Identosphere #43 • Azure AD VCs Preview • SSI in Web3
Towards a decentralized identity that puts people in control over their personal information.
Welcome and Thanks to our Patrons!
Support Identosphere via Patreon — Get Exclusive Content!!
Read previous issues and Subscribe : https://newsletter.identosphere.net
Contact \ Content Submissions: newsletter [at] identosphere [dot] net
Upcoming
1/2 Day IIW Virtual Event • The Business of SSI • 8/4
Introduction to Hyperledger Sovereign Identity Blockchain Solutions: Indy, Aries & Ursa • ♾️
IIW 33 • 10/12-14
Digital Trust World 2021 10/4-7 ‘the Conference for Authentication, Biometrics, Fraud & Security and Identity,’
Getting Started
Beginners Guide to SSI Domi
Sebastian Gebski's Reviews > Self-Sovereign Identity: Decentralized Digital Identity and Verifiable Credentials by Alex Preukschat, Drummond Reed
highly recommended. I strongly believe that the concept of SSI will be extremely important in the future - that's actually one of the few implementations on the blockchain that make a lot of sense.
Money
Build the dweb at HackFS (lots of links to guides)
Best use of Ceramic data streams or IDX for identity: $2,500
Best new tooling or patten for other developers to use IDX or Ceramic: $1,500
Best use of Ceramic alongside another sponsor: $1,000
Call for solutions : Trust My Data Until 9/13
Do you have experience in verifiable digital certificates and digital wallets?
Do you have ideas for digitising and securing the exchange of state-certified data, based on open standards and allowing for a secure and interoperable exchange of structured data with automatic authenticity verification?
Frameworks \ Standards
Ten Reasons to Use Picos for Your Next Decentralized Programming Project
Summary: Picos are a programming model for building decentralized applications that provide significant benefits in the form of abstractions that reduce programmer effort. Here are ten eleven reasons you should use picos for your next decentralized application. Temperature Sensor Network Built from Picos I didn't start out to write a programming language that naturally supports
Bootstrapping a VDR-based Fully Decentralized Object (FDO)/Credential Platform: VON Example
What are the common/known strategies for bootstrapping a VDR-based decentralized credential/object platform? …asked naively on purpose. Strategies for placing the first/initial DIDs in the VDR? …presumably purposed to be the initial Issuer(s) of verifiable
Panel: Start Simple to Scale Decentralized Identity HGF2021 • Indicio
Liquid Avatar Technologies and Indicio.tech will share how together they are transitioning the current KABN ID solution to verifiable credentials by building the Liquid Avatar Verifiable Credentials Ecosystem utilizing Hyperledger Aries, Ursa, and Indy.
GID EPISODE 10 — How to decentralize identity and empower individuals
If the internet decentralized information and crypto decentralized money and payments, then verifiable credentials will decentralize identity. In this episode, we chat with Dev Bharel, the software architect leading the charge around verifiable credentials at GlobaliD.
Verifiable credentials are key to the future of online privacy HelpNetSecurity
All the data is decentralized, meaning there’s no need for a database of student records that could be jeopardized. Alice’s data lives with her.
The employer doesn’t need to keep a copy of Alice’s transcript to verify her education.
The college doesn’t play intermediary and doesn’t have access to the list of organizations Alice shares her data with. Other parties have no way of correlating this data as each exchange is private and unique.
If desired, Alice could pick and choose what she wants to share. She could prove her degree without sharing her date of graduation or GPA, for example.
@Steve_Lockstep
The original #VerifiableCredentials were PKI-based SIM cards and EMV cards. […] https://constellationr.com/blog-news/not-too-much-identity-technology-and-not-too-little
Azure AD Verifiable Credentials architecture overview (preview)
This architectural overview introduces the capabilities and components of the Azure Active Directory Verifiable Credentials service.
What the Heck is a Data Mesh?!
