Identosphere #45 • UK ID Framework • Good Healthpass Interop • Is Blockchain Needed or No?
The latest news and updates, with upcoming events, high level explainers, and use-cases from a variety of vantage points.
Welcome and Thanks to our Patrons!
Support Identosphere via Patreon — Get Exclusive Content!!
Read previous issues and Subscribe : newsletter.identosphere.net
Contact \ Content Submissions: newsletter [at] identosphere [dot] net
Upcoming
Self Sovereign Identity/Decentralised Identity and Financial Services • 9/2 in Amsterdam, Berlin, Rome, Stockholm, Vienna
EIC Speaker Spotlight: Vittorio Bertocci on Browser Changes Affecting Identity9/14
IIW 33 • 10/12-14
Digital Trust World 2021 • 10/4-7 ‘the Conference for Authentication, Biometrics, Fraud & Security and Identity,’
Hiring
Meeco is looking for a Technical Team Lead Meeco
for our Australian team, where you can contribute to the success of our product team developing our globally awarded personal data platform.
General Knowledge
Bright Story: Self Sovereign Identity: The good, the bad and the ugly Brightlands
This blog presents a plethora of benefits of SSI technology to citizens, consumers, business, organisations and government. It also sketches potential abuse of the technology. None of these benefits and threats have already emerged, as SSI technology, its associated business models and its governance frameworks are still developing.
Podcast: Kaliya Young, The Identity Woman: Part I I Identikit Sequent X
For the opening episode of ‘Identikit Sequent X’, Michelle Dennedy welcomes Kaliya Young, also known as The Identity Woman, to Smarter Markets for our latest series examining the evolution of digital identity, and how self-sovereign identity, specifically, can advance a consent-based economy.
Self-Sovereign Identity: What You Can/Can’t Do With SSI? Affinidi
it gives complete control and ownership of data to the individual entities as they can decide what data to share and with whom.
Beyond this encompassing vision, let’s drill down into the specifics to understand what you can and can’t do with SSI.
A Digital Identity Revolution Tracey Follows
In order to better understand the benefits and drawbacks of such a verification system, we have to look at the future and work backward to make the right decisions today.
Blockchain and SSI
Do You Need Blockchain for Enabling SSI? Affinidi
We hope this will get you thinking about enabling SSI using an option that best suits your application or business requirement.
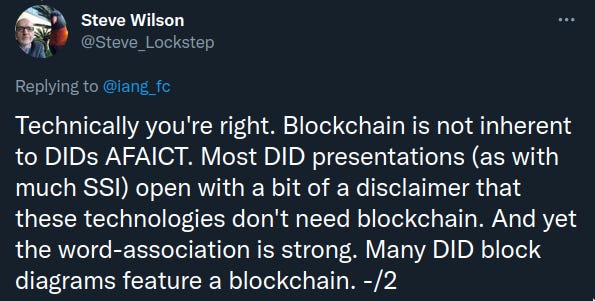
Twitter Thread of the Week Steve Wilson
Verifiable Credentials
The value of verifiable credentials in the evolving digital identity landscape Verified Me
In my recent podcast with Brad Carr of the Institute of International Finance, we discussed how digital identity and verified credentials can support a digital-first world, something that’s extremely relevant amid the current pandemic.
Better digital living with blockchain-backed verifiable credentials The Paypers
The NHS can now provide you with a digital verifiable credential to prove your vaccination status, securely stored in the NHS app and easily accessible, generating a QR code to prove to airlines and employers that you are fit to fly or work. But this is just the first step in the development of an enabling technology that can bring benefits to many areas of modern life.
On Climate Crisis and Self-Sovereign Verifiable Career Credentials Velocity Network
This rich verifiable self-sovereign career identity will be the ‘great transformer’ of the global labor market. It will change the way people navigate their careers and livelihoods, and how employers make talent decisions.
Transforming Scottish Education on the Blockchain DigitalScot
A pertinent example of how this can be applied in the corporate world is this example of the Scottish Social Services Council uses them to underpin workforce learning. The BCS describes this as the future of professional development, with many organizations like Siemens using them this way.
Bloom Attestation Service migrating to Verifiable Credentials Bloom
To transition fully to the W3C VC standard, Bloom decided to deprecate the proprietary attestation format and adopt the new open VC standard. The transition will fulfill the vision of giving Bloom users complete, secure control of their private data, while allowing interoperability with the rest of the VC ecosystem.
How Does a Verifier Know the Credential is Yours? Evernym
A link secret is a large random number, wrapped in a way that allows the holder to prove that they know the secret.
Issuing credentials directly to the MATTR mobile wallet Mattr
If you’re already using a secure mechanism to authenticate your users, then setting up OIDC capability isn’t necessary. As we’ve explored, sending credentials using secure DID messaging directly or via a QR code or deep-link is safe, convenient and allows users to obtain their credentials directly.
Interop
Setting Interoperability Targets Part 1 of 2 DIF
The Interoperability working group will be tracking them and providing guidance and documentation where possible. Importantly, though, there is a new DIF Working Group coming soon, the Wallet Security WG, which will dive deeper into these profiles and requirements, benefiting from a narrow scope and IPR protection, allowing them to speak more bluntly about the above-mentioned details.
Setting Interoperability Targets Part 2 of 2 DIF
Having shown in our last piece how interoperability “profiles” are designed, we now tackle some key technical problem areas ripe for this kind of profile-first interoperability work across stacks.
