Identosphere Weekly #16 • Object Management RFI • Indicio integrations • Kiva National ID Case-Study
A weekly review of upcoming events, organizational announcements, standardization work and community blog posts in the Verifiable Credentials ecosystem.
Thanks for joining us for Identosphere’s Weekly: issue #16!
You can share\subscribe via newsletter.identosphere.net.
Thanks to our patrons for your support!
Upcoming Events
The Next Generation of digital identity: self-sovereign Identity
Wed, 17 February 2021 07:00 – 08:30 PST
This monthly webinar series is an opportunity to hear from UK experts in distributed identity and learn the mechanics of decentralized identity systems.
Sovrin open Board of Trustees Meeting
Wed, January 27, 2021 9:00 AM – 10:00 AM PST
This is an open meeting of the Sovrin's Board of Trustees. Come and ask any questions you might have or suggest direction.
Public presentation on the Disposable Self-sovereign Identity RFI
February 3, 2021 at 11:00 AM ET.
The Object Management Group is exploring potential issues and opportunities for standardization across the world of distributed ledger (DLT) and Blockchain ecosystems. [...] At this webinar we will present the insights we have gained so far on Disposable SSIDs and potential solutions, so we can communicate a clear sense of what we are trying to learn and the range of responses we are seeking. (More on this Below)
High Level
Good Articles for Beginners & Business Folks
How SSI Can Make Any Platform a 'Super App'
Verifiable Credential Issuers stand to make significant strides in user adoption by offering newfound convenience in a traditionally painfully inconvenient industry. Companies that support a Verifiable Credential Issuance standard can provide audited and truthful information to any third party on behalf of and with specific permission from their customers. For example, a bank could provide proof-of-funds in the form of a digitally verified credential document, that can then be used as a source of truth to instantly initiate a mortgage application, or a real estate purchase offer.
4 Keys to Self-sovereign Identity Adoption, Riley Hughes
I decided to interview close to 50 business leaders who are seeking to deploy SSI in production to glean their learnings. The interviewees included our “competitors” (at this stage we’re more collaborative than competitive), a few of Trinsic’s customers, and industry leaders. I have summarized and consolidated their insights and my own thoughts into 4 keys for SSI adoption.
The Implications of Bring Your Own Identity
Good little think piece by the Identity Defined Security Alliance
My short stint as “Mark Jannell” taught me a lot of about trust and ease of use in a bring your own identity model. Trust, as always in security, is essential to this new class of relationships and must be established and then protected from abuse. Ease of use, it turns out, is a key factor in protecting that trust and promoting the adoption of good identity patterns. I’m sure that I could have learned these lessons in some other way, but I’ll never forget my half year answering to a pseudonym.
Blockchain is the Least Interesting Thing About Self-sovereign Identity
Blast from the Past (well Fall) this is a piece by Riley Huges
as useful as blockchain is for SSI, it’s nowhere near as interesting as:
The impact on the internet
The benefits of technical standards
The economic opportunity for early innovators
Government
Data: Governance and Geopolitics
How data is governed can be thought of along several lines of activity: legislating privacy and data use, regulating content, using antitrust laws to dilute data monopolies, self-regulating by the tech giants, regulating digital trade, addressing intellectual property rights (IPR) infringement, assuring cybersecurity, and practicing cyber diplomacy. Of these, antitrust, regulation, and privacy are most immediately in the spotlight, and are the focus of this commentary, but it will also touch briefly on the connections with other issues.
Kiva Protocol, Built on Hyperledger Indy, Ursa and Aries, Powers Africa’s First Decentralized National ID system (CASE STUDY)
Since the launch of Kiva Protocol, Davie says global regulators have made significant progress in terms of how they are considering digital identity and eKYC verifications. He sees a global movement towards user-owned and -controlled data, better privacy, and more universal access.
[...]
As of today, Kiva is focusing on building additional ecosystem applications and services to make it easier for all stakeholders to access and use Kiva Protocol. Much of this is being contributed upstream into the Hyperledger Indy and Aires projects, with the remaining components hosted in Kiva’s repository.
