Identosphere #44 • Are We the Problem? • CCG Highlights • Excelsior Pass+
You weekly guide to the latest news events and information surrounding work related to the development and implementation of decentralized identity and verifiable credentials
Welcome and Thanks to our Patrons!
Support Identosphere via Patreon — Get Exclusive Content!!
Read previous issues and Subscribe : newsletter.identosphere.net
Contact \ Content Submissions: newsletter [at] identosphere [dot] net
Upcoming
Self Sovereign Identity/Decentralised Identity and Financial Services • 9/2 in Amsterdam, Berlin, Rome, Stockholm, Vienna
EIC Speaker Spotlight: Vittorio Bertocci on Browser Changes Affecting Identity 9/14
IIW 34 • 10/12-14
Digital Trust World 2021 • 10/4-7 ‘the Conference for Authentication, Biometrics, Fraud & Security and Identity,’
Explainer
A Beginner’s Guide to Self-Sovereign Identity Domi
This article explores the current state of our online identities, wherein our personal identity is siloed and held by third parties on various servers - and is therefore more vulnerable to cyberattacks. Corporations such as Google offer the ability to use your account with them to access other sites, but this comes with problems of its own:
Verifiable credentials are key to the future of online privacy Helpnet
they offer a few advantages that we don’t get with paper records. Whereas a physical document (let’s say, a vaccine card) can be forged and passed off as authentic, the security mechanisms behind a verifiable credential means that it can never be tampered with and that anyone shown the credential will be able to immediately verify who issued it and to whom it was issued.
Selective Disclosure: Share Just What You Want Affinidi
In the context of SSI, selective disclosure is best implemented through verifiable credentials where the user has separate credentials for each piece of information such as his/her date of birth, full name, vaccination details, address, passport number, etc.
IDENTOS prepares customers for verifiable credentials Identos
Rather than trying to paste everything and everyone together, the path forward to help build trusted ecosystems relies on interoperability and leveraging existing assets while positioning the user in a disintermediated model of control and agency — possible with FPX and verifiable credentials.
Thought Leadership
#Identity. Are we (the industry) the problem? MyDigitalFootprint
It is evident that our ongoing discussions about identity, ethics, bias, privacy and consent revolve around a lot of noise (opinions) but little signal (alignment), but why? Recognising that in 30 years of digital identity, we still lack coherent and coordinated action to make it work for everyone is a reality.
Can Consent Ever Play a Valuable Role in Consumer Privacy? Anonyme
Can we rely on ‘informed consent’ if the informed part is largely missing?
Consent doesn’t scale well from the consumer’s perspective.
Identities Evolve: Why Federated Identity is Easier Said than Done SSRN
This paper shows that federated identity is really a radical and deeply problematic departure from the way we do routine business. Federation undoes and complicates long standing business arrangements, exposing customers and service providers alike to new risks that existing contracts are unable to deal with. Identity federations tend to overlook that identities are proxies for relationships we have in different contexts. Business relationships don’t easily “interoperate."
Use Cases
Groundwork laid for mass digital identity take up as use cases grow Biometric update
Identos is adding W3C (World Wide Web Consortium) verifiable credentials as a product feature for its digital ID solutions by the end of the year, announcing its position in the race to incorporate international standards for how digital credentials – from health records to degree certificates – are stored and verified.
Impact of Self-Sovereign Identity in Real Estate Affinidi
One sector where SSI is expected to have far-reaching implications is the real estate industry, as it has the potential to bring in a lot of transparency and trust among the stakeholders.
So, how does SSI fit into this traditional real-estate sector?
Opening the domestic card rails to innovation Meeco
Enabling Australian FinTechs a direct avenue to discuss how they partner and collaborate to access the eftpos payments network through the Committee resulted in recommendations that covered a number of central themes, including consultation and engagement, regulation, and technology and solutionsBen Tabell, eftpos Chief Information Officer and Committee Chair
Organization Work
2022 Pre-Budget Submission DIACC
That the government secure adoption of the Pan-Canadian Trust Framework by businesses and governments.
That the government act on the Finance Committee’s 2021 Pre-Budget Consultation Recommendations 128, Implement a digital identity system that empowers Canadians to control their data that is held by the federal government, and 129, Create a national data strategy.
