Identosphere #27 • Azure AD VC Demo • 7 Laws ID Standards • VC Use Cases
News and updates related to Verifiable Credentials, Decentralized Identifiers, and the quest to develop PKI-based identity infrastructure where people are in control over their personal information.
Welcome to Identosphere’s Weekly Update
If you haven’t already, you can subscribe and read previous issues at newsletter.identosphere.net.
Please support Identosphere on Patreon. Patron’s get special access to our quarterly report/summary. If you are new to the field this is a great resource highlighting the best of our coverage for the past 6 months.
Coming Up
The EOSIO Identity Working Group - Kickoff • April 12th
Gimly is excited to start the EOSIO identity working group WG (Twitter #eosio_id)! This open working group (WG) will create and foster identity solutions using EOSIO technology, by creating open W3C compliant self-sovereign identity standards, interoperability, and ecosystem development for eosio based identities.Covid-19 Credentials Initiative: Use Case Implementation • April 13
Digital Wellness Passes: The Missing Links Plug and Play Travel • April 14
This event will expand on the takeaways from our first digital wellness pass event “The Missing Links” including interoperability, standards, authentication, backend data exchange with vaccine certificates/testing results, and much more.Covid-19 Technology Innovations • April 14
“Explore the technology innovations being pioneered in response to the Covid-19 pandemic, and what potential for Scottish ventures this presents.” by Peter Ferry, Gary McKay and Julian Ranger (Siccar, APPII and digi.me)Privacy by Design • Apr 14
With Dr. Ann Cavoukian, Executive Director of the Global Privacy & Security by Design Centre.Series on self-sovereign identity (SSI) Conditis • April 14
This monthly webinar series is an opportunity to hear from UK experts in distributed identity and learn the mechanics of decentralized identity systems.Internet Identity Workshop XXXII (#32) • April 20-22 <—Register NOW. This is the main event for the whole community. The best place to dive in and get connected. 20% discount code: Identosphere_IIWXXXII_20
OpenID Foundation Virtual Workshop • April 29, 2021
PoCATHON by Affiniti • Mar 26 – May 9, 2021
We invite developers across the world to come and build applications that generate secure, portable and privacy-preserving credentials enabling trust across entities using Affinidi’s APIsIdentiverse 2021 • June 21-23 (Denver)
Covid 19
Everything You Need to Know About “Vaccine Passports” IdentityWoman \ Mother Jones
Andy Slavitt, a White House senior adviser for COVID response, specified at a March 29 briefing that “unlike other parts of the world, the government here is not viewing its role as the place to create a passport, nor a place to hold the data of citizens.”
WHO goes there? Vaccination Certificates Technology and Identity Stephen Wilson
the proper goal of a digital vaccination certificate should be confined to representing nothing more and nothing less than the fact that someone received their jab. Such a Verifiable Credential would include the place, date and time, the type of vaccine, and the medico who administered or witnessed the jab.
We don’t need immunity passports, we need verifiable credentials Cointelegraph
In theory, their idea is great. In practice, it’s terrible. Or, as the Daily Beast put it: “Vaccine Passports Are Big Tech’s Latest Dystopian Nightmare.”
Standards and Organizations
The 7 Laws of Identity Standards OpenID
A identity standard’s adoption is driven by its value of the reliability, repeatability and security of its implementations.
A standard’s value can be measured by the number of instances of certified technical conformance extant in the market.
Certified technical conformance is necessary but insufficient for global adoption.
Adoption at scale requires widespread awareness, ongoing technical improvement and a open and authoritative reference source.
When Libraries/Directories/ Registries act as authoritative sources they amplify awareness, extend adoption and promote certification.
Certified technical conformance importantly complements legal compliance and together optimize interoperability.
Interoperability enhances security, contains costs and drives profitability.
Verifier Universal Interface by Gataca España S.L.
This draft version can be found at https://gataca-io.github.io/verifier-apis/ and has been built using ReSpec.
This draft version for VUI includes today 6 APIs:
Presentation Exchange
Consent Management
Schema resolution
Issuer resolution
ID resolution
Credential status resolution
DIF Steering Committee election coming up
Among the conclusions of this analysis was that a larger steering committee would garner more trust and visibility into DIF's internal governance as an organization. An operating addendum was adopted last month which formalizes procedures for periodic elections and distribution requirements.