Digital identity in the UK in 2021 with TrueProfile.io’s René Seifert (podcast)
In episode 37, René Seifert talks about the current status of identity in the UK; the government’s recent call for evidence and DIU (digital identity unit); the resultant six guiding principles – including privacy and inclusivity; the potential of self-sovereign identity to solve some of these issues; TrueProfile.io and the importance of verified credentials in an HR context; plus the ethical, political and technical challenges of ‘immunity passports’.
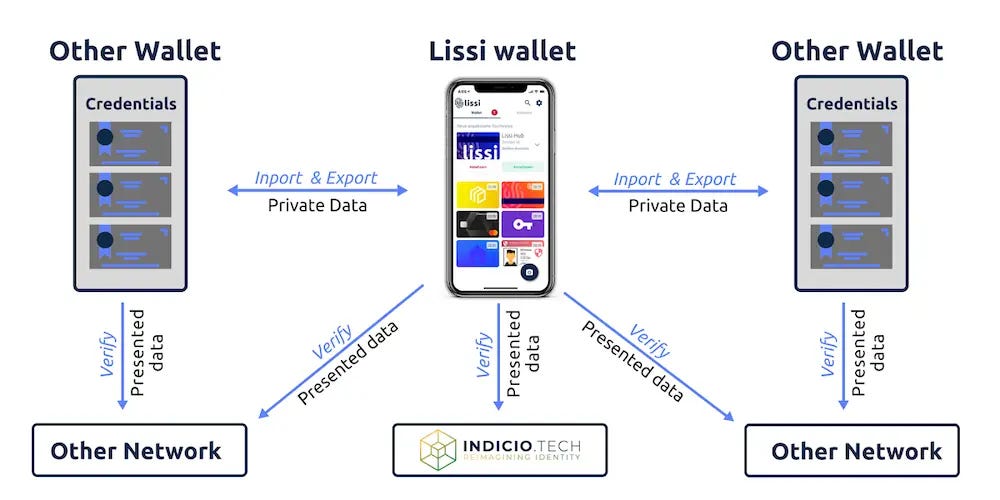
Indicio Network
The Lissi wallet supports the Indicio Network
we are committed to not only provide individuals with the choice of their favourite wallet, but also organisations with the choice of their network. We are delighted to announce that the latest version of the Lissi wallet also supports the Indicio Network.
Indicio.tech created the Indicio Network to meet the needs of companies and organizations that want a reliable and robust network to build, test, demo, and launch their identity solutions
GlobaliD connects to the Indicio Network
The Indicio Network will enable the issuance and verification of credentials on the GlobaliD platform and in the app, allowing individuals to port their credentials for authentication and authorization into any participating use case scenario — including vaccine passports.
Standardization Works
ION reaches 1.0
ION makes it possible to anchor tens of thousands of DID/DPKI operations on a target chain (in ION's case, Bitcoin) using a single on-chain transaction. The transactions are encoded with a hash that ION nodes use to fetch, store, and replicate the hash-associated DID operation batches via IPFS.
Jolocom’s latest contributions to DIF
Over the course of 2020, Jolocom added support for an off-chain element based on KERI. This is in addition to the Jolocom DID method (did:jolo and did:keri), which supports the Jolocom-Lib, our own SDK and the Jolocom SmartWallet.
Jolocom focused on the Rust KERI implementation
[...]
We at Jolocom strongly believe that DIDComm is a crucial infrastructure element for the broader and future-proof SSI stack, and current work on DIDComm v2 includes Jolocom’s implementation of the specification with authcrypt (authenticated encrypted) and most of the low level of the protocol.
Universal Wallet 2020 W3C Editor's Draft
This specification describes a portable, extensible, JSON-LD wallet representation, supporting digital currencies and credentials.
This editors draft was published January 18, 2021 (emphasis mine Infominer)
OASIS Open Establishes European Foundation to Advance Open Collaboration Opportunities
“The OASIS Open Europe Foundation gives us a unique opportunity to work with the European Union and EU Member States to advance open source and standards projects,”
OMG ISSUES RFI FOR DISPOSABLE SELF-SOVEREIGN IDENTITY STANDARD
This RFI aims to gain a better understanding of the self-sovereign identity space. In particular, the Blockchain PSIG is exploring the potential for standards setting in the area of contextually constrained or ‘disposable’ self-sovereign identity arrangements, building on top of existing W3C standards for self-sovereign identity [DID] and verifiable credentials [VC]. The aim of this RFI is to determine whether new standards for this specific aspect of self-sovereign identity are necessary, desirable and timely, and are not already being developed elsewhere. (The RFI)
A public presentation on the Disposable Self-sovereign Identity RFI will be held on February 3, 2021 at 11:00 AM ET.
