Identosphere Weekly #12 • Learn Concepts with MATTR • BCDevEx Opportunity
Identosphere wishes you a Happy New Year – full of verifiable credentials and key event logs. (December 19-27)
Being the holidays, and nearing the end of the year, this wasn’t the busiest week in SSI News, but we still found some gems. It feels good to browse the feeds and keep on the pulse.
Thanks, to our patrons, for supporting this publication!
If you haven’t already, you can contribute via patreon.com/identosphere.
Reads from this week
Is your company in the W3C?
If the answer is yes - there is an election going on right now for the Techincal Architecture Group ending Tuesday Jan 5th. Please check with your rep and ask them to vote for Amy Guy (Christopher Lemmer Webber recommends) and for Wayne Chang of Spruce Systems (Kaliya recommends)
Thoughtful Biometrics Workshop
The Thoughtful Biometrics Workshop is creating a space to dialogue about critical emerging issues surrounding biometric and digital identity technologies. It’s happening the 1st week of February: Monday, Wednesday, and Friday, 9am PST to 1pm PST / Noon EST to 5 EST.
Money for Developers!!! @bcdevexbot shares
This opportunity is for developers familiar with Hyperledger Aries, Aries Protocols, Python and JSON-LD processing to add support in ACA-Py for several important VC formats used by a number of other organizations in the VC community.
Value $60,000
Proposal Deadline: Jan 8, 2021
Adrian Doerk - SSI Ambassador shares:
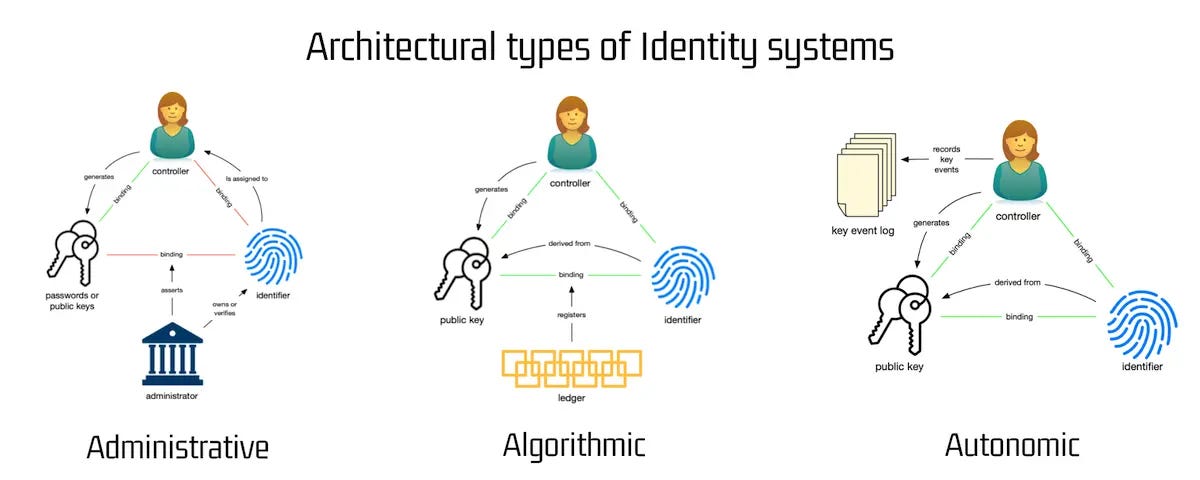
The trust infrastructure of self-sovereign identity ecosystems
The trust infrastructure is concerned with the question of how and why the presented information can be trusted. It defines the rules for all stakeholders and enables legally binding relationships with the combination of governance frameworks, which are built on top of trust frameworks.
The post includes a section on the core components of identity architecture that includes a graphic based on a post by Phil Windley that infominer appreciated.
SSI in Education
WellThatsInteresting.tech has a great post about SSI and Education. It highlights the recent announcement from Digitary about having issued over four million digitally verified documents from 100+ institutions for millions of learners in 135 countries.
Evernym’s December Roundup
Here are a few from Evernym’s picks:
Different approaches to Interoperability by Daniel Hardman of Evernym
Several VC ecosystems have grown up around the VC spec. Each touts standards compliance and interoperability, yet they do not currently interoperate with one another. Let’s have a look at their differences and commonalities, and then explore a simple proposal that might make which language your VCs “speak” as transparent as which language you choose when you watch a movie.
