Identosphere 65 • Building DID with MS • EU DGA meets TOIP (& MyData) • Devon Lofretto still not Moxy Marlinspike
Your weekly digest of the latest news, events, and development related to creating a system for ID online giving users ownership of their personal info, and eliminates the use of access control lists
Thanks to Patrons like you.
Consider supporting this publication with a monthly payment via Patreon ← click here
…or reach out to Kaliya, and she will invoice by your preferred means!
Read previous issues and Subscribe : newsletter.identosphere.net
Contact \ Content Submissions: newsletter [at] identosphere [dot] net
Correction: Moxy Tongue (Devon Lofretto, still not Marlinspike)
Last week we referenced Moxy Marlinspike’s first impressions of web3 (he really gets it!), recently posted on his blog, Moxy.
We also shared an image about Human Authority found on Devon Lofretto’s website Moxy Tongue, misattributed (again) to Moxy Marlinspike; a longstanding misattribution, only recently, “once and for all” publicly corrected.
TLDR; No Relation (but the, now famous, mis-attribution)
- Devon Lofretto came up with the original idea of Sovereign Source Authority, which became Self Sovereign Identity.
- Moxy Marlinspike, created Signal App. Nice privacy focused messaging app.
Upcoming
How To: Own Your Identity 1/25 UFOstart (IAMX)
Speaking: Markus Sabadello, Michael Shae, Tim Brückmann, Tim Heidfeld
Data Space Launchpad MyData • Until 2/22
Build using Decentralized Identities with Microsoft
Introduction to DID 01/13
Introduction to DID (continued) 01/20
High Level
#SSI101: An Introductory Course on Self-Sovereign Identity Spherity
Outside of a few philosophers, social scientists, and a tiny minority of specialized technologists, however, most people feel uncomfortable making any definitive or authoritative statements about identity.
Digital Identity Trends and Predictions for 2022 Signicat
What will be the buzzwords of 2022?
Identity wallet
Decentralized identity
Web 3.0
Passwordless
Kim Cameron
Remembering Kim Cameron Vittorio Bertocci
Kim might no longer update his blog, nudge identity products toward his vision or give inspiring, generous talks to audiences large and small, but his influence looms large in the identity industry – an industry Kim changed forever.
Memories of Kim Cameron Ian Glazer
Reification. I learned that word from Kim. In the immediate next breath he said from the stage that he was told not everyone knew what reify meant and that he would use a more approachable word: “thingify.” And therein I learned another lesson from Kim about how to present to an audience.
SSI Standards
Community Resources - DID Primer Credentials Community Group
decentralized public key infrastructure (DPKI) could have as much impact on global cybersecurity and cyberprivacy as the development of the SSL/TLS protocol for encrypted Web traffic (now the largest PKI in the world).
Why we need DIDComm IdentityWoman
This is the text of an email I got today from a company that I had a contract with last year [...] I was reminded quite strongly why we need DIDComm as a protocol to enable the secure transport of all sorts of things not just signed VCs but intermediate uses
NGI - ESSIF LAB reports
Adding SSI to internet communications using Sylk Suite by Bloqzone
The project SSIComms adds SSI to internet communications by adding SSI wallets to the renowned SYLK Suite, an award winning ensemble of communications solutions with the SIP protocol at its core.
SSI Mandate Service by Visma Connect
The SSI mandate service is a generic and holistic approach to provide and request mandates. Mandates are SSI credentials signed by the dependent that can be requested by either the dependent or authorized representative. These credentials can be used to prove to a verifier that the authorized representative is authorized to act for specific actions on behalf of the dependent.
OnboardSSI by Quadible
The concept of SSI was designed with the citizen and privacy in mind. However, existing implementations lack user-friendliness (e.g. showing hash codes to users), creating potential barriers in users’ adoption. OnboardSSI focuses on providing a secure and user-friendly wallet solution creating an easier way for citizens to manage their identity.
Data Privacy
Kids PRIVCY ACT Me2BA
Strengthen the legal protections afforded to children under COPPA, and extend COPPA protections to adolescents ages 13 to 17, who have long gone without privacy protections online, while creating new rights for families.