That the government work with provincial and territorial partners and Immigration, Refugees and Citizenship Canada to ensure that all Canadians have access to an ISO-compliant government-issued digital ID credential with economy-wide utility by December 2022.
That the government make digital identity-enabled services available to all Canadians by December 2022.
That the government prioritizes funding and integration of digital ID as part of the Digital Technology Supercluster Initiative.
Blockchain
Why cheqd has joined the Cosmos
We know that many communities are desirably and rightly passionate about their adopted protocols. We are not taking shots at any of the ones discussed below, which we didn’t take forward; we only want to explain our thinking and why we see using Cosmos as a massive boon for us.
Public Sector
Governor Cuomo Announces Launch of Excelsior Pass Plus to Support the Safe, Secure Return of Tourism and Business Travel NYS Gov
Excelsior Pass Plus, a result of the strategic partnership between New York State and VCI, will provide New Yorkers safe access to retrieve a secure, digital copy of their COVID-19 vaccination record using the SMART Health Cards Framework - making their interstate and international travel and commerce experiences safer, contact-less, and more seamless.
When will we get our own digital identity? Self-Sovereign Identity is coming! Jan Scheele
From the moment the parents register a child with the Municipality, the official identity is recorded in the Personal Records Database and you will receive a Citizen Service Number. Will it soon be replaced by a digital identity, or a Self-Sovereign Identity? In this article I will tell you all the ins and outs about this new form of identity.
SELF-SOVEREIGN IDENTITY: LEGAL COMPLIANCE AND THE INVOLVEMENT OF GOVERNMENTS SSI AMBASSADOR
When it comes to identity management the involvement of the government can be a tricky topic. It needs to be involved to enable access to public services, adapt legislature and guarantee equal access for its citizens. However, it should not be able to control or monitor all aspects and activities of its citizens. Self-sovereign identity (SSI) might for some imply, that a citizen is suddenly able to issue his own ID-card, which isn’t the case. Governments are still the primary source of foundational identities."
Data Sovereignty and Trusted Online Identity IEEE Beyond Standards
IEEE SA co-organized a discussion panel at the Pan-European dialogue on Internet Governance (EuroDIG) conference, an event known for its frank and interactive discussions of public policy issues surrounding internet governance. Messages coming out of the discussions will be presented at the Internet Governance Forum (IGF) later this year.
IOT
Digital Twins and Self-Sovereign Identity: Build the next generation of Simulation with privacy preservation IOT Practicioner
Managing IoT devices and user identities as well as the relationships among various devices and their digital twins face significant challenges. First, a lack of Identity Credential and Access Management (ICAM) standards for IoT creates proprietary standards and a lack of interoperability. Second, the operational lifecycle of IoT devices complicates integration of traditional ICAM. Lastly, ICAM technology must adapt to the proliferation of connected devices. This evolution requires a digital trust framework and the decentralized architecture of Self-Sovereign Identity (SSI).
Smart Property Windley
Smart property is much more than the anemic connected things we have now. Smart property imagines a world where every thing participates in digital communities and ecosystems, working through programmable agents under the owners control.
APPLYING CONCEPTS FROM SELF SOVEREIGN IDENTITY TO IOT DEVICES IOT dot EU
Devices are equipped by the manufacturer with an identity stored in a trusted execution environment (TEE) and secured by a blockchain. This identity can be used to trace back the origin of the device. During the bootstrapping process on the customer side, the identity registration of the device is updated in the blockchain. This process is performed by a so-called registrar. Smart contracts prevent unsolicited transfer of ownership and track the history of the device. Besides proof of origin and device security our concept can be used for device inventory and firmware upgrade.
Hands On
Setting up Mediator Agent in Ubuntu — (.Net Core service in Linux Box) Rangesh
In a Self Sovereign Environment supported by Hyperledger Indy / Aries agent framework, Mediator Agent is one of the essential components that acts as postman service between Issuer /Verifier Aries Agent and Mobile Agent.
