Identosphere Weekly #15 • Establishing SSI • TBL Solid-Inrupt • Zero Trust Architecture
Week 2 January • Blogs • News • Frontiers Research • Mailing list discussions • Upcoming Events
Thanks for reading another edition of the Identosphere Weekly. Share, Subscribe, and read previous editions at newsletter.identosphere.net
It’s week 15 and we have 15 patrons! Thanks so much to our contributors! We’d love to keep that trend going. Consider becoming a patron and supporting the continued creation of this weekly identity update.
https://patreon.com/identosphere/
Upcoming Events
DIF - F2F Virtual Community Meeting
DIF ( Decentralized Identity Foundation) is inviting the entire decentralized identity community to join our Second open online virtual meeting. We will discuss the current state of the decentralized identity space, individual elements' status, and how the path towards interoperability should look.
While many of the discussions will center around work items developed within DIF, we recognize the importance of cross-community collaboration. We will make sure that most key technologies will be presented at the meeting.
January 19th in the every fun “Gather Town” (so it is a relief from zoom and the avatars are so cute). Preliminary agenda
Decentralised Identity: What’s at Stake? Roundtable Discussion
The debate discussion will focus on the INATBA Position Paper on Decentralised Identity published on Nov 26th 2020.
This is going to be good :)
Speakers
Anil John Technical Director of the Department of Homeland Security Science & Technology Silicon Valley Innovation Program (SVIP)
Daniël Du Seuil Convener of the European Self Sovereign Identity Framework within the European Blockchain Partnership, National Belgian SSI Project Leader
Dr. Loretta Anania Scientific Officer at European Commission’s DG Connect
Kai Wagner INATBA Identity Working Group Co-Chair, INATBA Board of Directors Member, Partnership Development & Regulatory Affairs at Jolocom
Karyl Fowler CEO and Co-Founder of Transmute, Member of the Decentralized Identity Foundation Steering Committee
Indicio.Tech Meetup
Introduction to the newly open-sourced Mediator Agent
Please join us as we discuss the newly announced #opensource Mediator Agent for the #Aries toolbox
Wed, Jan 20, 12pm EST - Indicio.Tech
DHS S&T Insights Outreach Webinar Series
Do you have a cutting-edge technology or a new idea we need to know about?
We are launching the new Insights Outreach webinar series that will happen the first Tuesday of each month starting February 2021.
Join us on February 2, 2021, at 2:00 PM ET for the series launch. Office of Industry Partnerships Director Megan Mahle and S&T Industry Liaison Dee Parker will highlight S&T's unique innovation funding programs and current opportunities to adapt, develop, or commercialize your technologies in support of the DHS mission.
Thoughtful Biometrics Workshop
Update! This event has been postponed to March 8/10/12
9am-1pm PST Noon-5 EST.
creating a space to dialogue about critical emerging issues surrounding biometric and digital identity technologies.
Establishing Self Sovereign Identity
• How will society transition from today’s vast, vulnerable identity data silos to SSI?
• Will social media giants and governments embrace or resist SSI?
• Will SSI play a role in activism by civil society organisations?
• What are the incentives and commercial models that will encourage SSI adoption?
• What kinds of governance structures need to be established for SSI?
The purpose of this Research Topic is to generate a rich resource for identity practitioners, researchers, technologists, potential adopters and many more to explore, understand, advance and enrich this subject.
Articles are starting to come out in this Frontiers research topic. (Kaliya is one of the guest editors)
Distributed Ledger Technologies, Value Accounting, and the Self Sovereign Identity
Review Technological activists are designing blockchains and other distributed ledger technologies to challenge extractive value-accounting and identity management in global capitalism.
An Accessible Interface Layer for Self-Sovereign Identity
Original Research The mechanisms and evolving standards collectively known as Self-Sovereign Identity (SSI) offer the prospect of a decentralised Internet by providing a central pillar for a Human-Centred Data Ecosystem (HCDE).