The Object Management Group® (OMG®) is an international, open membership, not-for-profit technology standards consortium, founded in 1989. OMG standards are driven by vendors, end-users, academic institutions and government agencies. OMG Task Forces develop enterprise integration standards for a wide range of technologies and an even wider range of industries.
Thinking of DID? KERI On
The current generation of DIDs has introduced an innovative approach to digital identifiers, which has triggered the SSI movement. However, the inclusion of the method space in the DID syntax has led to fragmentation and weak security properties of the identifier type. These known method-space issues give the community impetus to redress them. In light of these innovative developments, now is the time to embrace KERI as an improved interoperable and secure solution for digital identity.
COVID-19
Microsoft joins coalition to accelerate the release of COVID-19 Vaccine Passports
VCI coalition members are working to enable digital access to vaccination records using the open, interoperable SMART Health Cards specification, based on W3C Verifiable Credential and HL7 FHIR standards. The VIC will enable individuals to obtain an encrypted digital copy of their immunization credentials to store in a digital wallet of their choice. Those without smartphones could receive paper printed with QR codes containing W3C verifiable credentials.
@maheshbalan shares
My presentation at the @Hyperledger Healthcare SIG about #VerifiableCredentials for Covid-19 - How a cryptographically secure digital credential can be used instead of paper documents. (Video)
Decentralized machine learning to respond to the health crisis
- CozyCloud (MyData)
The current health crisis has shown how essential it is to have data in order to make political decisions.
[...]We present here one of these solutions that allows training an AI with the data of many individuals without ever disclosing it to third parties, thanks to a decentralized protocol.
Paper of the Week
Self-Sovereign Identity for IoT environments: A Perspective
(On ARXIV) PGP, X.509, and SSI standards
We contrast existing approaches for identity on the Internet, such as cloud-based accounts and digital certificates, with SSI standards such as Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs). To the best of our knowledge, this is the first thorough comparison of these approaches. The benefits and challenges of using DIDs and VCs to identify and authenticate IoT devices and their respective users are discussed.
Beyond SSI
Toward new kinds of leverage, Doc Searls
Centralised thinking is easy. Control sits on one place, everything comes home, there is a hub, the corporate office is where all the decisions are made and it is a power game.
The Digital Identity Transformation – Podcast
Mike Vesey, CEO of IdRamp. As someone who has uniquely spent their full career immersed in enterprise identity, Vesey shares an insider perspective of how the industry has evolved during his tenure.
What Is ISO 27001:2013? A Guide for Businesses
ISO 27001 is also the cornerstone of a growing international consensus about data security best practices. Australia based its federal Digital Security Policy on ISO 27001. Likewise, ISO 27001 can provide guidance on how to meet the standards of other data privacy laws, such as the GDPR, which often direct companies to it as an example of universal best practices. So if you abide by ISO 27001’s recommendations, you’re on the right track for legal compliance, not to mention improved data security.
Ping vs. Okta: Top 3 Indicators That You’ll Get the Customer Satisfaction You Deserve
Some companies, like Ping, focus on being a long-term partner and are interested in understanding your identity and access management (IAM) challenges and implementing solutions to help improve your IAM journey. Others, like Okta, are interested in the short-term sale and may not always be there for you after the deal.
Thanks for Reading
In addition to the Identosphere Blogcatcher, this publication is also created using weekly Tweet Collections based on the following keyword searches #verifiablecredentials, #selfsovereignidentity, Self+Sovereign+Identity, Hyperledger+Aries, DIDComm, Key+Event+Receipt+Infrastructure, #ToIP, #TrustoverIP, w3c+Credentials.
Find this week’s collection here. Review previous tweet collections on decentralized-id.com.