Identosphere #58 • SSI ≠ Blockchain • FIDO Dev Challenge Winners • Concluding GLIEF's Financial Inclusion Series
Your weekly guide to the latest news and updates in self-sovereign identity. Upcoming events, use-cases, regulations, governance, and standards\development.
This weekly newsletter is possible thanks to readers like you!
Consider paying us a small amount each month via Patreon
Support our work on Patreon — Get Exclusive Content!!
Read previous issues and Subscribe : newsletter.identosphere.net
Contact \ Content Submissions: newsletter [at] identosphere [dot] net
Upcoming
Don’t miss our next speech at the ISSE Conference 2021 by EEMA • 11/16-18 Infocert
Unlocking Safe Travels Beyond COVID with Digital Credentials • 11/25 Affinidi
COVID Health Credentials for International Travel Summits (by LFPH and Affinidi) • 12/1-2 CCI Newsletter [APAC and EU friendly times]
Web3
Self-Sovereign Data (SoDa): The New Web3 Data Economy Craig Danton
In Stephenson’s “Snowcrash” Hiro Protagonist, the aptly named protagonist of the book, side hustles as a “Stringer for CIC”; essentially a gig economy worker collecting digital intelligence and posting it to a massive data marketplace. Users of the metaverse can then access this library to search for any information they want.
Unlocking Identity and Data Across the Web 3 Spruce ID
In recognition of our extensive experience with decentralized identity, Spruce was chosen in September to work with the Ethereum Foundation and ENS to develop Sign-In with Ethereum. This is meant to let users access online services by using their Ethereum accounts as an identifier, rather than an account owned by large corporations like Facebook or Google.
Explainer
Really Good: Self Sovereign Identity ≠ Blockchain Jolocom
Due to the ID-Wallet project in Germany, some articles and comments have equated Self Sovereign Identity (SSI) with blockchain technology in the last few weeks. The impression is given that SSI only works in conjunction with a blockchain. Spoiler, that’s not the case.
What Is Self-Sovereign Identity? Trinsic
Self-sovereign identity is the marriage of real identity with the digital world that will ultimately make people’s lives better.² It’s still in its infancy, and there is a long road ahead to truly make digital identity as legitimate and nuanced as a real-world identity.
Explaining SSI to C-suite executives, and anyone else for that matter – John Phillips SSIMeetup
Passwordless Authentication – Everything You Need to Know
When it comes to authentication, passwords were once the safest and most used methods of authentication
Public Sector
Catalonia launches a project for Self-Sovereign Identity to empower citizens in the digital world Politiques Digitales
The Government will only act as a validator, giving the tools and a secure legal framework, but it will not in any case have the custody of the data.
The Government of Catalonia has presented IdentiCAT, the new decentralized and self-sovereign digital identity model, which aims to become the first public digital identity at a European level and it will be self-managed by the citizen with the absolute legal guarantee and validity to operate with the public administration and the private sector.
Me2BA provides human-centered recommendations to the California Privacy Protection Agency
The California Privacy Rights Act of 2020 (“CPRA”) established the California Privacy Protection Agency (“CPPA”). The CPPA has full administrative power and authority to implement the CCPA and CPRA, which basically means that the CPPA will be in charge of updating regulations and adopting new regulations, while enforcement of these regulations will be done by both the CPPA and the Attorney General
Automating workplace vaccination verification — a path out of the pandemic IBM
The Department of Labor’s Occupational Safety and Health Administration (OSHA) recently released a rule on requiring all employers with 100 or more employees to ensure their workforce is fully vaccinated or require any workers who remain unvaccinated to produce a negative test result on at least a weekly basis before coming to work.
This rule impacts ~80 million workers — every company in the S&P 500
Company News
Hello World. It’s Walt.id
It is our goal to make SSI simple and accessible: to enable every developer and organisation to build identity and trust into the web and their applications. Ultimately, this will transform every digital interaction into an effortless and worry-free experience.
Bonfii announces partnership with Finclusive CU Ledger
FinClusive’s AML/KYC capabilities create verified identity credentials that will be incorporated into MemberPass – Bonifii’s digital identity solution for Credit Unions Through this partnership, U.S. Credit Union members can now establish and maintain verifiable digital identities that enable safe, secure, and touchless experiences for many credit union service
The Lissi Wallet now supports additional cards and convenience features
The Lissi Wallet now supports additional cards and convenience features. Import of additional cards The Lissi Wallet does supports verified credentials, custom cards and pk.pass files The Lissi Wallet now supports .pkpass files, as well as other custom cards, in addition to verifiable credentials (first screen). Any card in the wallet that has a bar code or QR code can now be easi
KYC-Chain Join Hands with enVoy
KYC-Chain will enter a partnership with enVoy. enVoy offers sustainable DeFi, tokenized letters of credit, realtime x border payments, and tokenized documentation for the supply chain removing risk and creating trust for third-party trade on an end to end ESG and sustainable supply chain journey.
