Summary 240 Aug 10-17: Two DPI VC Challenges • Agentic AI in the Open Standards Community • Velocity Network News • ETSI and CEN standards in eIDAS
Thank you to all of you who filled out the poll. It is still live. It should only take about 5 min.
UpComing
MOSIP Decode 2025 - Registration Deadline August 20
Proving Identity in Provenance, by Content Authenticity Initiative, August 27, 12-12:45
Center for Digital Public Infrastructure presents Credentials in Action: Public Innovation Challenge Registration closes 1 September 2025.
Internet Identity Workshop Mountain View, October 21-23, 2025
Hiring
Decentralized Identity (DID) Specialist, Paris, France
Blockchain Developer, Ayan Works, Pune, India
Thoughtful
[Jon Shamah] The Ten Commandments of Digital Identity Wallets
[Tim Bouma] The Medieval Innovation We’ve Misunderstood: Credentials Were Always About the Records
[The Atlantic] The Facial-Recognition Sham: Surveillance won’t make the internet safer
Who Should Handle Your Digital ID?
The current answer is: whoever can afford to build a verification service and convince websites to use it. There's no standardized vetting of these companies. No requirements for specific security practices. No oversight of how they store or use your data.
We're essentially outsourcing national identity infrastructure to whoever shows up with an API and a sales deck.
(Doc Searls) A Cure for Corporate Addiction to Personal Data
Funding Open Source like public infrastructure
What begins as a volunteer effort often ends up being maintained by governments for the benefit of society. I suggested that Open Source would and should follow the same three-phase path.
AI and Identity
(Heather Flanagan) [IETF+] Agentic AI in the Open Standards Community: Standards Work or Just Hype?
This post is a snapshot of both: a look at where the “AI conversations” are happening in the standards world, and where the deeper technical groundwork is being laid, whether or not anyone’s calling it AI.
[Andor Keselman] Deck from GDC: Introduction / Overview of the Landscape of AI Agents and Identity
Black Hat 2025 Insights: Identity’s no longer an afterthought
We surveyed 110 attendees about their top concerns and challenges related to identity security, and their feedback provided a snapshot of the current landscape. we learned that AI creates opportunities and poses threats:
From chaos to control: Converging human and non-human identity management
Part of the reason why it’s so difficult to secure NHIs is that anyone can create them. Developers often provision NHIs when deploying new applications, and everyday employees can grant AI bots access to internal company systems and resources.
Access Control in the Era of AI Agents
How Authorization Mitigates Top AI Security Risks (OWASP LLM Top 10)
(Fastly) Trust at Scale with Fastly Image Optimizer and C2PA
We're solving this problem directly within Fastly Image Optimizer, our service that optimizes images as they pass through the Fastly network. Metadata preservation has proven to be a valuable addition to Fastly Image Optimizer, striving to balance the web performance benefits of only preserving what is absolutely necessary (to minimize file size) for some images. C2PA is the latest enhancement in our support for using metadata.
Company News and Opinion
(Spruce ID) [Opinion] Revolutionizing Supply Chain Transparency
Companies are embracing VDCs for three main reasons:
* Speed: Supplier verification shrinks from months to days, accelerating launches.
* Fraud prevention: Cryptographic verification blocks fake credentials and counterfeit products.
* Transparency: Real-time, verifiable records meet regulator and consumer demands for proof.
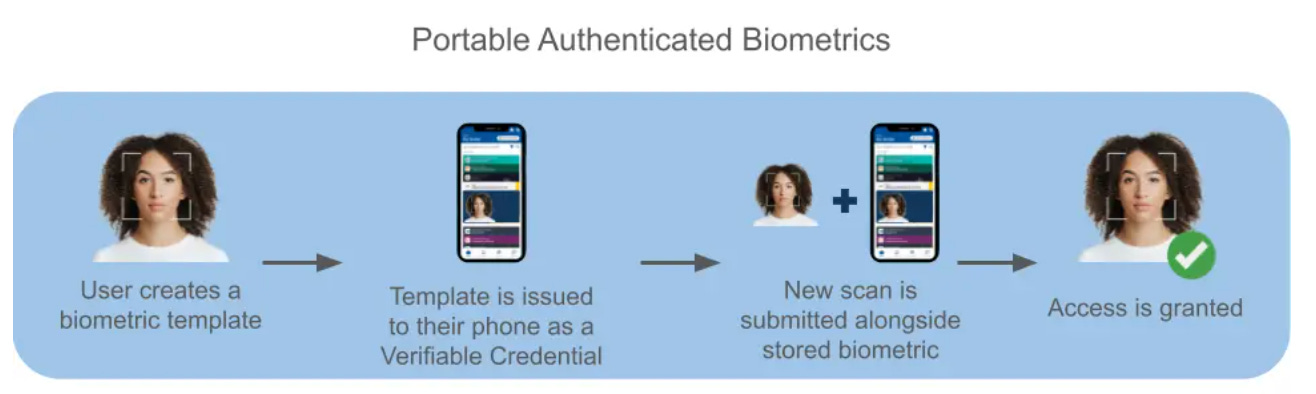
(Indicio) Portable Authenticated Biometrics 101
Velocity Network Foundation – MidYear Updates
Our current focus is increasing network density—bringing more value to all stakeholders across the labor market: employers, education providers, staffing firms, credentialing platforms, HR tech vendors, background screeners, lic1ensing bodies, state systems, AI models, and individuals.