I re-read Zhamak Dehghani ’s original and follow-on posts. Zhamak is the creator of the data mesh. In her second post she identifies four data mesh principles:
Domain-oriented decentralized data ownership and architecture
Data as a product
Self-serve data infrastructure as a platform
Federated computational governance
Company News
Gravity, Tykn advance interoperability of two decentralized ID solutions for the humanitarian sector
Gravity and Tykn are pleased to announce our continued collaboration to advance the interoperability of our two distinct decentralized identity solutions
Building an Identity Solution — Quantity Doesn’t Equal Quality Auth0
Why adding more developers to an identity project doesn’t always work out as intended
Selective Disclosure: Share What You Want Affinidi
Dock claim deduction demo
Andrew Dirksen, one of Dock’s core developers, walks you through a demo that shows how claim deduction, facial recognition, and verifiable credentials can be used together to cryptographically verify a person's age, eliminating the need for manual checks
European Digital Identity: Talao Announces Professional Credential Solution Talao
Talao’s team is excited to announce the development of the first Decentralized Self-Sovereign Identity (SSI) solution built on the Tezos blockchain for the Human Resources industry.
Use-Case
Confidential exchanges and the sharing of sensitive data: a major problem in business
if a crypto-account acquires an NFT UNIKNAME, the DID attached to it will totally control this NFT . The NFT UNIKNAME is a random-looking character string to which properties can be attached. The characters actually encode an obscured form of a human-memorable identifier.
Digital signatures, a fast track to digital transformation in the real estate sector
Find out how digital signatures are revolutionising the industry.
Web3
Web 2.0 vs Web 3.0 — A Bridge Between the Past and the Future
Web 2.0 vs Web 3.0 — A Bridge Between the Past and the Future Web 2.0 represents the Internet as we know it today and includes all the blogs, social media sites, shopping, news generation, and more! It is marked by user-generated content, interoperability across different services, usability, interactiveness, and high levels of participation.
Seamless Web3 Identity Verification Fractal
Built on Polkadot, Fractal Protocol is an open-source, zero-margin protocol that defines a basic standard to exchange user information in a fair and open way, ensuring a high-quality version of the free internet. In its first version, it is designed to replace the ad cookie and give users back control over their data.
Self-Sovereign Identity, smart contracts and Web 3.0 Hackernoon
Public blockchain and smart contracts are a convenient and viable cloud for security-critical information and allow to implement more complex schemes. For example, your service requires that the user's identity be confirmed by some external KYC provider, or there must be an always available master public key to distribute software updates in the network (relevant for IoT).
A Closed Metaverse = Dystopia. Introducing the Open MetaverseOS Boson Protocol
Literature
Sovrin: An Identity Metasystem for Self-Sovereign Identity Phillip J. Windley
We discuss the problems of online identity on the modern internet, discuss the nature of digital relationships, explore the architectures of identity systems, and detail the combination of these concepts into a comprehensive metasystem for solving the problems of online identity.
Public Sector
State Identity Solutions: Build? Buy? Or Both?
With a buyable solution like Auth0, state administrations are able to roll out digital services in days versus years for a custom-built in-house solution. The back-end of Auth0’s solutions are pre-built, allowing teams to customize quickly with low to no-code inputs from a development team to get a new release deployed faster.
Do we really need (or want) the State to provide us with digital identification? LIberatarianism.org
With identity being the missing link, the advent of self‐sovereign identity could finally bring ambitious projects like Bitnation to fruition. This virtual blockchain jurisdiction wants to establish a blockchain‐based self‐administration or, as the project itself advertises, “a toolbox for do‐it‐yourself governance.” With the concept of self‐sovereign identity being implemented properly, new digital nations such as Bitnation could compete against old territorial tax states.
Germany and Spain and join forces on the development of a cross-border, decentralised digital identity ecosystem
The cooperation agreement envisages the design and conceptualisation of a cross-border pilot to be implemented in the near future, with a view to contributing to the development of the European Union’s Digital Identity Framework, recently announced as part of the eIDAS Commission proposal.
New Digital Identity Advisory Council established
The NSW Government has established a Digital Identity Ministerial Advisory Council (DIMAC), that will advise on a strategic direction and roadmap for digital identity in the State.
