enabling Issuers of U.S. Digital Identity
7. Verifiers: Building Trust at the Point of Use
8. Digital Identity: End User Experience
(Heather Flanagan) Process, Standards, and the AI Rogue Wave: Notes from Gartner IAM
First, many organizations don’t really need a better product; they need a process they can sustain. Second, standards work is happening, but it’s largely invisible in the conversations where buying decisions take shape. And third, even as Gartner itself warned that the current AI hype is spiraling, the market continues to reward vendors for leaning into it anyway.
Identity and AI
The Key Issues in Agentic ID
That is why I have long made myself unpopular in the crypto world by maintaining that while not your keys, not your coins is a fun rallying cry for Bitcoin maximalists it makes absolutely no sense that people should be loaded with this responsibility. I like Adam Levine’s framing that while the idea of self-sovereignty in crypto is empowering it demands a “persistent competence” that I think is well beyond the capability and capacity of the average member of the public, and I include myself in that category.
What AI Agents Can Teach Us About NHI Governance
Agentic AI is a stress test for non-human identity governance. Discover how and why identity, trust, and access control must evolve to keep automation safe.
(Auth0) Model Context Protocol Nov 2025 Specification Update: CIMD, XAA, and Security
The Nov 25, 2025, specification update for the Model Context Protocol (MCP) is out.
For those of us working in Identity, this is the update that starts to solve the hard problems of connecting AI agents to real-world business data. It moves the protocol away from custom solutions and aligns it with standard OAuth patterns that developers and security teams already understand.
(Indicio) Why Verifiable Credentials will power real-world AI in 2026
AI systems are going to deliver business success in 2026, they must be able to safely access high-value data and act across organizational boundaries. To do this, systems and agents need to be:
- Identifiable
- Have access to structured and accurate data in a permissioned and auditable way
- Demonstrate that they have the delegated authority to share this data with other identifiable AI agents and systems.
Billions’ Know Your Agent - Identity and accountability for AI agents
Billions provides an Agent JS SDK that allows AI agents to generate and manage DIDs, perform authentication, and interact with the public attestation registry. The SDK supports LLMs with function calling and integrates with frameworks like LangChain.
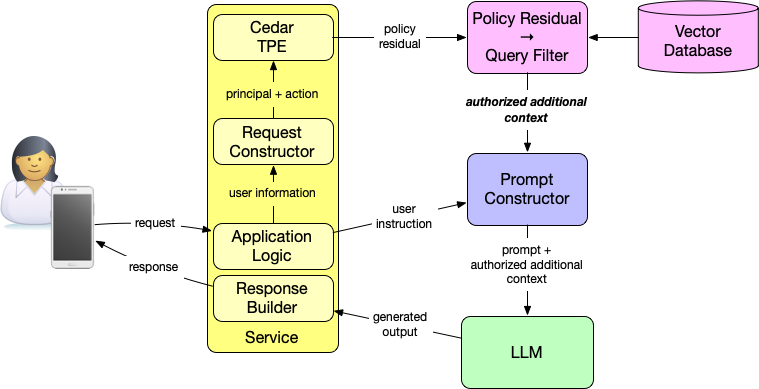
(Phil Windley) Authorization Before Retrieval: Making RAG Safe by Construction
(Phil Windley) What AI Can Tell You About Your Authorization Policies
Review and audit are different.
In review and audit, the intent is assumed to already exist. The policies are fixed. The question is no longer how authority should be expressed, but how it is already expressed and whether that expression can be understood, defended, and justified.
This difference matters because it changes how AI should be used. In authoring, AI is invited to explore alternatives. In audit, that permission must be taken away. The AI’s role shifts from collaborator to examiner: explaining behavior, enumerating scope, and surfacing consequences without proposing changes. The goal of a policy audit is not to optimize policies or propose fixes, but to understand what the current policy set allows, how broad that access is, and whether it can be defended as intentional.
(Phil Windley) Policy Authoring and Analysis with AI
AI doesn’t belong in the business of deciding who can access what, but it can be an effective partner in reasoning about authorization policies. When used inside clear guardrails, AI helps humans author, analyze, and refine policies without taking over access decisions.
[Podcast] Decentralized identity in the age of AI agents with Kaliya Young
In this episode, we sit down with Kaliya Young. Kaliya is widely known as the “Identity Woman” and is one of the earliest pioneers of decentralized and self-sovereign identity. With over 20 years in the field, Kaliya breaks down complex concepts like decentralized identifiers (DIDs) and verifiable credentials in practical, real-world terms.
Education
How The Open Group Uses Open Badges
The Open Group issues Open Badges to individuals who earn certifications, credentials, or other recognized achievements across its portfolio of programs. These badges:
- Provide a digital representation of an individual’s certification
- Include verifiable metadata about the achievement
- Allow certified individuals to share their credentials easily with employers, peers, and professional communities
- Support lifelong learning by enabling individuals to build a visible, portable record of their professional development
(Simone Ravaioli) REGEN: REfugeesGENeration - AI Can Transform How We Recognize and Empower Refugees
REGEN is a proposed AI-powered framework that would recognize and validate refugees’ informal skills and experiences through narrative analysis and issue verifiable credentials, transforming refugee recognition from a bureaucratic gatekeeping process into a pathway for empowerment and economic integration.
Trust and Other Things
Trust Services, Trust-as-a-Service, Trust-Enhancing-Technologies
In this context, its important to understand - Trust Services, Trust-as-a-Service, Trust-Enhancing-Technologies. Let us take 3 players across different domains to illustrate how things are evolving.
December 2025: Cross-Border Testing Proves Digital Identity Interoperability
December 2025: the EU’s EUDI Wallets Launchpad event in Brussels demonstrated that cross-border digital identity interoperability works through successful conformance testing between Member State wallets and relying party infrastructure. While the UK’s Digital Identity Trust Framework achieved statutory status with 48 certified providers and Ireland announced plans to use its 2026 EU Council presidency to push for EU-wide ID-verified social media accounts, the month’s defining moment was proof that the technical architecture can deliver on its interoperability promise.
Will Proof of Purchase (AKA e-receipt) become the highest-volume verifiable credential?
Now when general-purpose EBWs will be either mandatory or self-evidently useful for all enterprises (need it also for eg receiving job applications) it is time to restart the journey towards linespecific use of e-receipts. Better named Proof of Purchase verifiable credentials (PoPs) to underline the importance of so many wallet2wallet2wallet reuse opportunities.
Physical Badges with integrated Passkeys
How to build a Digital Credential Issuer (Developer Guide)
The future of authentication in 2026: Insights from Yubico’s experts
If you’ve followed us this year, you’ve read various posts from Yubico experts sharing their insights and expertise on the latest trends impacting cybersecurity around the world. We strive to post content that is insightful to not just our customers, but the businesses and individuals that are looking for information and actionable takeaways that can help them become truly cyber resilient in this digital world.
(Ethereum Leaders) The Trustless Manifesto
Authors: Yoav Weiss, Vitalik Buterin, Marissa Posner
Ethereum was not created to make finance efficient or apps convenient.
It was created to set people free — to empower anyone, anywhere to coordinate without permission and without trusting anyone they cannot hold accountable.