Exploring Value Propositions to Drive Self-Sovereign Identity Adoption
Original Research This paper presents research exploring the balancing of interactive friction and value proposition in the context of Self-Sovereign Identity (SSI) technology adoption. This work extends a related investigation of a full agency engagement with a
Development of a mobile, self-sovereign identity approach for facility birth registration in Kenya
Community Case Study Birth registration is a critical element of newborn care. Increasing the coverage of birth registration is an essential part of the strategy to improve newborn survival globally, and is central to achieving greater health, social, and economic equity
Blogs
2020 - How SSI went mainstream
The Sovrin Foundation (Chris Raczkowski and Drummond Reed) explains some recent history in SSI, how the foundation layed in 2020 prepared us for a global crisis, and how we got to this point where mass adoption seems immanent.
implementations that were launched in 2020 or are pending launch in early 2021 include:
IATA Travel Pass will be the first verifiable credential capable of providing proof of COVID-19 test and vaccination status at airports around the world,
NHS Staff Passport is the first portable digital identity credential for doctors and nurses in one of the largest public healthcare networks in the world,
GLEIF (the Global Legal Entity Identifier Foundation), based in Switzerland and the only global online source that provides open, standardized and high quality legal entity reference data, is committed to following the SSI model for digital identity credentials for companies.
SSI4DE, co-funded by the German Federal Ministry of Economic Affairs, supports showcases for secure digital identities in Germany, and Chancellor Angela Merkel declared digital identity as a priority matter during December 2020.
MemberPass brings SSI to financial services with Credit Union customer identity verification,
Farmer Connect is realizing is vision to “Humanize consumption through technology” by enabling and empowering individual coffee farmers to more easily work with global enterprises, and reducing costs and inefficiencies for large companies to work directly with small and often remote farmers.
Lumedic Exchange is the first network designed exclusively for patient-centric exchange of healthcare data using SSI-based verifiable credentials.
Tony Fish continues Data: Governance and Geopolitics
How data is governed can be thought of along several lines of activity: legislating privacy and data use, regulating content, using antitrust laws to dilute data monopolies, self-regulating by the tech giants, regulating digital trade, addressing intellectual property rights (IPR) infringement, assuring cybersecurity, and practicing cyber diplomacy. Of these, antitrust, regulation, and privacy are most immediately in the spotlight, and are the focus of this commentary, but it will also touch briefly on the connections with other issues.
Evernym writes: Why we support EFF
Privacy gets too little emphasis from some participants in the decentralized identity movement. They claim to value confidential interactions, yet advocate that individuals create public decentralized identifiers (DIDs) on the blockchain (ignoring legal warnings about DIDs being PII). They are okay with “phone home” verifications of credentials and revocation and capabilities.
Indicio Tech: Why we converted to a public benefit corporation
The idea of a benefit corporation begins with long-simmering dissatisfaction in the argument that the only responsibility or duty a company had was to increase its profits, a claim that had been forcefully made by University of Chicago economist Milton Friedman in the New York Times magazine in 1970.
Dark Matter Labs and IOTA foundation launch Persistent Selv
an exploratory demo app that leverages the possibilities opened up by self-sovereign digital identities (SSIDs) and data wallets, to help individuals plan their environmental legacy. Persistent Selv attempts to investigate possibilities for fostering individual long-term thinking, to make us aware of our interdependencies with the past and the future, understanding how our actions today might contribute to the legacies we are leaving behind to future generations.
Podcasts
Katryna Dow - Data minimisation: value, trust and obligation
Katryna talks to Oscar about her career (including inspiration from Minority Report), Meeco’s personal data & distributed ledger platform, the importance of data minimisation to inspire trust in organisations, and cultural differences in attitudes towards digital identity.
USPTO: CIO Jamie Holcombe
CIO Jamie Holcombe says identity verification with blockchain might be in the future for USPTO and talks about navigating changes in policy & law when considering a distributed ledger to store patents & trademarks. Among the interesting questions: do we start with patent #1 (applicant: George Washington)?
From the Twitter Collection
@michaelruminer tweets
V1.3.1 of the Verifiable Credentials Specification Map has been published
The release info and map URL at:
https://github.com/decentralized-identity/vc-spec-map/releases
@debimr75 shares
Now Animals too can have their own #decentralizedidentity to help them send their status updates to the rightful owner from their #IoT devices. #Decentralized #digitalidentity for #IoT devices would lead to #SmartFarming
@csuwildcat shares
As of Friday, we believe v1 of ION is functionally code complete, and the Sidetree Working Group at DIF (@DecentralizedID) should have a v1 spec candidate ready for the underlying protocol by Jan 21st. Public v1 launch of the ION network on Bitcoin mainnet is just weeks away.