Spruce Developer Update #11
CCG Mailing List
Light week on the feeds, so we can get caught up on the CCG mailing list :D
ATTENTION CCG LIST LURKERS!1! Talk to us, was Re: CCG 101 questionnaire 6/8 Heather Vescent
Our community has 440 members, but only 12 of you have responded. *sad face*
This survey is fast and fun, and will help us improve the CCG experience for you - especially if you are a lurker and want to engage with this community/the tech being built here. You're already taking a break reading this email, so just click the link! It's only 2 minutes (or less) of your time.
https://docs.google.com/forms/d/1PPNyZHq1c9xm8n_hdky3u4w7Bxn9OQ6GkLZt0-qGU_M/edit
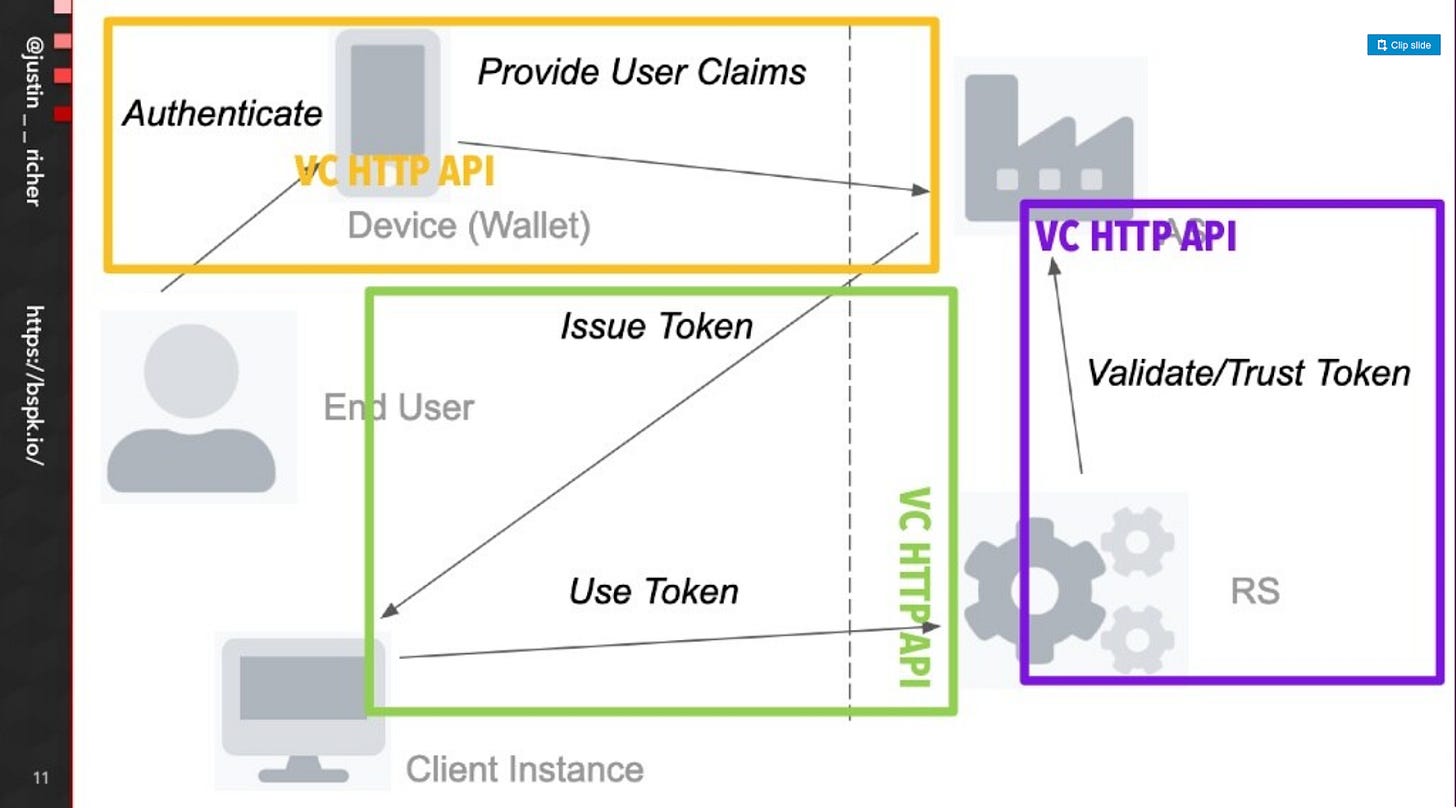
Re: VC-HTTP-API - A follow up on the RAR presentation Justin Richer 6/30
https://www.slideshare.net/zeronine1/rar-and-gnap-for-vc-http-api
As stated on the call, I did not write the deck as a leave-behind artifact, and so encourage people to instead watch the video of the presentation with vocal track instead.