Sovrin’s 12 Principles of Self-Sovereign Identity
Representation • Interoperability • Decentralization • Control & Agency • Participation • Equity and Inclusion • Usability, Accessibility, and Consistency • Portability • Security • Verifiability and Authenticity • Privacy and Minimal Disclosure • Transparency
What Does Trust Over IP Mean for Governments and Their Citizens?
credentials can help reopen travel, reduce the costs and improve access to healthcare, streamline KYC and financial transactions, and help connect students with employers needing their skills—all while saving governments billions in the costs of connecting and protecting their digital infrastructure.
[...]
featured speakers from Evernym, Mastercard, LG CNS, Accenture, GLEIF, and other[s]
CCG Mailing List
Manifesto: Rules for standards-makers
I've used all kinds of formats and protocols in a long career as a software developer, even created a few. My new manifesto summarizes what I've learned about what works and what doesn't.
Heather Vescent shared this post by Dave Winer about lessons learned over his years in software development, discussion followed.
Video
Building interoperable self-sovereign identity for Europe
Oskar van Deventer, a rockstar from TNO, presents:
ways to build an SSI ecosystem and architecture together that is interoperable and technologically mature fit for society and funding opportunities for SSI projects through grants.
Podcasts
Using Self-Sovereign Identity as the Foundation for Secure, Trusted Digital Relationships with Kaliya Young
Kaliya was on the Human-Centered Security Podcast. You can find it on the Web, Spotifiy, or Apple Podcast.
SSI Fundamentals
Mattr Learn Concepts
MATTR rocked out some AMAZING posts on fundamental concepts surrounding SSI.
We highly recommend them!!
Web of Trust 101
The emerging “Web of Trust” is an idea that has been around since the dawn of the internet. To explain what motivated its creation, let’s take a look at how trust on the internet functions today.
Digital Wallets
The reframing of the user as a first-class citizen and their empowerment as ‘holder’ represents a shift towards a new paradigm. Such a paradigm offers users greater sovereignty of their own information and empowerment to manage their digital identity. Users are able to exercise their new role in this ecosystem by utilizing a new class of software known as digital wallets.
Verifiable Data
refers to the authenticity and integrity of the actual data elements being shared.
Also covers Verifiable Relationships, Verifiable Processes, Verifiable Credentials, along with Semantics and Schemas.
Semantic Web
The semantic web is a set of technologies whose goal is to make all data on the web machine-readable. Its usage allows for a shared understanding around data that enables a variety of real-world applications and use cases.
Selective Disclosure
An important principle that we want to achieve when designing any system that involves handling Personally Identifiable Information (PII) is to minimize the data disclosed in a given interaction. When users share information, they should be able to choose what and how much they share on a case-by-case basis, while the relying parties receiving the information must be able to maintain assurances about the presented information’s origin and integrity.
Trust Frameworks
Trust frameworks are a foundational component of the web of trust. A trust framework is a common set of best practice standards-based rules that ensure minimum requirements are met for security, privacy, identification management and interoperability through accreditation and governance. These operating rules provide a common framework for ecosystem participants, increasing trust between them.
VC Model from Trinsic
The Verifiable Credential’s Model
At the core of every self-sovereign identity (SSI) use case is what we call the verifiable credentials model. This simple yet effective model helps conceptualize how verifiable credentials are exchanged between people and organizations.
Non-identity news…
Financial struggles in the US
The latest data from the Census Bureau’s Household Pulse Survey, taken between November 25 and December 7, found that 35.3 percent of U.S. adults are “living in households not current on rent or mortgage where eviction or foreclosure in the next two months is either very likely or somewhat likely.”
Identity but Not SSI
The Nuts and Bolts of OAuth 2.0
Aaron Parecki - Mr. OAuth has a new course out on Udemy
3.5 hours of video content, quizzes, as well as interactive exercises with a guided learning tool to get you quickly up to speed on OAuth, OpenID Connect, PKCE, best practices, and tips for protecting APIs with OAuth.
Beginners Guide to JWTs
A JWT is a structured security token format used to encode JSON data. The main reason to use JWT is to exchange JSON data in a way that can be cryptographically verified. There are two types of JWTs:
JSON Web Signature (JWS)
JSON Web Encryption (JWE)
The data in a JWS is public—meaning anyone with the token can read the data—whereas a JWE is encrypted and private. To read data contained within a JWE, you need both the token and a secret key.
Thanks for Reading
This newsletter is 100% reader-supported.
All contributions are greatly appreciated.