WG Discussions
CCG Call about ZCaps and OCaps (minutes)
This week’s CCG teleconference had a great discussion about object capabilities
Alan Karp: I've been doing capabilities since I reinvented them in 1996 and I want to make sure we get it right, because when newbies start to use them there are plenty of mistakes that can be made
[...]
A capability or an OCAP is an unforgeable, transferable, permission to use the thing it designates ... it combines designation with authorization
TBL: Out to Remake the Digital World.
A story appeared in the NY Times about Tim Berners-Lee’s vision for the web and Solid-Inrupt that are working towards fulfilling it. The article included a quote from Kaliya, and has stirred up an active thread on the CCG mailing list.
Others say the Solid-Inrupt technology is only part of the answer. “There is lots of work outside Tim Berners-Lee’s project that will be vital to the vision,” said Kaliya Young, co-chair of the Internet Identity Workshop, whose members focus on digital identity.
Mr. Berners-Lee said that his team was not inventing its own identity system, and that anything that worked could plug into its technology.
Michael Herman asks CCG public mailing-list:
Byline: Tim Berners-Lee wants to put people in control of their personal data. He has technology and a start-up pursuing that goal. Can he succeed?
Has anyone else looked at this article?
Anyone familiar with TBL’s view of Decentralized Identity?
Is there anyone from the Solid project or Inrupt a member of CCG?
A solid discussion is underway, including this from Kayode Ezike
when I developed solid-vc, I was operating mostly under the threat model of compromised cryptographic keys used to sign credentials via jsonld-signatures and a compromised Solid password.*
I don't want to bombard you all with too much information about this project in this thread, but for now I will share the solid-vc repo again as well as my RWoT9 submission.
Are we doing enough to align our work with Zero Trust Architecture?
Adrian Gropper asks on Public DID-WG mailing list:
Please read
https://www.nytimes.com/2021/01/02/us/politics/russian-hacking-government.html
What would be a good way for our SSI communities to advance zero trust
architecture through more effective accountability and audit?
Could DIDs and VCs help with systems architected with Zero Trust in mind? Yeah, probably:
1) You could use VCs to prove that you should have certain levels of access to certain systems. Checking this could happen automatically, but while ensuring that you're "live" and not some bot.
2) Logs could be kept of which VCs were used when to receive the authority to do something.
3) ZCAPs could be used to provide fine-grained access to very specific resources, even behind the firewall, within an organizations systems.
DIDs could power much of this... but shouldn't promise any of it. The closest we could probably get to what you're asking, Adrian, is to align the Zero Trust Architecture principles to how DIDs and VCs can help -- primarily around: identity verification (VCs), login authentication (DIDs), least-privilege access (ZCAPs, Confidential Storage), and HTTP API access authorization (ZCAPs).
The most important message from the SolarWinds hack and much of the ransomware havoc is that our systems are not set up for individual accountability or independent audit.
The VC and ZCAPs perspective is inadequate. As an SSI community we need to address the separation of concerns between authentication, authorization, and audit as equally important and needing a harmonized best-practice perspective. Standardized EDVs are table stakes but not terribly relevant to the protocols that link authentication, authorization, and audit. Confidential Storage should be adopting the protocols that connect authentication, authorization, and audit rather than introducing protocols narrowly scoped to the narrow and obvious role of encryption at rest.