Prohibit surveillance advertising and other harmful uses of data on all digital services likely to be accessed by children, rather than limiting protection to ineffectual notice and consent on “child-directed sites.”
2022: LOOKING AT THE YEAR AHEAD MyData
As MyData Global saw in our reflection on 2021, the transformation towards a human-centric personal data economy is underway. This transformation is driven by two forces: first, the dominant unethical approaches to personal data are starting to show how unsustainable they really are.
EU DATA GOVERNANCE ACT MEETS TOIP FRAMEWORK
The DGA defines an “intermediary” that facilitates processing and sharing of data for individuals and organizations to “…increase trust in data intermediation services and foster data altruism across the EU”. In the MyData framework for user-controlled data sharing, intermediaries are called MyData Operators and there is a certification program in place.
Organizational Update
How LEI datasets can enhance global sustainability initiatives and climate-aligned finance GLEIF
During COP26, GLEIF announced a partnership with Amazon and OS-Climate to add LEI datasets to Amazon’s Sustainability Data Initiative [...] We have since caught up with Ana Pinheiro Privette, Global Lead for ASDI, to discuss how the partnership is working to improve global sustainability data modelling, mapping and calculations, and the expected impact on climate finance risk and opportunity evaluations.
Guidance on the Acceptable Use of Biometrics DIACC SIG
• Biometrics SHOULD only be used where its use is demonstrably necessary and […] is proportionate to basic human rights, privacy laws, and justifiable to the benefits gained.
• The biometric technology MUST require suitable accuracy, minimize data collection
• The evaluation of proportionaliry SHOULD include evaluating […] sensitivity, necessity, proportionality, effectiveness, and minimal intrusiveness.
Use Case
A MAJOR - AND OVERDUE - POWER SHIFT IS COMING TO TRAVEL Phocuswire
it will be a transformative change, shifting power from travel suppliers to travelers themselves and giving travelers more choice, better personalization, lower friction and more security.
Desire to store less digital identity data stokes travel’s SSI brushfire BiometricUpdate
The potential use cases for self-sovereign identity to transform the travel industry are almost limitless, particularly with the impending arrival of decentralized identifier communications, also known as DIDComm
Can Verifiable Credentials Make Life Better for Refugees? Affinidi
Let’s say Mr.X is forced out of his country due to war and he reaches the neighboring country but doesn’t have any physical document to prove his identity such as name, address, educational qualifications, work experience, etc.
Web3
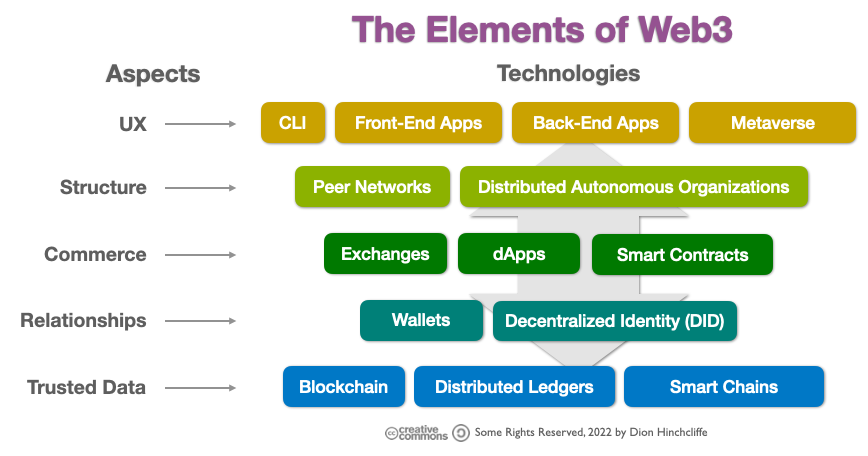
What is Web3 and Why It Matters Dion Hinchcliffe
OpenSea, Web3, and Aggregation Theory Stratechery
what gives Aggregators their power is not their control of supply: they are not the only way to find websites, or to post your opinions online; rather, it is their control of demand. People are used to Google, or it is the default, so sites and advertisers don’t want to spend their time and money on alternatives; people want other people to see what they have to say
Web3 and Digital Embodiment Phil Windley
Web3 will make a difference for all of us if it enables people to become digitally embodied, able to recognize, remember, and react to other people and organizations online—without the need to be in someone else's database.