Release of the Good Health Pass (GHP) Interoperability Blueprint TrustoverIP
After a public review period during June with stakeholders in air travel, government, healthcare, hospitality, and other affected sectors, the Blueprint was finalized in mid-July for final approval and publication. “Publication of the V1.0.0 Blueprint is just the first step in seeing interoperable privacy preserving digital health passes adopted in order to support people being able to gather together again with lower personal and public health risk,” said Kaliya Young, chair of the Working Group and Ecosystems Director at CCI. “Our next task is collaborating with real world implementers to fill in any remaining gaps to get to an interoperable system and working with LFPH and other partners to deliver open source code that can be deployed.”
Public Sector
Can the Korean Mobile Driver’s License Unlock Blockchain’s Potential? Raon
The Ministry of Public Administration and Security (MOIS) is working on the implementation of a national mobile driver’s license in the form of a blockchain-based Decentralized Identifier-based (DID) System. LG CNS and RaonSecure are in charge of the project and are currently building it.
UK Draft Digital Identity Framework Published Research Live
Updates to the framework include new guidance on creating a consistent approach on user experience, rules on how to manage digital identity accounts, clearer definitions for the framework’s role and details on how organisations will be certified.
Thoughtful
What happens when is tension is too low to improve performance or conflict too much to bare? MyDigitalFootprint
Ephemeral Relationships Windley
Many of the relationships we have online don’t have to be long-lived. Ephemeral relationships, offering virtual anonymity, are technically possible without a loss of functionality or convenience. Why don’t they exist? Surveillance is profitable.
Data Mob Rule MoxyTongue
Individual Rights are hard to come by historically. Strong people make them possible. First requirement of their existence is thus, strong people.
Measuring the Ethical Behavior of Technology Me2bAlliance
This session will share the results and learnings of the creation and development of an ethical “yardstick” for respectful technology, including its application to websites and mobile apps. The speakers will also explore learnings from everyday people in the validation research around the certification mark as well as share recommendations for tech makers.
Social Agriculture — understanding Kenyan farmers’ use of social media platforms for agricultural practices Caribou Digital
Caribou Digital is excited to embark on a new research project to understand how Kenyan farmers use social media platforms as part of their agricultural practices.
Healthcare
Vaccine Credentials Focus Group - US Subgroup
This is the mailing list for the US subgroup of the Vaccine Credentials Focus Group. You can see the group charter here.
Participating and contributing in this group requires a CCI membership, open and free to all (organizations and individuals). If you are not a CCI member yet, please request a membership agreement at
https://www.covidcreds.org/#Join
.
Indicio and Liquid Avatar Technologies Launch Canada’s First Privacy-Preserving Decentralized Technology for Sharing Health Data Indicio
“Liquid Avatar Technologies shares Indicio’s vision—the world needs technology that works for people by delivering real privacy and security,” said Heather Dahl, CEO of Indicio. “When we launched the Indicio Network, we saw the need for a space for innovative companies to collaborate on changing how we manage identity, enable verification, and create trust. Our partnership with Liquid Avatar Technologies, one of many, shows what can happen when innovators solve pressing problems with ground-breaking technology.”
Governance
Self-sovereign identity: Legal compliance and the involvement of governments SSI Ambassador
When it comes to identity management the involvement of the government can be a tricky topic. It needs to be involved to enable access to public services, adapt legislature and guarantee equal access for its citizens. However, it should not be able to control or monitor all aspects and activities of its citizens.
Self-sovereign identity: the future of personal data ownership? WEForum
Self-sovereign identity is a promising technology to allow you to control your own data. However, to provide the true value of the technology, it is essential to establish governance framework for its operation.
Tech Stack
IOTA Identity: Beta Release
The first major feature we introduced with this beta release is the account, a higher-level API to use IOTA Identity. Similar to the recent Chrysalis update, IOTA Identity becomes a lot easier to use by utilizing the account. It is intended to provide a much more simplified interface that is perfect for 90%+ of the use cases. The other 10% are more complex use cases that may still want to utilize the lower-level APIs to have more control over the Identities. The account doesn’t just simplify the interactions with DID Documents, but also with the Tangle and Stronghold.
Magic: A Key-Based Authentication System For Self-Sovereign Identity
Since Magic’s authentication protocol is based on key pairs provided by decentralized blockchain networks, it is platform-independent and thus able to provide authentication service without having to rely on centralized identity providers.
Use-Cases
Digital Twins and Self-Sovereign Identity: Build the next generation of Simulation with privacy preservation IOT Practicioner
The rise in the use of advanced analytics, machine learning (ML) and Artificial Intelligence (AI) and the Internet of Things (IoT) today have driven the technology of simulation into the concept of the digital twin. Digital twins are generally defined as a virtual digital model of a physical system that is used to make better decisions about the real world physical system. Digital twins are usually intertwined with sensors and include a two-way interaction between the physical and digital twin.
Why Centralised Decentralised Finance (CeDeFi) and Self-sovereign Identity (SSI) Work Together Unizen
the combination of Centralised and Decentralised Finance — unites two ways of interacting with assets into one. Centralised Finance (CeFi) represents traditional entities (e.g. banks, brokers, funds), Decentralised Finance (DeFi) covers blockchain financial applications, cryptocurrencies, exchanges, decentralised payment services, etc. By merging the two, high transparency, impactful innovation, and wide adoption can be achieved.
How Credit Unions Use Verifiable Credentials with Members with John Ainsworth Northern Block
Learn how Bonifii is using Verifiable Credentials as a Digital Transformation mechanism for Credit Unions to Increase Engagement with their Members. John Ainsworth explains how they are revolutionizing how Credit Unions say “hello” to a member.
Thanks for Reading!
Read more & Subscribe newsletter.identosphere.net
Support this publication https://patreon.com/identosphere
Contact \ Submission: newsletter [at] identosphere [dot] net