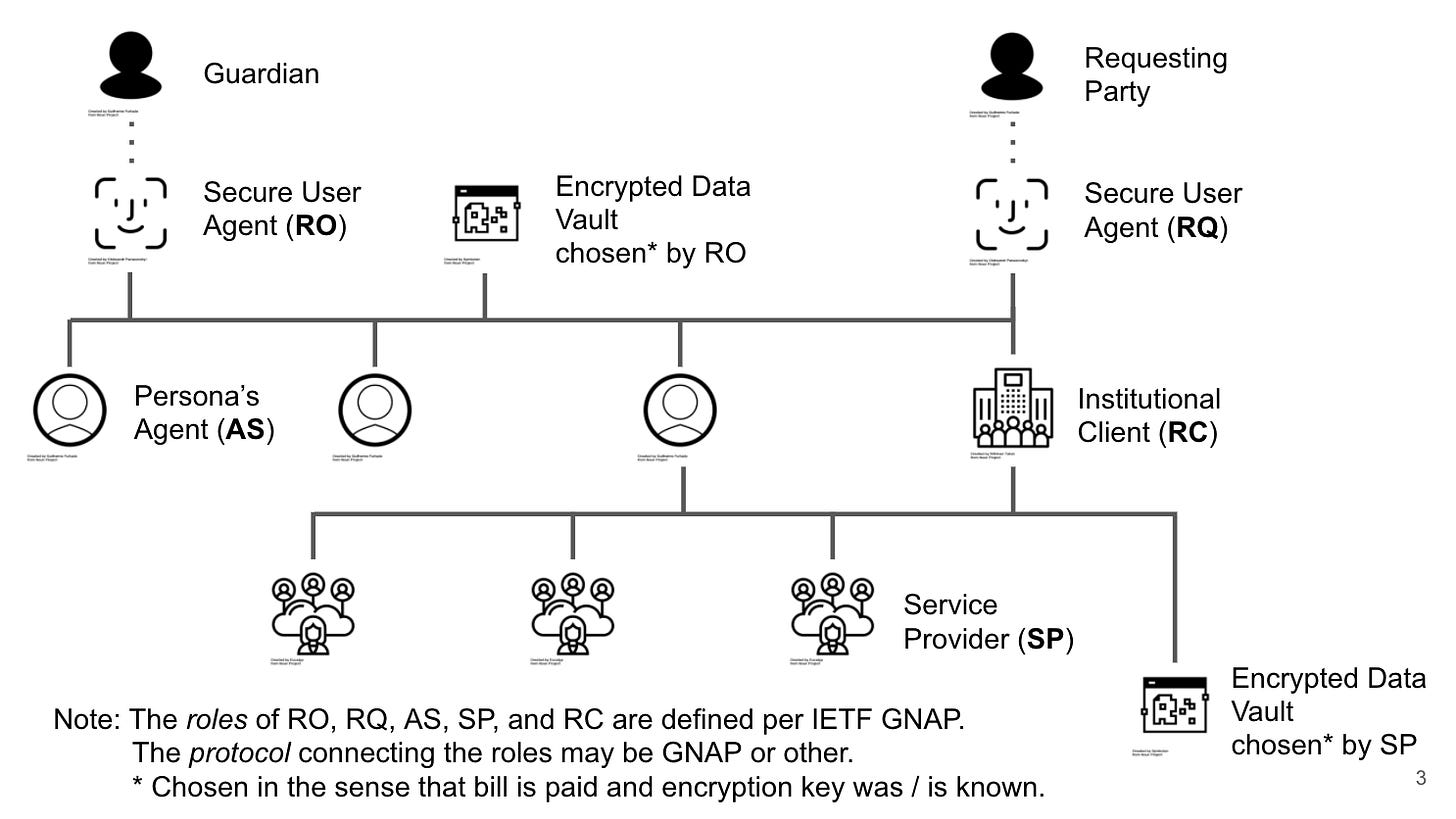
I've put together a few slides in an attempt to clarify the relationship between non-repudiable accountability and audits (and EDVs).
https://docs.google.com/presentation/d/1ksKal62ZiApX09Nejm4RSqHzHJbgwpu_l2Ho64_ePKU/edit#slide=id.p
Adrian follows up with some explanation of the slides
Considering risk mitigation, based on SSI principles, there are four separate actors:
Resource Owner (RO) their user agent (mobile wallet), and cloud agent (AS)
Service Provider (SP), by definition has data in the clear
Requesting Party (RQ) and their user agent (mobile wallet)
Requesting Client (RC), by definition has data in the clear
Beyond SSI
Digital Identity Isn’t Only For People
David Birch wrote in Forbes about a number of usecases for digital identity beyond personal identification
fintechs and regtechs looking for opportunities in the digital identity space should cast their ideas net pretty wide. Digital identities are not only for people and the future desperately needs digital identities for pretty much everything to underpin recognition, relationships and reputation (the 3Rs of the online economy).
Exostar Receives Kantara Initiative’s Identity Assurance Trust Framework Certification
Latest Recognition Further Demonstrates Company Protects Customers’ Identity and Personal Data by Complying with NIST 800-63 Standard
“This is a significant achievement and market differentiator for Exostar. The Kantara assessment and review process is rigorous and approval demonstrates a company’s care and respect for its customers.”