Identosphere 76: Avast Acquires SecureKey • EU Digital Wallet Consortium • Path to Mainstream Adoption
A weekly digest company news, policy updates, upcoming events, job opportunities, and developments in the standardization and adoption of sovereign identity protocols
Welcome to Identosphere’s Weekly Digest!
💖Thanks to our newest patrons & supporters💖
Support Identosphere on Patreon ← click here
…or reach out to Kaliya directly.
Read previous issues and Subscribe : newsletter.identosphere.net
Content Submissions: newsletter [at] identosphere [dot] net
Hiring
Executive Director ID2020
Coming up
Global Internet Governance and International Human Rights - Whose Rights, Whose Interpretations? 4/13-14, Nicosia (Program)
Techno-legal Challenges in Digital Identity Infrastructures: the Example of Self Sovereign Identities Alexandra Giannopoulou, University of Amsterdam, Netherlands and Ioannis Krontiris, Homo Digitalis, Greece
The question this article will try to answer is: are self sovereign digital identity solutions suitable for ensuring data sovereignty and individual empowerment? To answer this question, we will address challenges emerging from both the technological architectures and the applicable institutional and normative frameworks
Registration Open for OpenID Foundation Workshop at Google April 25 (Registration)
This OpenID Foundation Workshop includes a number of presentations focused on 2022 key initiatives for the Foundation as well as updates on active working groups.
Internet Identity Workshop #24 4/26-28, Mountain View, California
This is a really big deal that after switching to online for 2 years. It will be really good to be back together. Kaliya is the co-host along with Phil Windley and Doc Searls. Seriously just buy a plane ticket and come.Where IAM trends are set: EIC 2022 5/10-13 Berlin & Online
May 12th is decentralized identity day at the event (Kaliya may be attending)
Company News
ID.me and the future of biometric zero trust architecture Mike Vesey of IDRamp
The sunk cost of centralized databases is not an obstacle to decentralization. Verifiable credentials can be easily layered onto existing systems for better security. They can be used as a tool for orchestrating complexities across multiple identity management systems and databases so that they become privacy preserving and fraud resistant.
Acquisition of the Week
SecureKey looks to the future by joining Avast
Avast, a global leader in digital security and privacy, announced the acquisition of SecureKey. Our expertise combined with the maturity and scalability of our services will allow our Canadian success story to expand globally and provide people around the world with safe and accessible means of authenticating their identities online while cementing SecureKey as a key provider of digital identity solutions.
Public Sector
Ontarians are getting digital ID this fall: All you need to know itWorldCanada
tech standards that the provincial government says it is currently considering include the Verifiable Credentials Data Model 1.0 for data modeling, Decentralized Identifiers (DIDs) v1.0 for key management, JSON-LD 1.1 for data formatting, OpenID Connect as identity standard, BBS+ Signatures 2020 and Ed25519 Signature 2020 for signature format, Self-Issued OpenID Provider v2 and more for interoperability.
Organizations
European Union Digital Identity Wallet Consortium EUDI
The funding call is within the Digital Europe Programme (DIGITAL) topic 5.3.1.2 which requests support to implement the European Digital Identity Framework and the implementation of the Once Only System under the Single Digital Gateway Regulation. Up to €37m funding is available.
Schellman Joins Trust Over IP Foundation as Steering Committee Member
Tampa-based Schellman, a leading provider of attestation and compliance services, announced today that it is joining the Trust over IP Foundation (ToIP) as a Steering Committee member. As the first IT audit firm to join the leadership of ToIP, this move represents Schellman’s belief in the growing suite of digital governance specifications and tools being developed by ToIP Working Groups.
Sovereign Identity Use Cases
ID Verification Threats On the Horizon Liminal Podcasts
Cognito's CEO Alain Meier joins the State of Identity host Cameron D’Ambrosi to dive into why industries beyond financial services are now in the market for identity verification. They also unpack the impact of synthetic identity fraud across verticals, and how platforms find the balance when building their onboarding processes.
Fixing Aid | Can blockchain help fix the I.D. problem for a billion people? The New Humanitarian
Ismail looks at the concept of self-sovereign identity, which asserts that individuals must have ownership over their personal digital data and identification, and how that idea influences efforts to create efficient, secure digital identities for people in the midst of humanitarian crises.
SSI Fixes this?
I have been prompted several times this week by this article Hackers Gaining Power of Subpoena Via Fake “Emergency Data Requests” and people asking questions about whether SSI could solve this use case - Yes.
If there was a trust framework for police departments and a DID registry for them - the police departments could issue VCs to their officers.
If you want to se how hard this was/would have been to achieve in earlier technology stacks take a look at conceptual outlines from this NSTIC (National Strategies for Trusted Identities in Cyberspace) developing a trust framework for law enforcement federations done by the Georgia Technology Research Institute and the results/learnings.
Path to SSI\DID Adoption
Trust, Verifiable Credentials, and Interoperability Helen Garneau, Indicio
Accurate labeling, interoperability profiles, and testing are urgently needed to drive interoperability and scale decentralized identity, says a new white paper from Indicio
[…]
Seven aspects of interoperability
1. DID methods
2. Content encryption key types
3. Communication protocols
4. Credential format and signature types
5. Credential access / storage (wallet)
6. Credential protocols and coordination formats
7. Compatible governance / trust
4 Keys to Self-sovereign Identity Adoption Trinsic
Many implementers won’t realize the potential of SSI until it’s deployed at scale, but in order to get to scale, we need implementers to realize value. It’s the classic chicken & egg problem.