Testing self-sovereign identity with the Lissi demo
We are convinced this demonstrated user flow can help to better understand the interactions in a digital identity ecosystem such as IDunion. [...] The Lissi team is in discussion with trust service providers, authorities, municipalities, agencies, associations and other relevant stakeholders to meet all the necessary requirements and provide you with the best user experience.
Verifiable Credentials Use Cases - Affinidi
Starting with an intro to VCs in March, Affinidi has been rolling out a series on Verifiable Credentials use-cases!
Verifiable Credentials in Ben’s Serendipity
Think about it for a moment. No physical documents at all, but a simple and secure self-sovereign identity that Ben had complete control over. More importantly, look at the interoperability and flexibility as Ben could use them in different situations and across multiple platforms.
The EOSIO DID method specification
We have been working with the Decentralised Identity Foundation to shape this specification, and also want to thank the W3C Credentials Community Group for their support in the creation of the Verifiable Condition type, a necessary component to create the EOSIO DID document to represent EOSIO account permissions.
SSI In IoT, The SOFIE Project The Dingle Group
For the 22nd Vienna Digital Identity Meetup* we hosted three of the lead researchers from the EU H2020 funded The SOFIE Project. The SOFIE Project wrapped up at the end of last year a key part of this research focused on the the use of SSI concepts in three IoT sectors (energy, supply chain, and mixed reality gaming) targeting integrating SSI in without requiring changes to the existing IoT systems.
DID Comm has its own site
DIDComm lets people and software use DIDs to communicate securely and privately over many channels: the web, email, mobile push notifications, QR codes, Bluetooth, message queues, sneakernet, and more.
Company Updates
Elastos DID: What’s Ahead for 2021
Tuum Tech is working on an Elastos DID-based application called Profile, a rising competitor to LinkedIn – in large part by leveraging Elastos DIDs. Unlike in conventional applications where data and identities are managed and controlled by centralized systems, users will retain full ownership of their data when using Profile.
Spruce Developer Update #8
“We are currently working on a project that will enable creator authenticity for digital assets including NFTs.”
“focused on advancing did-tezos as the first formally verified DID Method.”
DIDKit Updates
Credible Updates
IDunion enters the second project phase initiated by the Federal Ministry of Economic Affairs and Energy of Germany
The goals of this new project phase includes the establishment of a European cooperative, the launch of a production network and the implementation of 40+ different pilot applications from several areas.
On Self-Sovereign Identity: What's the Business Value of SSI? Hackernoon
To businesses, immediate value comes from removal of the costly and challenging GDPR compliance. Forbes reports that in 2018 in the UK alone $1,1 billion was spent by companies on GDPR preparation, while US companies allocated over $7.8 billion on protecting customers’ personal information.
SAP Completes Pharmaceutical Industry Pilot to Improve Supply Chain Authenticity
today announced the completion of an industry-wide pilot utilizing self-sovereign identity (SSI) credentials to establish trust in the pharmaceutical supply chain for indirect trade relationships.
SAP Pharma Solution Supports Supply Chain Compliance
SAP has chosen an open, interoperable technology to validate all stakeholders in the pharma supply chain in order to provide customers with the best solution for compliance under the U.S. Drug Supply Chain Security Act (DSCSA) requirements. The DSCSA also limits stakeholders’ interactions to ATPs.
The benefits of Self-Sovereign Identity wallets: Collaborating on Self-Sovereign Identity wallets Rabobank (Part 2)
SSI and identity wallets will make it easier for citizens, organizations and governments to manage (digital) identities. It will make registrations and transactions across the internet private and secure. It will also make organizations more efficient and effective.
The Importance of Data Inputs and Semantics for SSI with Paul Knowles [Podcast]
The platform was an incredibly federated platform when I built it because I didn’t know that SSI existed. So as soon as I found that ecosystem, I tore up the rulebook and said, “This isn’t going to work; I have to rebuild it.”
Removing Anonymity Online Would Risk The Most Vulnerable Users Anonym
We all know online abuse can be incredibly damaging and Pew puts it like this: “In its milder forms, [online abuse] creates a layer of negativity that people must sift through as they navigate their daily routines online. At its most severe, it can compromise users’ privacy, force them to choose when and where to participate online, or even pose a threat to their physical safety.”
