Summary 239 Aug 4-10: Just out NIST 800-64-4 !!! • IIW is now Oct 21-23 • VC Public Innovation Challenge •
The Weekly Round up of Decentralized and Self-Sovereign Identity News.
Thank you to all of you who filled out the poll. It is still live. It should only take about 5 min.
UpComing
*** DATE CHANGE *** Internet Identity Workshop, October 21-23, Mountain View California.
Credentials in Action: Public Innovation Challenge by CDPI in partnership with Red GEALC Sept 1 Deadline to Register.
To join the Innovation Challenge, teams must present a working prototype and a compelling, well-developed idea that demonstrates clear impact and innovation potential. You don’t need to have a polished product or full deployment plan, but your submission should show you’ve worked critically about the problem, the user, and how verifiable credentials can solve real challenges in the LAC region.
The challenge: Build open-source, user-centric solutions in:
- Cross-border credential portability: recognise identity or qualifications across countries.
- Climate credentials: unlock access to green finance or validate ESG efforts.
- Education & skills recognition: enable people to share learning and achievements globally.
- Or surprise us with your own idea!
Its great to see it finally live department:
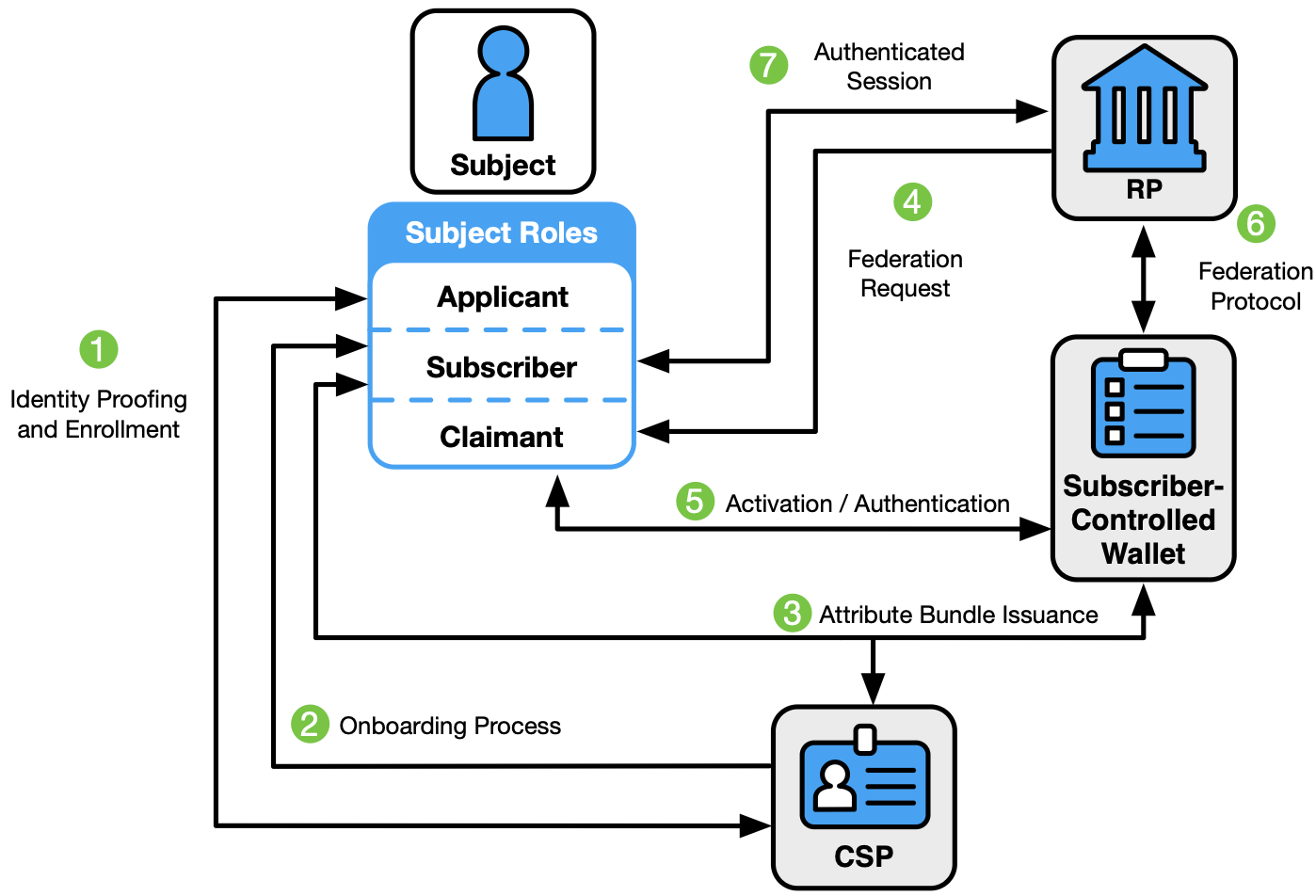
NIST 800-64-4 is Here!
