One Year of Identosphere (#52) • Excelsior Pass Plus (International) • De-risking African Economies with LEI
Latest updates in decentralized identity: company news, explainers, standards updates, upcoming events and more!!!
This weekly newsletter is possible thanks to Patrons, like yourself.
It’s been a year since we began this weekly review. Incredible! We learned so much just to begin this publication and so much more, since then! Thanks for coming along for the ride!
Consider paying us a small amount each month via Patreaon
Support our work on Patreon — Get Exclusive Content!!
Read previous issues and Subscribe : newsletter.identosphere.net
Contact \ Content Submissions: newsletter [at] identosphere [dot] net
Coming Up
Connect:ID Conference • 10/5-6 Washington DC, Kaliya is speaking on Day 1 about Decentralized Identity.
Digital Trust World 2021 • 10/4-7 ‘the Conference for Authentication, Biometrics, Fraud & Security and Identity,’
Ceramic's Sovereign Data Hackathon • 10/7-21
Ceramic is live on mainnet 🚀👩🏽🚀🍾🥂 [...] a chance at over $10,000 in bounties.‘Identity Matters’: Meeco at IDNext ’21 • 10/11-12 • Katryna Dow will speak on day two, giving a session on the challenges ahead in the identity space.
Internet Identity Workshop 33 • 10/12-14
Authenticate Virtual Summit Recap and looking forward Authenticate 2021 • 10/18-20 • Fido Alliance
Global Assured Identity Networking POC Pre-launch “Listening Tour” OpenID
The objective of these sessions is to gather input for shaping the Community Group program targeted to launch in December of this year.
All are welcome and you can participate in any of the following upcoming forums:
1. OIX Trust Identity Conference 10/14 - on site/remote GAIN POC focused event on the 15th from 10am-12pm.
2. FIDO Authenticate Conference the following week. The hybrid GAIN POC session is in the planning stages for 21st of October.
Explainer
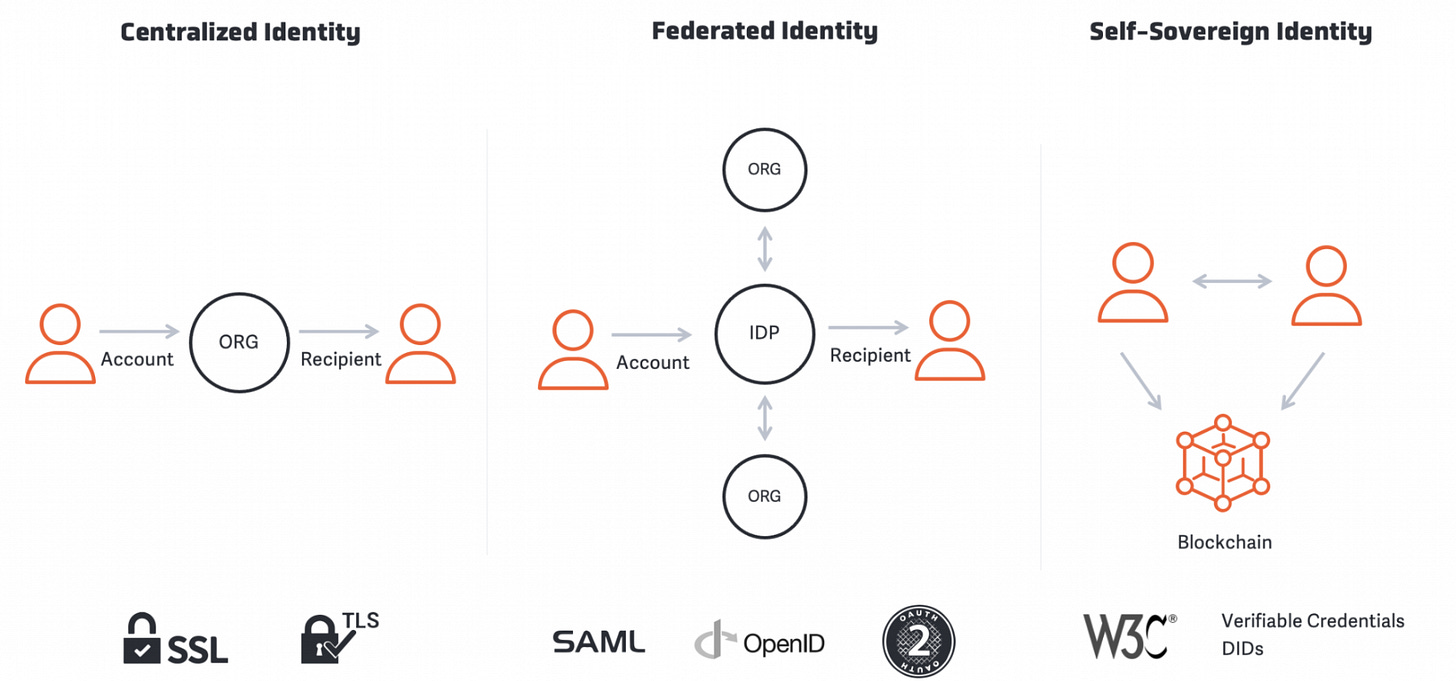
Self-Sovereign Identity Allows YOU to Control Your Personal Data Imageware
SSI supports credential leveling, including:
Authentication Assurance Levels (AAL) 1, 2 & 3
Biometrics to protect your data
Affirmation/Metadata
SSI credentials can be used:
In person or online
For government, financial, or high trust applications (document verification markets)
For asset ownership, decentralized finance (DeFi), and crypto markets
Company News
Jolocom goes Consulting
Our consultant focus is of course on decentralized digital identity (aka Self Sovereign Identity). Our advantage is that Jolocom has been able to build up enormous know-how through projects over the past 7 years. Not only was knowledge in the technology area built up, but also an extensive network through active work in committees (e.g. W3C, DIF, INATBA, ESIF / EBSI), associations (e.g. federal bloc) and consortia (e.g. shop window projects digital identities).