DID Conference Korea 2022 Recap – Identity Proofing, Passwordless Sign-in and User-friendly Digital Identity idRamp
The presentation focused on the keys to mainstream DID adoption:
Focus on practical business value
Better data protection vs debates on the value of decentralized/centralized systems
Stronger Zero Trust security vs details on blockchain, DIDs, and, ZKPs and ledgers
Easy password elimination and superior privacy vs sociological discussion on SSI and data economy
Trust as strategic brand advantage vs a long walk into new governance operation
Verifiable Credentials to accelerate service delivery and reduce cost of IAM
Optimize existing systems incrementally vs replacing them
Governance
The Age of Optionality—and its costs Doc Searls
We plan to relieve some of that oblivity by having Shoshana lead the final salon in our Beyond the Web series at Indiana University’s Ostrom Workshop. To prepare for that, Joyce and I spoke with Shoshana for more than an hour and a half last night, and are excited about her optimism toward restoring the public commons and invigorating democracy in our still-new digital age.
What can we do with a DAO that cannot be done with other organizational forms? Reb00ted
I conclude: there is no consensus whatsoever :-) That may be because there such a large range of setups under that term today.
Thoughtful
The Ukrainian War, PKI, and Censorship Phil Windley
PKI has created a global trust framework for the web. But the war in Ukraine has shone a light on its weaknesses. Hierarchies are not good architectures for building robust, trustworthy, and stable digital systems.
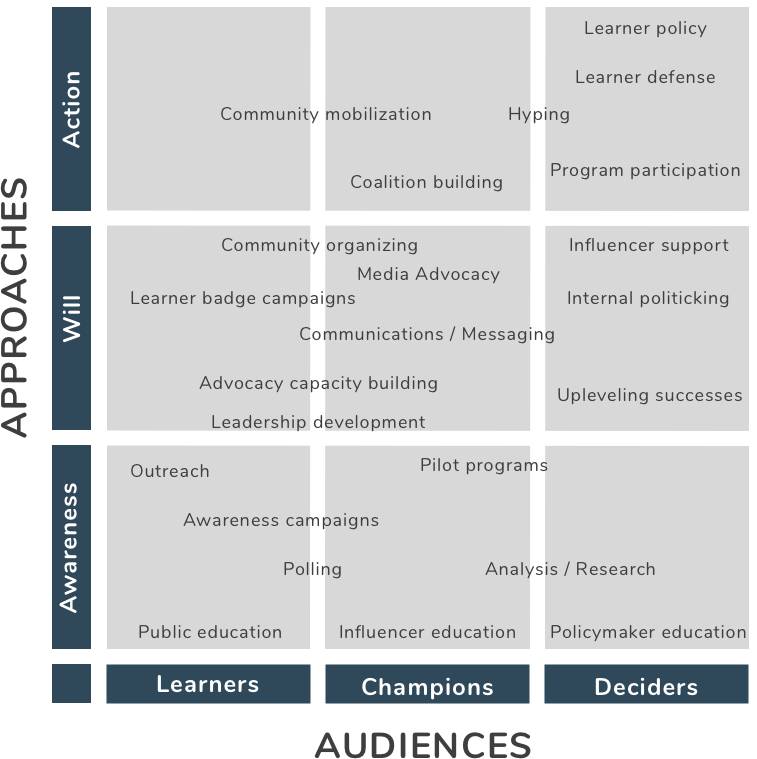
Advocating for learner-centric badge systems We Are Open Coop
how do we advocate for learner-centric badge systems? This is the piece that we’ve been thinking about the past couple of weeks.
Identity Not SSI
Biometrics…by CLEAR - trying to be the logIn with Google/Facebook for Real Life
New York Mets Offer Face-based Entry at Citi Field findbiometrics
Wicket’s tech will eliminate the need for manual scans, so fans who opt in will no longer need to stop and take out their phones to present a digital ticket.
The need for new Data Institutions Alan Mitchell
we were presenting at the Open Data Institute’s event on Data Sharing and the Rise of Data Institutions — a crucially important subject for the years ahead. (You can see the slides of our presentation here.)
Trusted Timestamping Part 1: Scenarios Nunnaphat Songmanee, Finema
Evidentiary value is an essential component of important transactions. When a transaction is recorded in a printed document, one way to impart evidentiary value is by including date and time
Worried About Digital Identity? The Security of Our Identities
We need to take back accountability for our data. It’s not up to Facebook or Google; they’re not security companies. These organizations do us a favour by offering backup and recovery options, but we pay the price. Furthermore, they are claiming your data as their asset and making money.
Decentralization is the Future of Digitization Jolocom
In Germany, for example, the federal government initially decided to store data from the nation’s Corona-Warn app on centralized servers, as reported by Reuters in April 2020. In response, multiple stakeholders like the Chaos Computer Club (CCC) loudly criticized the plans and the resulting public outcry forced the government to reconsider. The fact that the government heard the criticisms, re-evaluated its proposals and opted for a decentralized version of its Corona app instead – one where data will only be stored on users’ phones instead of centralized government servers – was news well received by large parts of society.
Thanks for Reading!
Read more \ Subscribe: newsletter.identosphere.net
Support this publication: patreon.com/identosphere
Contact \ Submission: newsletter [at] identosphere [dot] net