These guidelines cover the identity proofing, authentication, and federation of users (e.g., employees, contractors, or private individuals) who interact with government information systems over networks. They define technical requirements in each of the areas of identity proofing, enrollment, authenticators, management processes, authentication protocols, federation, and related assertions. They also offer technical recommendations and other informative text as helpful suggestions. The guidelines are not intended to constrain the development or use of standards outside of this purpose.
Annotated Version with highlights for Definition, Error, Other important info, Recommendation, Reference (to external resource)
(Biometric Update) NIST finalizes first full Digital Identity Guidelines update since 2017
In addition to advice on how to integrate digital wallets and passkeys, the guidelines also provide new advice on setting context for risk management, measuring continuous evaluation and identity proofing processes, and adds controls to address identity fraud through the use of injection attacks to deliver deepfakes. They also more clearly define roles and types of identity proofing and emphasize the importance of providing alternatives to face biometrics in the process.
Helping Us Understand Each Other
From Babel to Bridge: Converging Digital Identity Across the Atlantic — Part 6: Reconciling Babel — Addressing Language Confusion Across Identity Frameworks (Etymology)
Despite the encouraging technical convergence, one obstacle remains in forging a unified trust layer: the bewildering array of terminology used by different identity communities.
By clarifying the lexicon, we enable a more precise discussion of technology fit and illuminate how seemingly different frameworks often address similar needs under the hood.
(T-Mobile) Digital Product Passport
Catena-X enables this shift by providing standardized DPP frameworks, partner access, and interoperable data exchange—making large-scale, cross-industry data collaboration possible beyond just batteries.
Humid Nights And Self Sovereign Dreams Executive Guide To Decentralize…
Centralized log-ins are sandcastles: one unexpected wave, and customer credentials scatter across oceans of breach alerts. Firms still cling. Yet every breach disclosure reveals the same flaw: storing identity in one place hands hackers an easy single target, auditors another penalty, and boards a migraine. distributed identity flips the model, letting users prove themselves via cryptographic tokens nobody hoards.
Research on European Wallets
Digital Identity Wallets: A Guide to the EU’s New Identity Model
Real Code
Issue and verify credentials using the Swiss Digital identity public beta, ASP.NET Core and .NET Aspire
Identity and AI Agent
The Future of Identity in a Deepfake World
The truth is, we’re building new infrastructure for reality itself, not just for what is true, but for who gets to be considered real. And the stakes couldn’t be higher. If identity becomes a lie we can all buy, then truth becomes a privilege only the verified can afford.
How to control non-human identities before they control us
Industry standards to manage NHIs are also being developed, McDaniel said. The Cloud Native Computing Foundation has the Secure Production Identity Framework for Everyone (SPIFFE) and its complementary standard the SPIFFE Runtime Environments (SPIRE), but McDaniel said they of course mainly apply to cloud environments.