An Overview of Affinidi’s Terms of Use for Developers Affinidi
This article provides an overview of our Terms of Use for any developer who wants to use our APIs and SDKs.
Bringing Truth to Market with Trust Communities & Product Information Markets Mattereum
With product information markets enabled by Trust Communities, we can incentivize truth in markets by allowing experts to make money on their expertise and face consequences for erroneous claims. Simple concept, powerful implications.
State Recognized
Yann Desclercs from Cornerstone Advisory Plus speaks about countering the de-risking trend in African economies with the LEI GLEIF
African financial institutions are struggling to access international correspondent banking networks, either because they do not have the critical size required in terms of volume of activity, or, more importantly, because they are not always fully compliant with international AML and KYC standards and sanction regimes. As a result, the African financial system is widely perceived as high risk
Excelsior Pass Plus to be recognized out of state, internationally WGRZ
Excelsior Pass Plus will be compatible with the globally recognized SMART Health Cards Framework developed by VCI. VCI is a coalition of 570 public and private organizations including major health networks and Microsoft.
Decentralization
We need to talk about Self Sovereign Identity Olaf van Wijk
When we talk about SSI in relationship to the decentralization movement where bitcoin was the frontrunner, we talk about it in a similar manner as the original promise of nuclear energy. In this case not an abundance of cheap energy but the notion of self-control at the level the bitcoin ledger operates. But how would that look like?
Why decentralization matters CDixon
Decentralization is a commonly misunderstood concept. For example, it is sometimes said that the reason cryptonetwork advocates favor decentralization is to resist government censorship, or because of libertarian political views. These are not the main reasons decentralization is important.
Vaccine Logistics
Safeguarding COVID-19 Vaccines with SSI Frank Kottler
— Part 1/3
Defining the Future of IoT with Distributed Identity Management
— Part 2/3
Dylan realizes that the identified design requirements correspond to properties that are typically solved by means of cryptography. To embed cryptographic methods securely in their network, VirGo needs to identify both a network architecture and an identity management paradigm that fulfill the design principles when they interact.
— Part 3/3
Dylan has identified the requirements towards their IoT network and possible secure network architectures. Still, two challenges remain unsolved: the configuration effort required to setup device APIs and communication protocols, and the question of how to securely identify and authenticate the devices.
Papers
A Truly Self-Sovereign Identity System
we argue that without addressing privacy at the network level, SSI systems cannot deliver on this promise. In this paper we present the design and analysis of our solution TCID, created in collaboration with the Dutch government. TCID is a system consisting of a set of components that together satisfy seven functional requirements to guarantee the desirable system properties.
Determinants of Behavioral Intention to Use a Self-Sovereign Identity Digital Wallet: Extending the UTAUT with Trustworthiness ProQuest
The unified theory of acceptance and use of technology was extended to examine the potential influence of the self sovereign identity principles and trustworthyness, along with other factors such as percieved usefulness and perceived ease of use, on the adoption of this new approach to online identity
Not SSI
Surveillance Technology Me2B
As part of Bloomberg & NYC Media Lab’s Machines + Media 2021 virtual event, experts discussed the state of surveillance technology today, and the balance between keeping communities safe and protecting civil rights and liberties. Dr. Karina Alexanyan, consultant with the Me2B Alliance, described the Me2B Alliance’s approach to respectful technology at the 10 minute mark.
Identity
Our Ultimate Guide to Authentication: Types, Mechanisms, Forms, Protocols and More Ping Identity
When organizations employ authentication factors and protocols in a well-thought-out manner, users can still have excellent experiences while security administrators and auditors know operations are being executed securely. As we have seen, there are a number of ways to provide these services in any organization.
Trust Registry or Machine-Readable Governance? Indicio
Machine-readable governance is composed of elements that help to establish trust and enable interoperability: trusted participants, schemas (templates for structuring information in a credential), and rules and flows for presenting credentials and verifying them. Machine-readable governance can be hierarchical. Once a governance system is published, other organizations can adopt and then amend or extend the provided system.
Blockchain newsletter: Emerging coronavirus variants spur blockchain innovations in healthcare
Get a first look at the Gartner report for decentralized identity and verifiable claims. Access promising use cases, risks and considerations, and expert recommendations on creating value for a fully decentralized future.
Here’s your complimentary access to Gartner’s Innovation Insights.
Artificial Intelligence
Big Brother: A critique of the 4th Industrial Revolution Berkman Klien
China will remain an important partner for Africa. Nevertheless, it does not seem right that in the poorest continent on the planet, the most visible, public-led 4IR implementation is in security — and is simply a tool to maintain authoritarianism in many countries.
Responsible & Respectful AI Me2b
As part of the WaiACCELERATE USA 2021, Dr. Karina Alexanyan, consultant for Me2B Alliance, spoke about Responsible and Respectful AI. Me2B Alliance’s work specifically, is mentioned at around the 6-15 minute marks. The second speaker is Dr. Mona Sloane, Senior Research Scientist at the NYU Center for Responsible AI.
Thanks for Reading!
Read more \ Subscribe: newsletter.identosphere.net
Support this publication: patreon.com/identosphere
Contact \ Submission: newsletter [at] identosphere [dot] net