Development
Issue Azure AD Verifiable Credentials from an application Microsoft
learn how to:
Set up Azure Blob Storage for storing your Azure AD Verifiable Credentials configuration files.
Create and upload your Verifiable Credentials configuration files.
Create the verified credential expert card in Azure.
Gather credentials and environment details to set up the sample application.
Download the sample application code to your local computer.
Update the sample application with your verified credential expert card and environment details.
Run the sample application and issue your first verified credential expert card.
Verify your verified credential expert card.
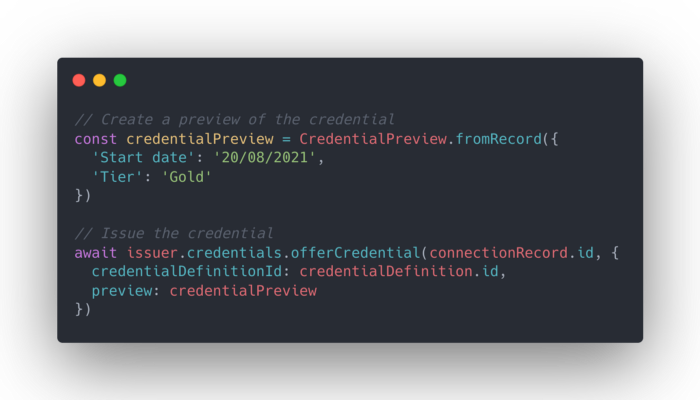
Issuing a verifiable credential in 7 easy steps Amino
First we’re going to create a holder Agent, this will be the Agent that receives the membership credential. During their life, the holder will collect many different verifiable credentials. Memberships, ID-cards, even purchasing records.
Welcome to Dock’s API - Testnet Sandbox
You can test our API in the sandbox testnet by simply switching the toggle to test mode. To get started; create a free account, log into your dashboard and acquire your API key.
Identity not SSI
2021 FIDO Developer Challenge: Outcomes and Winners
This year’s FIDO Developer Challenge reached a successful conclusion, with a ceremonial event during Authenticate 2021 in Seattle. The recorded video of the ceremony is available now, and we’re pleased to share more detailed stories of the three finalists as well as the rest of the teams that made it to the final stage.
Governance
ToIP Releases Additional Tools for Governance and Trust Assurance in Digital Trust Ecosystems
Following the September announcement of its first tools for managing risk in digital trust ecosystems, today the ToIP Foundation announced three more pairs of tools to assist in the task of generating digital governance and trust assurance schemes
Research
3 Stages of a Pan-African Identity Framework for Establishing Self-Sovereign Identity With Blockchain Solomon Darnell, Joseph Sevilla
Three stages have been identified as necessities to accomplish the development of this system before opening it further beyond the pan-African worldwide community. The three stages are defined by systems that allow for biometric/demographic registration (stage 1), interoperability and security hardening (stage 2), and biometric modality data analysis/organization/association (stage 3).
User Experience
Identity and Consistent User Experience Phil Windley
There's a saying in security: "Don't roll your own crypto." I think we need a corollary in identity: "Don't roll your own interface." But how do we do that? And what should the interface be? One answer is to adopt the user experience people already understand from the physical world: connections and credentials.
Use-cases
#5 in the Financial Inclusion Interview Series – Concluding Remarks from GLEIF CEO, Stephan Wolf
Throughout the financial inclusion interview series, we caught up with key partners to discuss the launch of GLEIF’s digital business identity initiative in Africa and how it is bringing about greater financial inclusion for African SMEs. Stephan Wolf, CEO of GLEIF, concludes the series by accentuating the immeasurable opportunities and transparency this initiative will bring to the global supply chain
How large is the market for Energy Web DIDs? EnergyWeb
At Energy Web, we understand that in order to have any meaningful adoption of enterprise applications using decentral technology, a DID-based tech stack has to be offered in a convenient and reliable way as well. This is why we’re developing the Decentralized Service Level Assurance (DLSA) solution.
Thanks for Reading!
Read more \ Subscribe: newsletter.identosphere.net
Support this publication: patreon.com/identosphere
Contact \ Submission: newsletter [at] identosphere [dot] net