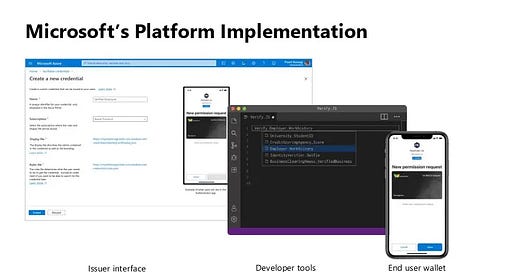
Azure AD Verifiable Credentials
Announcing Azure AD Verifiable Credentials MS ID Blog
We started on a journey with the open standards community to empower everyone to own and control their own identity. I’m thrilled to share that we’ve achieved a major milestone in making this vision real. Today we’re announcing that the public preview for Azure AD verifiable credentials is now available: organizations can empower users to control credentials that manage access to their information.
Azure AD Verifiable Credentials Entering Public Preview Kuppinger Cole
This solution enables organizations to design and issue verifiable credentials to their users, be it enterprises issuing employment credentials to their employees, universities enrolling students or issuing diplomas, governments issuing passports, ID cards, and countless other uses.
Azure Active Directory VCs - preview introduction Daniel Krzyczkowski
I have configured Verifiable Credentials accordingly to details in the documentation. I have an existing Azure AD B2C tenant so it was much easier because users have to sign in first before they can be issued a verifiable credential.
Blogs
On the Horizon: Tykn and Social Impact Through Digital Identity IdentityReview
The Turkish Government has recently announced that it will be using Ana to accelerate work permit distribution for its 3 million refugees. The Turkish Ministry of Foreign Affairs—alongside the United Nations Development Programme (UNDP), the INGEV Foundation, the World Food Programme (WFP), TÜBİTAK and the Istanbul Chamber of Commerce—developed this application with the intent of making refugees financially independent.
Self-Sovereign Identity and Government – Data Exchange Cybernetica
We then begin sharing portions of that data with third parties, leading to a situation where the data is now in three locations, the weakest of which is still most definitely the end-user’s method of storage, where all the data on them is accumulated.
Self Sovereign Identity Systems - The Passion Pad
We should have the right to manage our identity, free of any country or the place where we live. By giving this right to the government or any central authority, we give them much more power. Separating data rights from the actual data is important. User should have the right to decide who should have the access to his/her data.
Creating Verifiable credentials in ASP.NET Core for decentralized identities using Trinsic
This article shows how verifiable credentials can be created in ASP.NET Core for decentralized identities using the Trinsic platform which is a Self-sovereign identity implementation with APIs to integrate.
Videos
Digital Identity, use Verifiable Credentials with Blockchain Microsoft Mechanics
Joy Chik, Microsoft’s Identity CVP, joins Jeremy Chapman to show you how it works and gives you the key steps to get up and running.
Jolocom's lightning talk at DWeb meetup - Self-sovereign Identity In Germany
A brief video introduction to use cases, strategies and challenges of the four German SDI projects.
Papers
Blockchain, Self-Sovereign Identity and Digital Credentials: Promise Versus Praxis in Education
technology as a public good for the education sector. It levers on the lead author’s perspective as a mediator between the blockchain and education sectors in Europe on high-profile blockchain in education projects to provide a snapshot of the challenges and workable solutions in the blockchain-enabled, European digital credentials sector.
Not SSI but interesting
NFTs on Holochain? Easy as passing the ball Holochain
in Holochain, every element on every user’s chain is already guaranteed to be unique, and you don’t get scarcer than that. You just need to track the history of who the unique thing has been transferred to.
What is up with Yat? NFTs.WTF
What’s strange about the project is that the people behind it (Richard Spagni and Naveen Jain) are not novices, but world-leading privacy experts and seasoned founders and investors in crypto, leading many to give them the benefit of the doubt that they will deliver on the promises to users and that there must be some reason for them to not share more technical details. [Yikes! -nfo]
Exclusive: Trust in tech cratered all over the world last year Axios
Edelman said the main reason for the trust fall is the increasingly “complicated” relationship between the public and technology — including the spread of misinformation, rising privacy alarm and bias in artificial intelligence.
What Are the Six Key Areas of the FATF Consultation? Elliptic
On March 19th, Paris-based Financial Action Task Force (FATF), the global standard-setting body for anti-money laundering and counter-terrorism finance (AML/CFT), released its Draft Updated Guidance for a Risk-Based Approach to Virtual Assets and Virtual Asset Service Providers. Or, in compliance acronym speak the FATF's draft guidance for its RBA to VAs and VASPs.
Thanks for reading
Subscribe on newsletter.identosphere.net and support us at patreon.com/identosphere