Privacy
Links Between Privacy and Disinformation: Julia Angwin
Privacy, as we know, is a complex topic. When it converges with technology, it becomes more complicated. One aspect of this complexity is where privacy fits in with disinformation—false or misleading information spread intentionally to confuse or manipulate people.
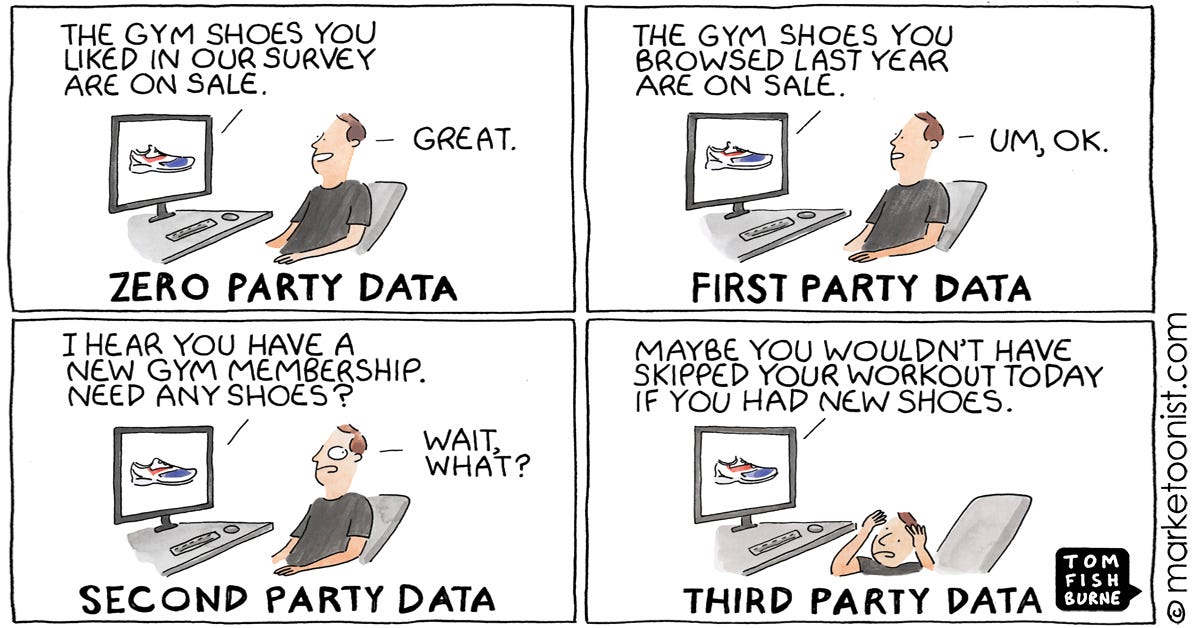
@tomfishburne
“The Personalization Privacy Paradox” - new cartoon and post on zero party data versus third party data https://marketoonist.com/2021/07/zeropartydata.html
Advances in health "must ensure self-sovereign identity" HealthCareGlobal.com
“I wholeheartedly agree that individuals should not be required to share their own personal health information with unknown third parties or with anyone in authority who demands it" Shaw adds. "But I strongly disagree with the suggestion that ‘events and businesses are either safe to open for everyone, or no one’. It creates a false dichotomy that either everyone is safe, or nobody is safe
Biometrics
China’s Supreme Court Bars Use of Facial Recognition Without Consent
China’s highest court has issued a ruling that could significantly limit the scope of facial recognition programs in the country.
iOS 15 Code Points to Biometric Onboarding for Apple’s Mobile ID
The iPhone’s incoming mobile ID feature will use selfie biometrics for identity verification, suggests code uncovered by 9to5Mac. The news indicates that Apple will be even more directly in competition […] The post iOS 15 Code Points to Biometric Onboarding for Apple’s Mobile ID appeared first on FindBiometrics.
Thanks for Reading!
Read more \ Subscribe https://newsletter.identosphere.net
Support this publication https://patreon.com/identosphere
Contact \ Submission: newsletter [at] identosphere [dot] net