The Internet Engineering Task Force has developed Workload Identity in Multi-System Environments (WISME), which should work for on-prem and hybrid environments, and there's also the Kubernetes-specific Kubelet.
(DIF) Scaling AI DIFferently: The Missing Growth Lever
The solution therefore isn’t more intelligent AI models, it’s a complimentary, verifiable identity layer. An identity layer doesn’t just enable trust at the level of individual users trusting individual interfaces; it also supports a healthier marketplace overall by making AI systems traceable, comparable to one another, and accountable to the users and services they interact with. It helps users in aggregate trust AI more in aggregate.
Operational Advantage Through Ethical AI
Human-Machine Teaming (HMT) is transforming the tempo and effectiveness of military operations. As AI and autonomous systems proliferate, HMT provides a pathway to harness these technologies while preserving human judgement, accountability, and ethical oversight. This article explores the components, challenges and strategic implications of HMT - and why it matters now more than ever.
Interesting Services
(Antonyms Labs) How to Get 9 “Second Phone Numbers” on One Device
But where MySudo differs from other services is that each of the 9 phone numbers sits within its own digital identity or persona called a Sudo, so you’re effectively running 9 separate identities or personas for any purpose you choose.
What is the story we tell?
Where Decentralized Identity Failed – And Where It Might Still Succeed
Decentralized identity promised to disrupt digital identity, but the private sector didn’t buy in. While businesses saw little value, governments recognized its potential for interoperability and secure services. From age verification to AI agents, this blog explores where decentralized identity fell short – and where it may still reshape the future.
DIF celebrates v1.0 release of did:webvh, with 3 complete implementations
If you’re hearing about did:webvh for the very first time here and now, let’s start at the beginning with a few high-level differences between did:web and did:webvh….
This method sought instead to achieve a superset of features already in production today, to offer existing DID-based and DID-like systems a beter option to migrate to or translate to.
Identity not SSI
(Auth0) FAPI 2.0: The Future of API Security for High-Stakes Customer Interactions
In this blog post, we introduce FAPI and its latest iteration, FAPI 2.0, highlighting how these standards can help organizations protect critical interactions, enhance data security, and deliver seamless customer experiences.
Getting a Better Understanding
Five Myths About JWTs Debunked
Myth 1: A JWT Is Just Another Name for a Token
Myth 2: JWT and Access Token Are Interchangeable Terms
Myth 3: JWTs Are Vulnerable Because Their Payload Is Readable
Myth 4: A Signature Makes a JWT Inherently Secure
Myth 5: JWTs Are a Modern Replacement for Sessions
Company News
(Ayanworks) [Video] CREDEBL | Open-source Platform for Decentralized Identity and Verifiable Credentials
Thoughtful
(Heather Flanagan) Not Just a Technical Problem: Why Fighting Disinformation needs resilient Infrastructure
And in almost every session, it became clear that the technical underpinnings of the Internet—especially in crisis and conflict settings—are being overlooked.
What I want is to build confidence in the systems we rely on to make decisions, especially in high-stakes environments.
* Digital infrastructure often isn’t designed to serve people in remote or underserved areas.
* Technical standards don’t always account for multilingual or multi-platform accessibility.
* Short-term, market-driven decisions prioritize scalability over long-term resilience.
Lifelogging under fascism: How self-tracking became self-incrimination
While quantified self involved quantitative data that was typically private and optimization-focused, lifelogging was its qualitative equivalent, typically public and sharing-focused.
But both movements feel different in 2025.
We have a choice when we build technology. We can take the easy way out and build something optimized for growth that doesn’t necessarily keep users safe — which, in turn, can be actively used against them in the hands of an adverse regime. Or we can build it to be truly user-first, with their well-being in mind.
Signs of Openness
Japan: Apple Must Lift Browser Engine Ban by December
This is directly relevant to Apple’s current iOS behavior, even under the EU’s Digital Markets Act, where technical and procedural restrictions continue to block meaningful competition. Japan’s guidance is clearly designed to avoid similar outcomes.”