Web 3.0 - How to get started! Tech3.0
I will go through how to create your own DID (ID on the blockchain), and how you can use it today with Profile. @tryProfile @ElastosInfo
What is Web3Auth???
Web3Auth partners with Polygon Studios to bring seamless logins to the Polygon ecosystem
Web3Auth aggregates OAuth (Google, Twitter, Discord) logins, different wallets, and existing key management solutions, and provides dApps/wallets a familiar experience that fits every user. Mobile, web, and blockchain agnostic
Metaverse
A Digital Identity Fit For The Metaverse Forbes
The SSI model has an individual’s value — be it crypto, in-game items, or other NFTs — directly tied to their identity. It will be accessible with a simple click for physical services, like an Uber, as well as digital ones
Avatars May Use SSI In Metaverse To Prove Identity Hypersign ID
The tech got a surge especially after Facebook decided to change its name to Meta. In this blog […] focus will be on explaining why decentralized digital identities are an important tool for Metaverse to replicate the real world.
Self Sovereign Identity and Web3: From the metaverse to real life Talao
SSI makes it easier to rely on traditional economic actuators (Brands) online and off-line to develop traffic and business on decentralized platforms and the Metaverse
Public Sector
MetaMUI and Sovereign Yidindji Government launched 1st self-sovereign identity-based National ID system Cointelegraph
We are delighted to announce that our first E-Government pilot program with the Sovereign Yidindji Government has been successfully completed on Jan 7, 2022.
Decentralized Identity & Government Evernym
a few notable government-led projects, such as Aadhaar (India), Verify (UK), eIDAS (EU), and the Ontario Digital Identity Program (Canada) - What decentralization means for portability, scalability, flexibility, and privacy - How governments and commercial organizations can enhance existing federated identity systems with verifiable credentials
the potential of Self-Sovereign Identity with representative use cases
Our Self-Sovereign Identity initiative with SwissSign, the canton of Aargau and cardossier clearly shows: Even if there are still uncertainties regarding technical maturity and governance – SSI is happening and brings major advantages in data protection and cross-organizational digitization.
Companies
SURF: Technical exploration Ledger-based Self Sovereign Identity Identity Economy DE
the privacy-friendly nature of SSI, end-user control over disclosure of personal information, and the SSI trust model aligned well with the public values typically found in R&D. The platform we used (based Hyperledger Indy) allowed us to successfully run all use cases.
SSI initiative open to new players adnovum
Procivis launches SSI+
Composed of the desk, wallet and gateway, SSI+ offers a complete solution for issuers, holders and verifiers of verifiable credentials (VCs) to get started with self-sovereign identity projects today.
Hello, User: Episode 13 with Katryna Dow
Katryna discusses Meeco’s mission to enable everyone on the planet access to equity and value in exchange for the data and information they share.
International Thank You Day Jolocom
We at Jolocom reflect on amazing projects that became possible by joining forces with partners such as T-Labs, Bundesdruckerei, Stacks, and TIB – the Technical Information Library Hanover.
Research
Non-human Personas: Including Nature in the Participatory Design of Smart Cities Martin Tomitsch, Joel Fredericks, Dan Vo, Jessica Frawley, Marcus Foth
we introduce a framework for developing and employing non-human personas. As a key element of the framework, we describe a middle-out approach for forming a coalition that can speak on behalf of the non-human species that are impacted by design decisions.
Identity not SSI
Nat Sakimura delves into Financial-Grade API ubisecure
“The data economy needs a secure and interoperable data network. And we are finally getting there with FAPI and eKYC standards. So, you guys need to get ready for the ride. It’s the time. You need to start acting, start preparing for that.”
The Rise of the Identity Data Fabric Radiant Logic
Every new identity project takes much longer than anticipated, demands huge costs in customization, presents a huge burden on staff across the enterprise, and reveals security gaps due to the complexity and inflexibility of the legacy infrastructure.
Thanks for Reading!
Read more \ Subscribe: newsletter.identosphere.net
Support this publication: patreon.com/identosphere
Contact \ Submission: newsletter [at] identosphere [dot] net