RAR resources? Brain Richter 7/12
As I've been digging into RAR a little bit and trying to see how it might
fit within the VC-HTTP-API work I have found some great resources speaking
about what RAR, PAR and JAR are.
- https://medium.com/oauth-2/rich-oauth-2-0-authorization-requests-87870e263ecb
- https://pt.slideshare.net/TorstenLodderstedt/rich-authorization-requests
- https://datatracker.ietf.org/doc/html/draft-lodderstedt-oauth-rar
Justin Richer replies
RAR has been implemented and is available in Authlete (and supporting libraries):
https://www.authlete.com/developers/relnotes/2.2.8/
And in Connect2ID (and supporting libraries):
Brian Richter Replies
As soon as I clicked send I also found this PR into keycloak
Verifiable Credential Notarization Protocol (VCNP) Michael Herman 7/17
I’m calling these Notarized Credentials because I think they differ from VCs in a couple of ways:
1. Support for Notary-based self-issuance of verifiable credentials (aka Notarized Credentials)
2. Three levels of signatures in the Self-Issuer scenario:
* No signature (when the credential is first created by Alice in Alice’s Personal Wallet (or an app under Alice’s control).
* Single signature (Alice’s signature)
* Notary signature (as a witness to Alice’s signature)
3. (Almost free) and liberal use of the VDR and issuance of new DIDs whenever needed
4. ZKP verification of Notarized CredentialsHere’s a more detailed visualization of the Verifiable Credential Notarization Protocol (VCNP) workflow…
Bikeshed: Renaming the VC HTTP API Manu Sporny 7/17
My attempts below:
VCP - Verifiable Credential Protocols
"HTTP protocols for the management of VCs"
Use this to define the class of protocols?
VCIP - Verifiable Credential Issuance Protocol
"An HTTP protocol for VC issuance"
VCVP - Verifiable Credential Verification Protocol
"An HTTP protocol for VC verification"
VCPP - Verifiable Credential Presentation Protocol
"An HTTP protocol for VC presentation"
VCRP - Verifiable Credential Repository Protocol
"An HTTP protocol for VC repository management"
RAR Structures for VC HTTP API 7/21 Justin Richer
This is what OAuth 2 invented scopes for, instead of the OAuth 1 or HTTP Basic method of “you just get everything”. So, why not just use parameterized scopes? It seemed like a good idea when I first invented it a decade ago: https://blue-button.github.io/blue-button-plus-pull/#scopes or when it got pulled into other efforts like https://openid.net/specs/openid-heart-fhir-oauth2-1_0-2017-05-31.html … and Orie even suggested the following set of parameterized scopes for this API:
'create:credentials': Grants permission to create credentials
'derive:credentials': Grants permission to derive credentials
'create:presentations': Grants permission to create presentations
'verify:presentations': Grants permission to verify presentations
'exchange:presentations': Grants permission to exchange presentations
Supporting VC-JWT and BBS+ Presentation Exchange in the VC-HTTP-API 7/31 Orie Steel
Here's my weekend project:
https://github.com/OR13/GNARLY (while we wait for a better name...)This demo API and Spec has a number of improvements over the current
VC-HTTP-API, including tested support for VC-JWT, JsonWebSignature2020 and
BBS+ Selective Disclosure Presentation Exchange.I also added some details on "scopes" and references to how easy and well
supported they are by Swagger and Auth0.Remember that we resolved to follow https://restfulapi.net/ and
https://swagger.io/specification/ ... neither of which support GNAP or RAR
explicitly.
Thanks for Reading!
Read more & Subscribe newsletter.identosphere.net
Support this publication https://patreon.com/identosphere
Contact \ Submission: newsletter [at] identosphere [dot] net