Velocity Network Technology Becomes “Verii” Under the Linux Foundation’s LF Decentralized Trust Initiative
This move includes the Velocity wallet SDKs, registrar services, credential issuer and verifier agents, and payment tools, all of which will now be stewarded within the Linux Foundation’s globally respected, community-driven open-source framework.
Velocity Charitable Foundation Elevates Statewide Approach to Verifiable Credentials and Open Ecosystems
This effort centers on the deployment of the Velocity Network™—a global, standards-based protocol that empowers individuals to own and share their trusted career credentials—as a tool for enhancing state workforce strategy, while documenting Arkansas’s journey as a case example.
(IDNow) The Trust Playbook: 2026 ready strategies for identity, trust & growth
This playbook explores how forward-thinking organisations can turn today’s compliance chaos into tomorrow’s competitive edge. From eIDAS2 and the EU Digital Identity Wallet to the rise of AI, decentralised identity, and generative fraud, we unpack what’s changing and what to do about it.
Celebrating
Turing Space’s CEO Jeff Hu and CTO Henry Hang Named to Forbes 30 Under 30 Asia
Identity not SSI Reports
(Auth0) Customer Identity Trends Report 2025: Securing Customer Trust in the age of AI.
Drawing upon a global survey of 6,750 consumers and operational telemetry from the Auth0 platform, this report explores a number of themes that all pertain to trust — and how it can be built and maintained in a rapidly changing digital landscape. • Part one examines customer experiences and attitudes, primarily around identity, authentication methods, and customer journeys. • Part two shines a light on threats against customer identity, serving as a sobering reminder of the importance of strong security measures. • Part three goes where AI meets customer identity, uncovering important insights that may influence how organizations roll out AI agents.
NIST 800-63-4 Reactions
Dark Reading: NIST Digital Identity Guidelines Evolve with Threat Landscape
eIDAS
A new ETSI Technical Report, TR 119 479-2,
Outlining enhancements for the EU Digital Identity (EUDI) Wallet framework.
(IDnow) IDnow sets new standard as one of Europe’s first identity verification providers to meet latest eIDAS 2.0 regulations
With rising threats from deepfakes and increasingly sophisticated types of online fraud, especially in the finance, mobility, and telecom sectors, the ETSI 119 461 v2.1.1 standard outlines a comprehensive European framework for compliant identity verification services, including requirements for presentation attack detection, injection attack detection, and biometric-integrity assurance.
(IDnow) How ETSI and CEN standards are shaping the future of digital identity in Europe, one regulation at a time.
At the core of the transformation lie technical standards developed by the European Telecommunications Standards Institute (ETSI), the European Committee for Standardization (CEN), and the International Organization for Standardization (ISO). These are legally binding through Commission Implementing Regulations (CIRs), which lay the groundwork for secure, interoperable, and compliant digital identity services.
Decentralized Web
Holochain Horizon: Foundation Forward
We recently hosted what will be the first of many livestream events for everyone in our community, a series we’re calling Holochain Horizon (for those who want to go to the primary source, here’s a link to that conversation).
Research
Self-Sovereign Identity in Indonesia: Opportunities, Challenges, and Implications for Public Services
Self-Sovereign Identity (SSI) is a decentralized digital identity model that gives individuals greater control over their personal data, and this paper examines its potential integration into Indonesia's digital identity system (IKD) to enhance privacy, security, and public service efficiency. While SSI adoption could particularly benefit marginalized communities, the study identifies key challenges including infrastructure gaps, regulatory issues, and digital literacy disparities, ultimately proposing a localized strategy for implementing SSI within Indonesia's existing systems.